- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Dynamic IP List import now failed
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: Dynamic IP List import now failed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2018 07:04 AM
I just have the two default PA dynamic IP lists, but they each only have roughly 100 IPs. I would think there would be more than that but when I try to hit 'import now' it just fails. Anyone shed some light on how these two lists work and how often they are updated. And where can I verify that they have been being updated? I have active threat protection licenses.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2018 09:25 AM
Q: I can get a list of the IPs on the dynamic list by running these two commands from the cli:
request system external-list show type predefined-ip name panw-highrisk-ip-list
request system external-list show type predefined-ip name panw-known-ip-list
A: Yes, you can. You can also click on each list within the WebUI from Objects > External Dynamic Lists > List Entries and Exceptions to view list entries.
Q: is there a way to get a list of the URLs/IPS being blocked by the other PA policies?
A: If by "other PA policies" you are referring to URLs/IPs blocked by other features such as AV DNS signatures, etc there is no single aggregated list. Your best resource would be the Threat Vault @ https://threatvault.paloaltonetworks.com/
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2018 02:06 PM
The recommendation is to use EDL's in two separate rules.
One to cover connections going out to the bad IP's
One to cover connections coming from the bad IP's.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-09-2018 08:16 AM
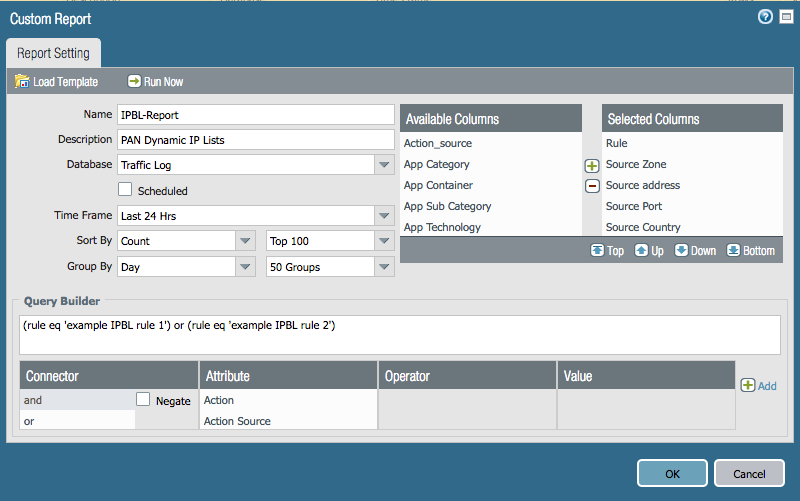
Assuming you will be doing this locally on your firewall (not Panorama) the steps are somewhat straightforward. There are several community articles and videos on the subject. Of course, you will also need to enable logging on the relevant security policy rules as well before you will have any log data to run reports against.
https://live.paloaltonetworks.com/t5/Tutorials/Getting-Started-Custom-Reports/ta-p/69951
https://live.paloaltonetworks.com/t5/Management-Articles/Create-a-Custom-Report/ta-p/55143
You'll want to build something similar to the example report below but you will need to play with it until you're capturing exactly what you'd like. Please be sure to include a query to match on the relevant security policy rules.
Here are the set commands from my example report:
set shared reports IPBL-Report type traffic sortby repeatcnt
set shared reports IPBL-Report type traffic group-by day-of-receive_time
set shared reports IPBL-Report type traffic aggregate-by [ rule from src sport srcloc to dst dport dstloc action ]
set shared reports IPBL-Report type traffic values repeatcnt
set shared reports IPBL-Report period last-24-hrs
set shared reports IPBL-Report topn 100
set shared reports IPBL-Report topm 50
set shared reports IPBL-Report caption IPBL-Report
set shared reports IPBL-Report query "(rule eq 'example IPBL rule 1') or (rule eq 'example IPBL rule 2')"
set shared reports IPBL-Report description "PAN Dynamic IP Lists"
And the XML:
reports {
IPBL-Report {
type {
traffic {
sortby repeatcnt;
group-by day-of-receive_time;
aggregate-by [ rule from src sport srcloc to dst dport dstloc action];
values repeatcnt;
}
}
period last-24-hrs;
topn 100;
topm 50;
caption IPBL-Report;
query "(rule eq 'example IPBL rule 1') or (rule eq 'example IPBL rule 2')";
description "PAN Dynamic IP Lists";
}
}
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2018 08:41 AM
Hello, the 'import now' failure for your pre-defined lists is an expected behavior. These lists are not updated through a manual import now action. The following can be found within the WebUI help pages of a PAN-OS device.
