- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Captive Portal w/2FA in Azure
- LIVEcommunity
- Discussions
- General Topics
- Re: Captive Portal w/2FA in Azure
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-11-2021 06:21 AM
Hi All -
Hopefully I make this clear.
What I'm looking to do is set up Captive Portal with a push notification in Azure AD. I can't seem to find any documentation around this, can someone give me the general steps or point me to existing documentation?
Thanks in advance.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2021 04:13 AM
This should get you pretty close:
Set up GlobalProtect
Add the new captive portal to the portal agent configuration - Network > GlobalProtect > Portals > GP_Portal > Agent
Alias to point to VLAN 961 Example: server.mfa.company.com 10.10.10.10
Set up Azure
Basic SAML Configuration
Example
Identifier (Entity ID) https://server.mfa.company.com:6082/SAML20/SP
Reply URL (Assertion Consumer Service URL) https://server.mfa.company.com:6082/SAML20/SP/ACS
Federation Metadata XML Download
Set up Palo Alto:
SAML Identity Provider
Device > Server Profiles > SAML Identity Provider > Import
Authentication Profile
Device > Authentication Profile > Add
Type = SAML
IDP Server Profile = SAML Identity Provider created above
Username Attribute = username
Advanced Tab > Allow List = all
Authentication
Objects > Authentication > Add
Authentication Method = web-form
Authentication Profile = Authentication Profile created above
Policy
Policies > Authentication > Pre Rules > Add
Action Tab > Authentication Enforcement > Authentication Object created above
Let me know if you have any questions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2021 06:42 AM - edited 06-21-2021 06:44 AM
Thank you RobertShawver! I appreciate the help. When you mentioned adding new captive portal to portal agent configuration, where do i put that? Is that under the App tab of the portal agent configuration? My guess is under trusted MFA Gateways as described in Step 6, item 3, from the following document: Configure GlobalProtect to Facilitate Multi-Factor Authenti... (paloaltonetworks.com) Piecing things from different places.
Another question: server.mfa.company.com, does that have to externally resolve? The azureadminblog post seemed to indicate you only need internal, but someone told me it needs to be external for azure to talk to it.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2021 11:44 AM
"Is that under the App tab of the portal agent configuration?" - You got it.
"server.mfa.company.com, does that have to externally resolve? " - Mine does not, but your mileage may vary. I'd say try it internal first.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-22-2021 01:00 PM
@RobertShawver getting close, but not there yet. Browser based applications I get redirected over http to azure, but after trying to authenticate i get AADSTS700016 Application with identifier 'https://cp.domain.com:6082/saml20/sp' was not found in the directory... Also, not getting the notification from GlobalProtect when attempting non-browser based. Appreciate any help.
Thanks, Chris
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-23-2021 04:10 AM
Hey Chris -
I'll admit that troubleshooting without seeing your setup is a bit of a challenge.
Configure Multi-Factor Authentication (paloaltonetworks.com)
What I did was follow these instructions but with these caveats:
Step 2: Add a SAML IDP
Step 3: Skip this step (this is why it took me so long to get this going, it took me awhile to figure out that I needed to skip step 3.)
I suspect you may have the same issue as I seem to remember that error you spoke about.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2021 06:51 AM
Hi Robert,
Glad to know that document still applies. I did skip step 3 and was thinking hmm... maybe this isn't possible. Still getting the error, but I have two tickets in with support and hopefully at least one of them can help me figure that out.
Thanks to your help, I finally got the GlobalProtect Protected Resource message to pop up that I've been trying to trigger. I have a couple of test auth rules.
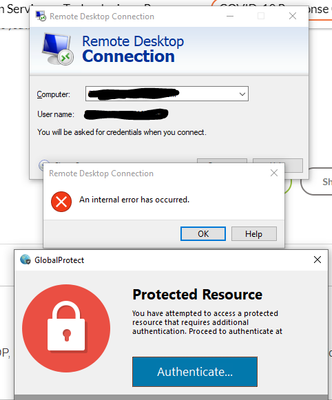
The one i triggered the GlobalProtect message was for RDP session to specific host. When I try to connect I get "An internal error has occurred" Remote Desktop Connection dialog box. Then the GlobalProtect message that has the authentication button which takes me to captive portal in browser window and i get the AADSTS700016 message (which I expect at this point).
Question for you: Are you using this to control RDP sessions? The "An internal error has occurred" has me concerned that it may not work if the session times out before it can authenticate.
Another question: How do you get https to trigger authentication, do you have to have ssl decryption in place?
I greatly appreciate your help!
Thanks,
Chris
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2021 06:15 AM - edited 07-01-2021 06:19 AM
Hey -
Sorry it took me so long to respond. We are doing it for RDP, but it's kind of a hokey process. If I try to RDP to a box that would have me crossing the CP, I also get the "An internal error has occurred", but I also get the GlobalProtect "Protected Resource" "Authenticate" popup (see screenshot). I click on Authenticate and that takes me to the Captive Portal where I authenticate. From there I go back to RDP and login again and it works because I am now authenticated via the CP.
It's hokey, but it makes sense in my head. I can't RDP to a box that I need to authenticate via captive portal to first. After that I can RDP to it without authenticating again for like two hours (I believe there is a timeout setting).
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-01-2021 06:33 AM - edited 07-12-2021 05:12 AM
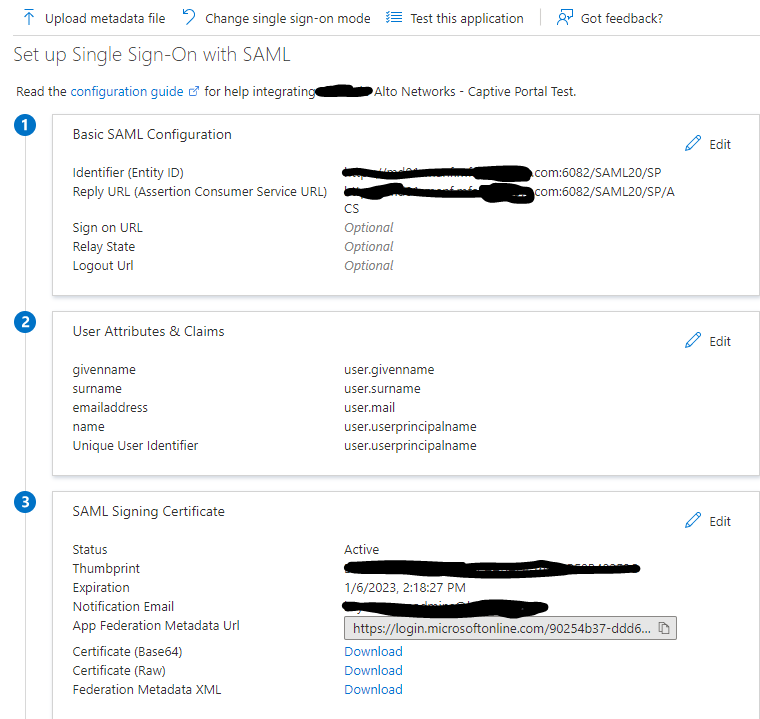
Don't know if this will help or not, but here is my Azure setup:
I think what's important to note here is the port addition:
Entity ID:
https://your_address.com:6082/SAML20/SP
Reply URL:
https://your_address.com:6082/SAML20/SP/ACS
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2021 08:10 AM
Hi Robert,
That is good to know that you see the same behavior, but it works. I was seeing the exact error, getting the Protected Resource message and then clicked authenticate. I think last I tried it I still had the Azure error, so I don't think I was authenticating. We resolved the Azure error just before I went on vacation, but have been unable to do further testing since. Thank you so much for confirming that you are able to do the RDP.
Sites that are https: do they work for you with captive portal? we don't have ssl decryption in place, so I'm wondering if that is the cause. The block-continue response pages don't show up for us for https sites but they do for http, which i think is due to us not having ssl decryption in place. I have read that if you have decryption you need to do ssl decryption forward proxy for it to work. I'm just wondering if you had problems with https sites. I'm just wondering what your experience has been with https sites.
Thank you so much for your help!
Chris
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-09-2021 08:22 AM
Thank you again Robert,
You are amazing! I think we got the Azure error resolved before i went on vacation, but this will be great to compare a working config with what we have.
Latest question that came up: Since the GlobalProtect client does enforcement for non-http/https traffic, what happens if a computer don't have the GlobalProtect Client or it is disabled? We want to make sure that the resources are still protected.
Thank you so much,
Chris
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-12-2021 05:00 AM
Hey Chris -
Awesome! I'm glad to hear you are making good strides. I'll hit you up on the side to compare working configs.
I'll have to think about the enforcement for non-http/https traffic. Since we mainly use for RDP access I haven't given it much thought. I could easily be wrong here (TBH, I'm really a noob at this), but what we protect with the setup you and I both have is "on the network". That being said, I would think that if a computer doesn't have the GlobalProtect Client or it is disabled you wouldn't be "on the network" and as such wouldn't be able to access those things. If that makes sense.
- 16415 Views
- 25 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA Global Protect in GlobalProtect Discussions
- CIE for user/group mapping for firewall on-premise in General Topics
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- Panorama managed - Global protect SAML cert renew - IDP xml import wrong expiry in GlobalProtect Discussions
- Android & iOS devices are bypassing the captive portal in Next-Generation Firewall Discussions