- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
AD Group Mapping - Azure SAML Auth
- LIVEcommunity
- Discussions
- Secure Access Service Edge
- Prisma Access Discussions
- Re: AD Group Mapping - Azure SAML Auth
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
AD Group Mapping - Azure SAML Auth
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2021 04:02 PM
Any documentation on how to setup AD Group Mapping when using Azure AD SAML instead of LDAP as the authentication source. I did configure the LDAP servers and am using the long-name in the group policies but the policies aren't mapping the user to the AD group as I'd expect.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-29-2021 02:37 PM
I be interested as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-05-2021 04:29 AM
You can see the article from Okta and use it for Azure AD, you just need to find the Azure AD documentation how to set the atributes:
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-14-2022 06:18 AM - edited 06-14-2022 06:19 AM
Hi There,
I arrived here to seek for answer to a problem that I could not find an answer to anywhere.
In fact, I still didn't find it but having access to lab, and some thought got me the desired result.
So what is it.
If you have setup a Security Web Policy based on LDAP Groups, and you authenticate using Kerberos/LDAP AD , PAN will identify you as domain\user.name
You have some influence over how domain\ will look, but overall PAN will identify the user and will know groups you are a memeber of.
Now, you want to introduce AzureAD SAML authentication.
You found the article and followed it to the letter: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g0000008U48CAE
You were able to authenticate, and get connected so what's the problem?
The problem is that your user name is no longer domain\user.name but now it is user.name@emailaddress.com , it is the account you have used to authenticate against Azure AD.
The user no longer matches any groups and the desired access for this user or group of users no longer works.
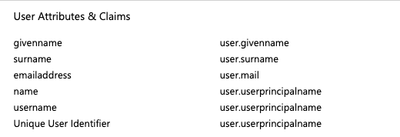
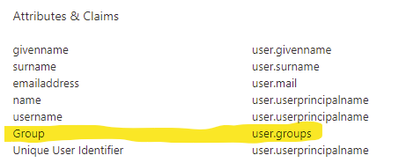
I found that the Attributes in the article do not contain group attribute.
Under AzureAD Portal for Single-Sign on I've added the attribute then for Security Groups
Its under "Add a Group Claim"
Source Attribute: GroupID
Customize the name of the group claim: Group
All these is case sensitive(apparently)
Once you have the extra attribute, export the XML and Import to Palo.
Import it as Authentication Profile and add Group attribute you created:
When I log in using SAML now, I have different view:
The User: shows the email address I used to authenticate.
The Primary User name is domain\user.name
Firewall can "match" the SAML account I used to the local AD.
Now, interesting part to some is the fact that I do not use Active Sync. My Local domain is entirely different to Azure AD. They are seperate.
I do have email attribute populated in my AD as the account I use with Azure though.
Hope this helps someone.
Cheers
Mariusz
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2022 08:30 AM
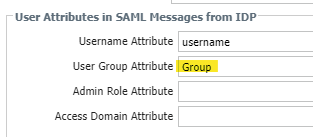
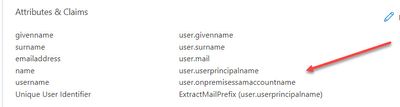
You do not need to add a group attribute, and it will not work for login control using groups. If you change the username attribute to match the settings below and have LDAP configured for userID Groups will work even for Prelogin. users will still login as before only the username submitted will be using local domain username format 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2022 10:52 AM
It does not affect prelogin as no user credentials have b been processed yet. A typo on my part
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-14-2022 03:37 AM
Hi , Have you tried this in LAB and or in your environment, is it working and are you able user AD groups also on PA
Sanha
- 18978 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access CIE and User-ID mapping not working for groups in Prisma Access Discussions
- The user information linked in the CIE does not match the match criteria in the GP's application settings. in Prisma Access Discussions
- Bidirectional User-id redistribution between Prisma access and on-prem Firewalls in Prisma Access Discussions
- Prisma Access with CIE in Prisma Access Discussions
- Using Cloud IDentity Engine to enforce group-based policies in Azure AD in Prisma Access Discussions