With an active Threat Prevention license, Palo Alto Networks® provides two Dynamic IP Lists: Palo Alto Networks - High risk IP addresses and Palo Alto Networks - Known malicious IP addresses. These feeds both contain malicious IP address entries, which you can use to block traffic from malicious hosts. The firewall receives daily updates for these feeds through antivirus content updates.
Please also note that you cannot edit, delete, or clone these predefined lists.
We carefully evaluate what IP addresses should be included on a daily basis. Due to the sharing and recycling of IP address, it is very hard to conclude that an IP address is malicious in all aspects. So for IP Blocklists, we only release those that have been manually verified. We believe these have achieved reasonably good coverage.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2018 08:43 AM
Thanks, so its safe to assume that the 100 or so IPs I currently have on that list is what PA currently believes to be malicious?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2018 08:49 AM
That is correct. Other coverage for malicious domains/IPs/URLs is provided in the form of Antivirus DNS signatures, Wildfire DNS signatures, as well as PAN-DB URL Filtering malware, phishing, and command-and-control categories.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2018 09:09 AM
I can get a list of the IPs on the dynamic list by running these two commands from the cli:
request system external-list show type predefined-ip name panw-highrisk-ip-list
request system external-list show type predefined-ip name panw-known-ip-list
is there a way to get a list of the URLs/IPS being blocked by the other PA policies?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2018 09:25 AM
Q: I can get a list of the IPs on the dynamic list by running these two commands from the cli:
request system external-list show type predefined-ip name panw-highrisk-ip-list
request system external-list show type predefined-ip name panw-known-ip-list
A: Yes, you can. You can also click on each list within the WebUI from Objects > External Dynamic Lists > List Entries and Exceptions to view list entries.
Q: is there a way to get a list of the URLs/IPS being blocked by the other PA policies?
A: If by "other PA policies" you are referring to URLs/IPs blocked by other features such as AV DNS signatures, etc there is no single aggregated list. Your best resource would be the Threat Vault @ https://threatvault.paloaltonetworks.com/
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2018 01:30 PM
I am looking for more information and found the following for DNS, this is good stuff.
1) The DNS list comes out daily and the IP lists come out daily - is there any overlap or is this IP list specifically only the things out there that do not have a DNS or Domain Name.
2) What are the High Risk IP Address List ? I see the note on the description is that just a IP addresses from other lists that are not in your Malicious list. I am trying to decide if it should be blocked. We will assume the Known Malicious IP Addresses are bad and block those.
Is there a good detailed list of links I can look at for DNS ( AV and Wildfire) as well as the IP lists?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-05-2018 01:44 PM
Hello, please see answers in line.
1) The DNS list comes out daily and the IP lists come out daily - is there any overlap or is this IP list specifically only the things out there that do not have a DNS or Domain Name.
A: There should not be overlap between DNS signatures and IP lists. DNS signatures are part of the daily Antivirus content releases. You can review a list of new Spyware DNS C2 signatures by reviewing the release notes either from your firewall via Device > Dynamic Updates > Antirivus > release notes or via our Threat Vault @ https://threatvault.paloaltonetworks.com. You may also access release notes from the Dynamic Updates section of https://support.paloaltonetworks.com.
2) What are the High Risk IP Address List ? I see the note on the description is that just a IP addresses from other lists that are not in your Malicious list. I am trying to decide if it should be blocked. We will assume the Known Malicious IP Addresses are bad and block those.
