- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
App-ID for known services being blocked and not categorised as "ssl".
- LIVEcommunity
- Discussions
- General Topics
- Re: App-ID for known services being blocked and not categorised as "ssl".
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
App-ID for known services being blocked and not categorised as "ssl".
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2021 08:21 AM
Hello,
We have a Palo Alto running v9.0.9-h1 with an outbound to Internet rule which as follows:
From: Internal Networks
To: Internet External
Application: ssl
What we are trying to achieve is for the firewall to ensure that only SSL/TLS traffic is allowed outbound.
The issue is that that the firewall categorises well-known services such as Salesforce, LinkedIn, Office365 as specific App-IDs and thus blocks traffic and we are having to add each required application individually.
A potential workaround is to drop Application=ssl, and add Service=TCP:443 - But doing this we lose the layer 7 inspection and could allow a user to send HTTP over the 443 port which isn't ideal.
Is there a way to have the Palo categorise as ssl and then stop processing App-ID to get the best of both worlds?
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2021 09:02 AM - edited 09-10-2021 10:50 AM
From a security posture perspective, this is a bad idea. Attackers have C2 beacons regularly encrypted down SSL tunnels now. Writing a pervasive rule to allow anything that uses that underlying technology is a risk that enterprise networks should not assume. Verify first, trust second.
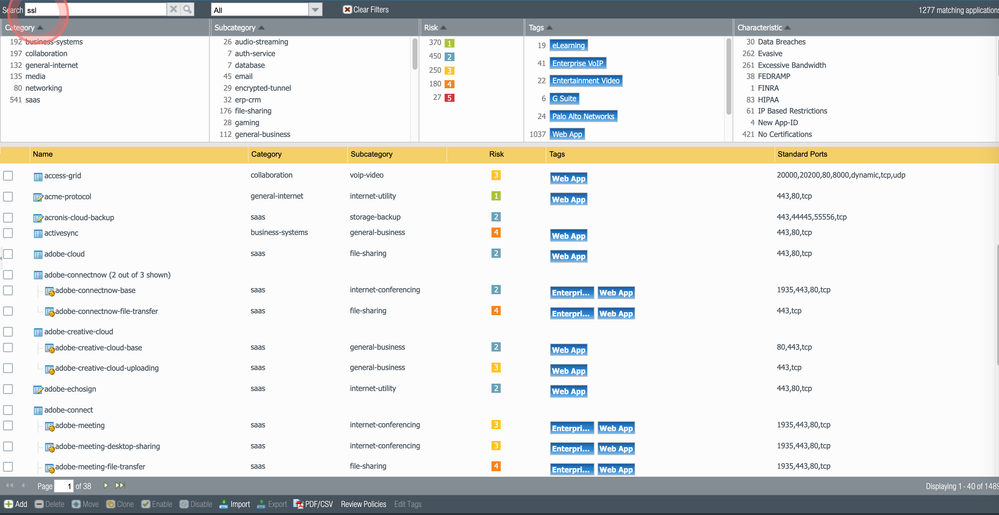
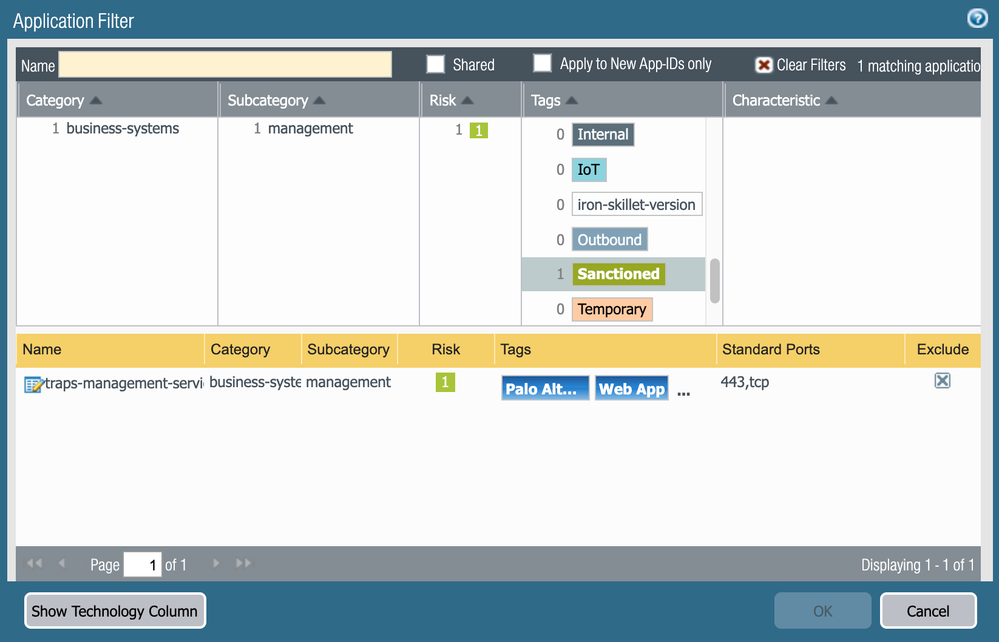
What you should do is go to the objects tab, search ssl and SSL in the searchbar. Of the applications that come up, edit the tags and add "sanctioned" to the ones you want.
