- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Bypassing "Packets dropped: forwarded to different zone" limitation
- LIVEcommunity
- Discussions
- General Topics
- Bypassing "Packets dropped: forwarded to different zone" limitation
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Bypassing "Packets dropped: forwarded to different zone" limitation
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2021 02:43 AM
Dear community!
I´d like to consult with you for a possible solution for this scenario:
We have 2 internet lines from two interfaces of the PAN firewall connected to two different routers. Each interface is in a different zone.
When incoming and returning packets follow different paths then we have an asymmetric routing condition. Situation similar to this one:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClReCAK
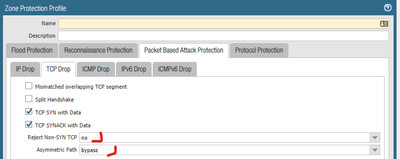
We configured the firewall to bypass the non-SYN-TCP check but we still have packets dropped with counter "Packets dropped: forwarded to different zone"
Having both external interfaces in the same zone fixes the issue but we´d like to have them in different zones.
A possible workaround could be using a PBF as in this article: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClF5CAK
But this is also not an option because the return mac entries supported is not big enough for all the incoming sessions, meaning the firewall will drop new sessions when table is full.
+ Is there a workaround to bypass the "Packets dropped: forwarded to different zone" counter and allow the firewall to forward s2c traffic to a different zone?
Thank you!
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-09-2021 05:31 AM - edited 11-09-2021 06:19 AM
Hi @Carracido ,
I saw the same behavior with an A/A HA-setup. Are you in the same setup ?
If so, have you considered changing the session setup options ?
For more info please check:
Hope this helps,
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-09-2021 06:30 PM
Hi @kiwi,
Thank you for the answer.
No we don´t have A/A HA-setup so that wouln´t be a solution for our scenario.
Cheers!
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-10-2021 04:59 AM
Hi @Carracido ,
You mentioned you have disabled the non-SYN TCP check, but did you set "assimetric path" to bypass?
Have you allowed assymetric path globally or per zone with zone protection profile?
I haven't faced a situation like this and I am working that is the actuall purpose of keeping the two ISP connection in different zones?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2021 01:18 AM
We tried allowing assymetric path both globally and per zone, still the same issue.
The purpose of keeping in different zones the two ISP connections is for having more granularity in the security policies.
Kind Regards.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-16-2021 01:47 AM
Hi @Carracido ,
What are you gaining from this granularity? Does the benefits you will gain deserve adding such complexity?
Don't get wrong - as I said I haven't work with such setup and I am insteresed in the motives and are there any other acceptable solutions.
I was hoping for the asymetric pass to do the trick...It is very unlickly, but are you applying any IP spoofing protection with the zone-protection profile?
- 7172 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Address Group and Tag limitations in General Topics
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- Do I need an edge router in front of my Palo Alto? in General Topics
- Limitations Observed with XQL Custom Widgets and Issue Visibility in Cortex XDR Discussions
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions