- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
February 2023 Rewind: LIVEcommunity Highlights
- LIVEcommunity
- Get Started
- News
- February 2023 Rewind: LIVEcommunity Highlights
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-28-2023 10:55 AM - edited 02-28-2023 10:56 AM
Welcome to our February 2023 Rewind, where we review some of LIVEcommunity’s biggest headlines from the past month!
In February, LIVEcommunity was busy sharing Palo Alto Networks’ Zero Trust OT Security announcement, an addition to our Member Testimonial series, playbooks for fighting cryptojacking, and more!
LIVEcommunity Member Testimonial: Steve Cantwell
Our new Member Testimonial video series invites community members from around the world to share their experience on LIVEcommunity, the importance of connecting with peers in cybersecurity, and what keeps them coming back. @S.Cantwell has been a member of LIVEcommunity since 2019 and part of community’s Cyber Elite program — which recognizes our most committed, helpful, and knowledgeable members — since it launched in 2020. He is an involved, responsive, and thoughtful member, and we’re grateful to have him as a part of LIVEcommunity: To date, he has made 745 posts, given 191 kudos and created 95 accepted solutions!
Introducing AI/ML Powered Industrial OT Security
XSOAR Marketplace: Keeping it Simple with Microsoft Teams via Webhook
The Cortex XSOAR integration with Microsoft Teams is fantastic, and includes a lot of useful functionality, but how do you schedule a message?
That question piqued my curiosity and a quick Google search gave me what was needed: Microsoft Teams supports messages via incoming webhook, and with Cortex XSOAR Bring Your Own Integration (BYOI) capabilities, it didn’t seem like an insurmountable challenge to write a simple integration that would simply send a message. Read on to learn how to send a message using Microsoft Teams, webhook, and XSOAR.
PANCast Is Looking for Episode Ideas!
PANCast, a Palo Alto Networks podcast that provides actionable insights to customers, is looking for ideas! PANCast provides actionable insights from cybersecurity experts to customers, helping ensure each day is more secure than the one before it.
Please share what topics you'd like to hear covered, simply by clicking "Suggest an idea" via this PANCast Ideas page. You can also listen to the latest PANCast episodes now.
How to Use Cortex XDR to Monitor Cryptojacking Malware
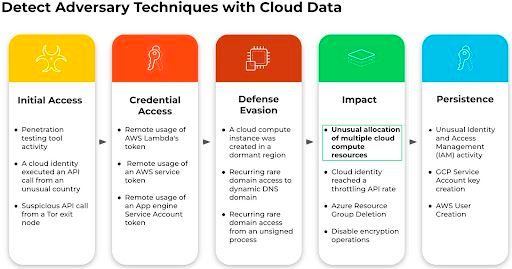
Cryptojacking — a form of cryptomining that uses unauthorized access to someone else's device and resources to mine for cryptocurrency — is officially a thing. These two blogs take a look at how Cortex can be used to combat cryptojacking malware:
TCP MSS Adjustments
The Maximum Transmission Unit (MTU) specifies the largest amount of data that can be transmitted by a protocol in one TCP segment. The larger it is, the less overhead you have but the more retransmits you'll get in case of a problem. The larger frame also means increased latency due to time necessary to transmit. The smaller it is, the more overhead you'll have but less to retransmit if there is a problem. Learn more about how to manage TCP MSS adjustments in this blog.
Cortex XSOAR: How to Archive Hosted Data for XSOAR 6
There are many benefits to being a hosted XSOAR customer, such as offloading the care and feeding of the XSOAR environment. That being the case, it does require a different process when the time comes to archive the data to prevent slow performance or running out of storage. Let's review how to archive and retrieve your data, including best practices, recommendations and FAQs for archiving.
Playbook of the Week: Speed Up Phishing Response with the Cortex XSOAR Deployment Wizard
Phishing is involved in almost 40% of security incidents, according to the 2022 Unit 42 Incident Response Threat Report. Attacks that once relied on poorly written phishing emails to find victims have rapidly increased in sophistication and targeting due to the growing amount of personal information easily found on the internet.
With Cortex XSOAR, phishing responses can easily be automated and it is one of the most popular use cases for automation. The Phishing pack helps organizations reduce the time spent managing phishing alerts and provides a standardized, methodical process to handle phishing.
TLP Update (2.0), Going Softer on AMBER and Adding AMBER+STRICT
The Traffic Light Protocol (TLP) can play a major role in your XSOAR instance. As you may have seen already, every Threat Intelligence Feed you can add will come with this option to be set. The traffic light protocol was first developed by first.org, a security professional community in the area of incident response but actually mainly CERT related.
As you may imagine, when CERT people come together they are keen on sharing knowledge and insights as well as the latest and most urgent events they are facing with each other. But how do you end up not over sharing information while publicly exposing that your company may or may not be affected by a certain threat actor or vulnerability? How can you make sure that your effort of investigating a certain threat gets public knowledge?
Autonomous Digital Experience Management Use-Cases
Over ninety-five percent of end users report experiencing unanticipated application downtime, which causes businesses to lose valuable productivity. Find and fix problems with the user experience using autonomous digital experience management, all before those problems have an effect on your company.
Feb ‘23 Discussion Highlight: Posts With Accepted Solutions
Nominated Discussions help LIVEcommunity Solutions Engineers highlight a discussion that has an Accepted Solution, and turn it into an article with additional helpful information, documentation, and clarity! Here are the Nominated Discussions we published this past month:
- Nominated Discussion: How to Change Forward Decrypt Trust Certificate
- Nominated Discussion: Delete All Address Objects
- Nominated Discussion: How to Add Risk Based Apps to a Custom Group
- Nominated Discussion: QoS Cleartext Match Issue
- Nominated Discussion: Palo Alto integration with Azure Sentinel
- Nominated Discussion: URL Filtering in TLS v1.3
Content From Our Cyber Elite Experts:
@Nikoolayy1 is a longtime Cyber Elite expert and wrote two posts for LIVEcommunity this past month! Nikolay is a Senior Cybersecurity Consultant who is responsible for the implementation of NGFW as the primary leader in Palo Alto firewalls, WAF systems, and DDOS/Bot protection technologies. He is an expert in Palo Alto Networks’ security solutions and his insights are well-worth a read:
You're now fully briefed on LIVEcommunity's February 2023 highlights!
If this was helpful, be sure to give this blog a thumbs up. See you next month!
- 3170 Views
- 0 comments
- 0 Likes
-
2.3 Network Integration
1 -
Alibaba Cloud
1 -
April
1 -
Azure
1 -
Best Practice Assessment
1 -
BPA
1 -
Certification
4 -
Community
5 -
community news
31 -
Community Updates
4 -
Cortex
1 -
Cortex Data Lake
1 -
Cortex XDR
1 -
Cortex XSOAR
1 -
Cyber Elite Program
1 -
cyberelite
8 -
events
2 -
Expedition
1 -
GlobalProtect
1 -
Google Chrome
1 -
Ignite '22
1 -
Ignite 2022
1 -
LIVEcommunity
12 -
member testimonials
1 -
Network Security
1 -
News
8 -
NGFW
6 -
PAN-OS
3 -
Panorama
1 -
Prisma Access
2 -
Prisma Cloud
1 -
Rewind
20 -
Skillets
1 -
Strata Logging Service
1 -
Tips & tricksm
1 -
Tips and Tricks
1 -
VM-Series on Azure
2 -
webinar
1 -
XSIAM
1
- Previous
- Next






