- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to merge multiples confing to one config
- LIVEcommunity
- Tools
- Expedition
- Expedition Discussions
- How to merge multiples confing to one config
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-29-2021 06:54 PM
Hi community,
I need to know if is possible load multiple configuration to merge in one.
This is the scenario.
I have 3 Cisco ASA with different config, I need to migrate this 3 different (3 sites) ASA configuration to one PANOS config.
I proceed to create in my expedition 3 projects, one for each ASA firewall or site.
The question, exist one way to take this 3 configuration and merge in one PANOS ?
Thanks for your comment or suggestions
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-01-2021 10:24 AM
Again Thanks a lot for all your help !!!!!.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 07:55 AM
Hi @mss.support Yes, you could import all three of the Cisco ASA configs and merge them to a single base config in one project. If you already make three projects , you could export merged config and do load config partial command to load objects and policy one by one in the target firewall
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 08:17 AM
Hi Lychiang,
What is the process to load and merge the 3 configurations in one project ?
"If you already make three projects , you could export merged config and do load config partial command to load objects and policy one by one in the target firewall" ---- > In this case you are mentioned that is possible migrate each by each project and use the API to send the configuration separate to the PA firewall ?.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 09:58 AM - edited 04-30-2021 10:03 AM
Hi @mss.support ,
1 you will zip all three asa config into a zip file
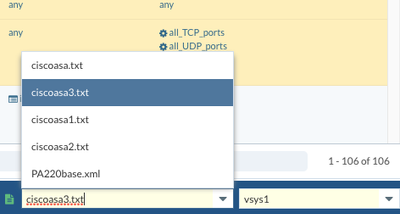
2. upload your asazip file in the import -> cisco -> upload multiple files
3. Upload your PAN-OS config under Import -> Palo Alto -> upload a single file. upload your base config here . it can be either firewal or panorma config depends where your policy going to be managed at.
4. You will need to fix all the red number showing in the dashboard for each of the cisco asa file , you can switch the context located at the right bottom corner to get to each of the ciscoasa config and make modification for each of the ciscoasa config
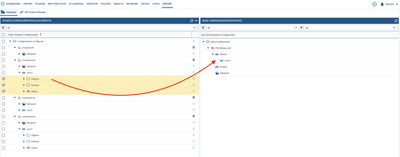
5. Since you are merging three ciscoasa firewall into one palo alto firewall, you will need to review which network interfaces you would like to migrate to the palo alto network, if there are not many interfaces, you can build the interfaces and zone on the firewall directly, please make sure the zone name needs to match the zone name in the policy. If there are a lot of interfaces you would like to keep from ciscoasa config, you will need to fix the interface configurations under each cisocasa config, make sure you rename each of the interfaces to PAN-OS naming conventions and each of the configs do not have duplicated interface names, also you might only need one VR depends on your use case. When you ready to merge the source and base configs, you can go to "Export" -> " Mapping" -> if you need to merge the network interface, you will first start with ciscoasa1 config, check all checkbox under "network", drag and drop them to "network" section onto the right side base config (If you already built interfaces and zone on the firewall, you do not need to merge the network configuration ) for policy and objects, under vsys1, drag and drop them to the right side vsys 1, continue for ciscoasa2 and ciscoas3
6. Once you finished drag and drop, you should see configuration from 3 ciscoasa moved to base config as below :
7. You can then click on "Merge" to merge the config
8. Once the merge is done, you can then click "Generate XML and set output" to download the merged xml file.
9 You could then load the config using "load config partial" or if you have direct access between expedition and firewall, you can then do an API calls from expedition to firewall to push the configuration over.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 11:04 AM
Hi Lychiang
First thanks a lot for the info and process load and merge in one config.
About interfaces,
Yes, In this case the asa configs have the following interfaces.
I have one config with the following interface config.
interface GigabitEthernet0/0
interface GigabitEthernet0/1 with 8 subinterfaces
interface GigabitEthernet0/2
interface GigabitEthernet0/3 with 9 subinterfaces
interface GigabitEthernet1/1
interface GigabitEthernet1/2
interface GigabitEthernet1/3
other with 3 subinterfaces
and other with one Gigaethernet with 4 subinterface and one gigaethernet.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 11:29 AM - edited 04-30-2021 11:30 AM
So if you need to keep those interfaces, you can click "remap interface" to remap them to PAN-OS naming convention. as long the interface name does not duplicate between three ciscoasa configs , you are able to merge without a problem.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 03:01 PM
Great,
Sorry, sorry last question,
I have this warning. I filter but I cannot see the PING object, or echo or ICMP. Do you know what is this.
Security RuleID [111] is using an object-group [PING] but both SourcePort and Service are filled. [access-list swift_access_in extended permit icmp host x.x.x.x x.x.x.x 255.255.255.254 object-group PING]
Security RuleID [352] is using an object-group [echo-trace] but both SourcePort and Service are filled. [access-list outside_in extended permit icmp object-group vlan101-mgmt-net x.x.x.x 255.255.255.0 object-group echo-trace]
Security RuleID [606] is using an object-group [PING] but both SourcePort and Service are filled. [access-list dmz-nyc_in extended permit icmp host x.x.x.x host x.x.x.x object-group PING]
Best Regards
Andres
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 03:11 PM
Hi
Related to interfaces, the vlans are different in all 3 asa configs.
In case in the asas use the same interfaces , for example. In two asa using the Gigaethernet0/1 but different vlans.
I was think remap that ,. for example.
In one site change the gigaethernet by ethernet1/1 with your subinterfaces. But with other asa remap with etherner1/3 with yours subinterfaces. That works ?
Again I really really appreciate your help with all your messages.
Best Regards
Andres
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-30-2021 03:57 PM - edited 04-30-2021 03:57 PM
For object-group PING , if you filter address group object contains “PING” you should find it
expedition only support remap to layer 3 interface , for vlan interface you will need to recreate the interface .
- 1 accepted solution
- 10367 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!