A: https://live.paloaltonetworks.com/t5/Featured-Articles/PAN-OS-8-0-IP-Block-List-Feeds/ta-p/129616
- Palo Alto Networks - High-risk IP addresses: This list includes IP addresses that have recently been featured in threat activity advisories distributed by high-trust organizations; however Palo Alto Networks does not have direct evidence of maliciousness.
Is there a good detailed list of links I can look at for DNS ( AV and Wildfire) as well as the IP lists?
A: I recommend using content (AV and Wildfire) release notes as well as our Threat Vault as previously mentioned. The IP lists can be viewed from your device using the commands previously discussed in this thread.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2018 01:53 PM - edited 02-07-2018 01:55 PM
Can someone tell me the best way to use these feeds from PA? Should I have a specifc outbound rule referrencing these lists as destination addresses and deny'ing all traffic outbond ?
Like so:
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2018 01:58 PM
Our recommendations are detailed in the PAN-OS 8.0 new feature guide.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2018 02:06 PM
The recommendation is to use EDL's in two separate rules.
One to cover connections going out to the bad IP's
One to cover connections coming from the bad IP's.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2018 02:10 PM - edited 02-07-2018 02:12 PM
Ok, so I add another rule and will end up with 2 rules:
1. trust to untrust w/those 2 lists as destination
2. untrust to trust w/those 2 lists as source
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-09-2018 07:08 AM
Next question, can someone help me create report to referrence these two policies? I just want to know if its getting hits and if so from where, how many, time, etc..
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-09-2018 08:16 AM
Assuming you will be doing this locally on your firewall (not Panorama) the steps are somewhat straightforward. There are several community articles and videos on the subject. Of course, you will also need to enable logging on the relevant security policy rules as well before you will have any log data to run reports against.
https://live.paloaltonetworks.com/t5/Tutorials/Getting-Started-Custom-Reports/ta-p/69951
https://live.paloaltonetworks.com/t5/Management-Articles/Create-a-Custom-Report/ta-p/55143
You'll want to build something similar to the example report below but you will need to play with it until you're capturing exactly what you'd like. Please be sure to include a query to match on the relevant security policy rules.
Here are the set commands from my example report:
set shared reports IPBL-Report type traffic sortby repeatcnt
set shared reports IPBL-Report type traffic group-by day-of-receive_time
set shared reports IPBL-Report type traffic aggregate-by [ rule from src sport srcloc to dst dport dstloc action ]
set shared reports IPBL-Report type traffic values repeatcnt
set shared reports IPBL-Report period last-24-hrs
set shared reports IPBL-Report topn 100
set shared reports IPBL-Report topm 50
set shared reports IPBL-Report caption IPBL-Report
set shared reports IPBL-Report query "(rule eq 'example IPBL rule 1') or (rule eq 'example IPBL rule 2')"
set shared reports IPBL-Report description "PAN Dynamic IP Lists"
And the XML:
reports {
IPBL-Report {
type {
traffic {
sortby repeatcnt;
group-by day-of-receive_time;
aggregate-by [ rule from src sport srcloc to dst dport dstloc action];
values repeatcnt;
}
}
period last-24-hrs;
topn 100;
topm 50;
caption IPBL-Report;
query "(rule eq 'example IPBL rule 1') or (rule eq 'example IPBL rule 2')";
description "PAN Dynamic IP Lists";
}
}
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2018 01:14 PM - edited 03-14-2018 01:27 PM
Thanks.
So I created the report locally on an HA pair that has the two rules configured and ran it for the past 24 hours but got 'No matching records.' So to test I sent some traffic to one of the IPs on the list and ran the report again and it worked:
Day Received Rule Source Zone Source address Source Host Name Source Port Source Country Destination Zone Destination address Destination Host Name Destination Country Destination Port Action Wed, Mar 14, 2018 outbound-PA-dynamic-BLOCK trust 10.102.20.55 ******* 0 10.0.0.0-10.255.255.255 untrust 183.81.171.242 183.81.171.242 Mongolia 0 deny
Thanks a ton bvandivier! One last question, where can I grab the XML of those reports so I can load into another PA?
- 3 accepted solutions
- 25695 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!