- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Internal/External Gateway User-id
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Internal/External Gateway User-id
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Internal/External Gateway User-id
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2023 06:51 AM
Dear Guys,
I try to configure my global protect portal to connect my clients through external or internal networks.
I configure my agent with internal detection and external parameters.
When i connect in the internal networks, the FW see me in the internal network but in the monitor tab i don't see the user-id with my private ip address.
When i connect to external gateway, the tunnel is up and i see the user-id with the private IP configure in the pool IP vpn gateway
All my security rules use the user-id.
My questions are:
Do i need to create 2 portals gateways ? one with external parameters, the 2nd with internal parameters ( for do this i can create one dns name with external or internal ip depending on the network access).
Or I can configure one agent with internal and external parameters to receive the user-id ?
I just want to receive the user-id for matching the security rules.
Thanks for your help
Nota: In the internal network i don't need/want use ipsec tunnel.
Regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2023 07:09 AM
Hi @SECRES .
No, you don't need to separate GP Portals.
Your internal users should still be able to connect to the GP Portal that is most probably hosted on your external interface.
It is really important how you have configured your Internal Gateway tab for the Portal agent client config.
Do you have second GP gateway applied on your internal interface with tunnel mode disabled?
It will be hard to identify what is the problem without looking at your actual configuration.
Can you provide the following:
Note: hide/blur any sensitive information as usernames, IPs FQDNs, etc.
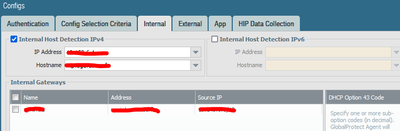
- GP Portal -> Agent -> Config -> Internal tab
- GP Gateway -> internal gateway
- Are you using explicit rule allowing internal users to reach internal GP gateway? Do you apply any security profiles on it? Or are you using the default intra-zone rule? Any sec profiles on it?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2023 07:52 AM
Hi, here after the screenshot for the agent configuration. For my test in the security rules, my ip adress have all access to internal gateway without user-id, but i want see my id in the monitor tab 🙂
Security rule
I don't know if my need is correct:
I just want :
- in my internal network, the gateway see me in internal, i don't need the ipsec tunnel but i want to see my user-id in the firewall for matching security rules
- in external, i used the same dns name and i connect to my external gateway and i retrieve the user-id and i match the security rule.
Thanks for your help
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-30-2023 07:24 AM
Make sure your Global Protect deployment is set for always-on. To obtain User-ID through GlobalProtect in an internal network, GlobalProtect must be deployed in user-logon or pre-logon mode and with internal gateways. GlobalProtect keeps the User-ID up to date by automatically re-authenticating the user every time there is a network status change on the endpoint.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Cm2uCAC
- 4221 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Name Normalization issue in GlobalProtect Discussions
- GlobalProtect Cert+SAML in GlobalProtect Discussions
- GP Login Lifetime? in GlobalProtect Discussions
- Global Protect Connectivity Issue in GlobalProtect Discussions
- Strange Gateway change issue on network with Prisma Access GP Client in GlobalProtect Discussions