- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Restrict GP gateway selection to specific user groups via panorama
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Re: Restrict GP gateway selection to specific user groups via panorama
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-13-2021 12:38 PM
Due to some internal department/company shuffling we have a requirement to authenticate a specific subset of our user base via ldap only, bypassing our existing SAML setup. Reading other forum posts and Palo docs I've learned that once you enable SAML on a gateway that's pretty much all you can use, so I'm looking at setting up a secondary gateway for these specific users.
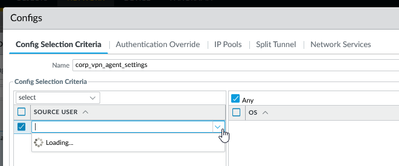
The issue I'm running into is that since Panorama is not able to directly query the Active Directory LDAP servers for group info I am unable to select any AD groups in the gateway agent configs section.
I was hopping that copy/pasting the entire ldap structure for the cn would allow it to show up properly on the managed firewall.
but that just shows up as a string on the actual firewall.
Does anyone have info on how to push this out through Panorama, or is this even possible?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-06-2021 10:59 AM
Following back up here, I was on the right path with the full LDAP string in the users section.
tl;dr use the full LDAP query in the user/group setting in GP and DON'T enter the AD domain name in the group mapping settings.
Panorama does not pull the user/group info from LDAP in the GP section so a copy/paste of the LDAP query has to be manually entered. This can be pulled from the Policies tab as MickBall suggested.
The piece that was tripping me up is that we are using SAML for authentication and the user group mapping that was setup prior to myself working in the system had a manually defined domain in the user domain field using the FQDN.
Turns out this was not allowing the firewall to properly match the user account to the group for non-policy mappings. So policies would work just fine, but GP portal and gateway mapping never worked. Removing the domain altogether allowed not only the proper groups to be matched but also enabled Panorma to pull in all of the groups from AD.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-14-2021 01:16 AM - edited 05-14-2021 02:55 AM
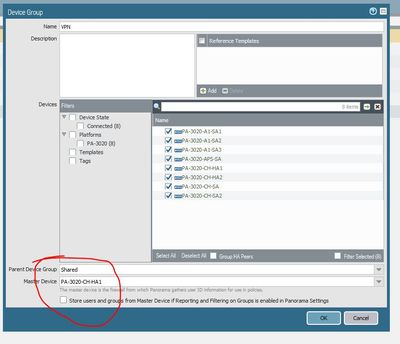
Have you not selected a master device in your device groups. or perhaps this does not work for gateways.
Or hows about you just copy the group name from a firewall and paste into Panaorama.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-14-2021 01:48 PM
We do have a master firewall set in Panorama and are currently pulling in groups for use in network policies. The system just does not appear to want to pull in the groups for GP settings.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-14-2021 11:59 PM - edited 05-15-2021 12:01 AM
OK i was not aware as only use panorama for objects and policies.
Would copy and paste from a policy not work... not ideal i know...
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-06-2021 10:59 AM
Following back up here, I was on the right path with the full LDAP string in the users section.
tl;dr use the full LDAP query in the user/group setting in GP and DON'T enter the AD domain name in the group mapping settings.
Panorama does not pull the user/group info from LDAP in the GP section so a copy/paste of the LDAP query has to be manually entered. This can be pulled from the Policies tab as MickBall suggested.
The piece that was tripping me up is that we are using SAML for authentication and the user group mapping that was setup prior to myself working in the system had a manually defined domain in the user domain field using the FQDN.
Turns out this was not allowing the firewall to properly match the user account to the group for non-policy mappings. So policies would work just fine, but GP portal and gateway mapping never worked. Removing the domain altogether allowed not only the proper groups to be matched but also enabled Panorma to pull in all of the groups from AD.
- 1 accepted solution
- 5484 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- service certificate push from panorama to managed firewalls eg: vpn in Panorama Discussions
- Admin GUI Login Fails on WAN Interface - Slow Load & "Single Sign-On" Error on PA-410 in Panorama Discussions
- Hardware firewall, cant find the CPU "data, and mgmt plane" logs in Next-Generation Firewall Discussions
- Panorama can't show specific timeframe log in Panorama Discussions
- Problems with Panorama Logs (e.g. Panorama shows logs from 2 years ago when we filtered for more recent dates and does not show the filter correctly). in Panorama Discussions