After you have chosen your sanctioned applications, go down 2 menus of the objects tab and create a filter to allow all sanctioned apps.
Then you are able to write an outbound policy allow rule to all the filtered/sanctioned apps you wish.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2021 09:22 AM
Hi Slick, thanks for the response.
The issue we're having is for outbound Intenet browsing which this is, we don't know what applications are required until they are blocked, then requiring a support ticket, analysis and a firewall change. The turn around for this is 5 days minimum, that is significant impact.
The business is putting pressure on us to simply allow TCP:443 outbound in which case we lose all L7 capability.
Any further thoughts?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-10-2021 10:54 AM
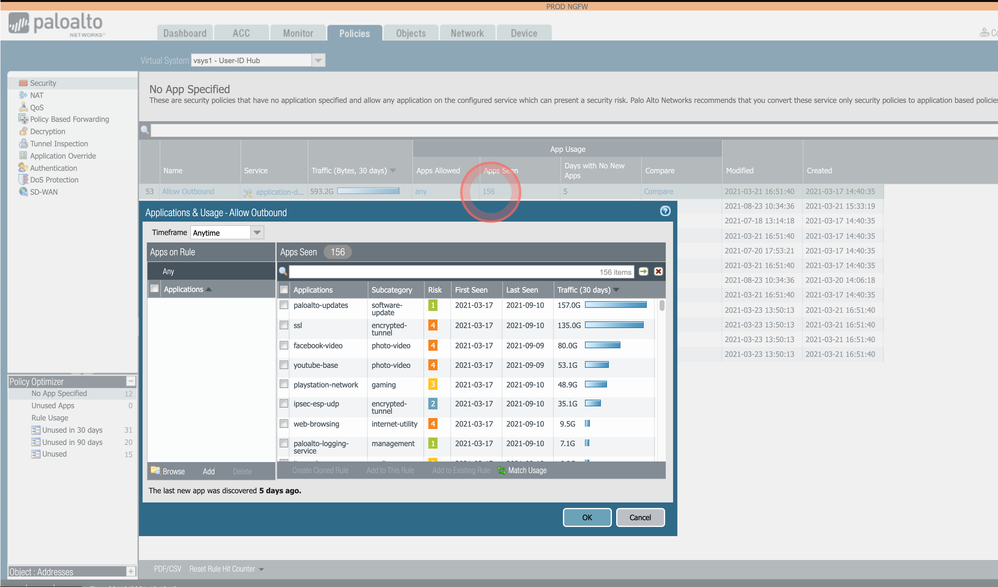
You could write a pervasive allow 443 rule but use it for only a few days, and then use the policy optimizer in the bottom left to see which apps touch the rule, and then click the checkbox to add them to a sanctioned rule as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2021 01:38 AM
While that sounds like something which we *could* do, that doesn't meet our needs.
To restate the requirement: We need to allow ALL SSL based applications by default outbound for Internet browsing but still have the firewall perform L7 inspection to ensure the traffic is actually SSL (like it would do for unknown SSL based applications).
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2021 10:53 AM
What you are asking for is not in the Palo Alto ethos. The product is built for positive enforcement, meaning there are no explicit allows. We found this to be too big a security risk, and for zero trust, most companies are moving toward a positive enforcement model.
So if you wrote a rule that was "allow any application from internal to external on any port" for a day or two, you could then use policy optimizer to restrict the function down to L7 policies because it would default allow, and then you could segment which traffic flows belong to which rule.
The L7 and content inspection is always happening, even on an allow all rule (as long as you attach a security profile group to the traffic), the APP-ID for the rule occurs as well.
But you're asking for something to be done that the industry is actively trying to move away from in which Palo pioneered. It's possible by doing the above.
- 5608 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- URL Category Change Request for www.intusjuntsparlament.com in General Topics
- Why do the same Windows Server data collected using XDRC and WEC agents show different statuses in the following fields? in Cortex XSIAM Discussions
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in General Topics
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in VirusTotal
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions