- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Configuration VM-Series on Azure cloud
- LIVEcommunity
- Discussions
- Network Security
- VM-Series in the Public Cloud
- Re: Configuration VM-Series on Azure cloud
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Configuration VM-Series on Azure cloud
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-05-2022 02:58 AM
Hello
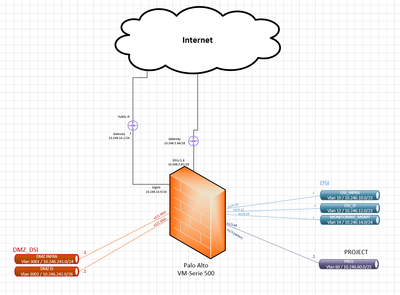
I'm deploying my first Palo Alto on Azure (I already deployed physical appliance) but I'm blocked.
I would like to deploy this type of design. The global network defined is 10.200.0.0/16 who are splitted in serverals sub-networks. I have one Untrust zone for Internet access and several zone for networks where we host our servers for IT needs, projects needs.. On Azure configuration during the VM deployment, the setup request to configure Untrust zone, Trust zone and Management zone. So I understand how to configure Untrust and Management zone and define the subnet attached for these zones, but for Trust zone, in my case, I don't see how to configure it.... I have no a dedicated Trust zone with a subnet dedicated..
Sorry if my question is stupid..
Jerome
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-09-2022 09:02 AM
Hello
No answer ? I would like to know in Azure how configure differents networks for each type of server (dmz, Web server, infra servers...).. Is-it better to create one vnet with several subnets inside the vnet? Or create one vnet per type of server (dmz, infra, Web servers) and create vnet peering ? And in both cases, can I create zone in Palo Alto for each type or it's not possible ? And how to configure for trafic goes via Palo Alto to Internet or to allow specific trafic between différents zone/vnet?
BR
BR
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2022 09:32 AM
Have a look at the Reference Architecture guide as well as the Deployment Guide for Azure, I think it will help you work through this scenario as well as understand the best practices for setting up in Azure.
https://www.paloaltonetworks.com/resources/reference-architectures/azure
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-11-2022 11:30 AM
It depends on your ultimate goal. Personally I usually deploy multiple vnets and that way the traffic between them can be forced through the vm series firewall, even if it it intrazone. Or you could still do it this way and have multiple interfaces zones. Putting all subnets within one vnet is the thing I would not do in this case.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-13-2022 02:02 PM
Hello
Thank you. I configured my architecture based on hub/spoke topology. I have à central zone (hub) where is deployed my FW. And I deployed spoke for each other "zone" such as DMZ or Project for project servers. From these zones, they will use corporate services such as AD, DNS, DHCP,... Is-it better to create a spoke name INFRA where AD,DNS,DHCP will be deployed? Or these servers are mutualized for all spokes and it's better to create a dedicated subnet under HUB ?
Regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-19-2022 06:42 AM
hard to say without knowing your environment, but what I've done in the past is to make the "spokes" separate vnets. Palo's in their own vnet with peering all the spoke vnets with this one, and using a LB sandwich on each side.
- 4054 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Palo vm-series cloudwatch plugin no metrics in VM-Series in the Public Cloud
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- Important Notice: Downgrade of Firewalls with Expired AIOps Premium Licenses in AIOps for NGFW Discussions
- Log forwarding from Cloud NGFW in Azure to Log Analytics Workspace for Sentinel in VM-Series in the Public Cloud
- SCM Essentials Questions in Strata Cloud Manager