- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Creating a duplicate network?
- LIVEcommunity
- Discussions
- General Topics
- Re: Creating a duplicate network?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2018 01:01 PM - edited 03-19-2018 01:17 PM
Hi folks,
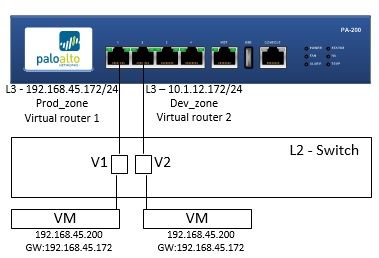
I am being asked to create a duplicate network that will service VM clones of production VMs for testing and development purposes (without changing their IP or anything else). We have something similar at a different site using "transit" zones and individual NAT rules (that I did not configure), but this task is a bit different from that.
I need a L3 interface to represent this duplicate network, to eventually communicate to the internet.
I am trying this small test first.
Is there a way to NAT the IP of devices (and maybe gateway IP) to communicate to a unique L3 interface on the firewall?
I assume separate zones and virtual routers will keep the traffic separate, looking for suggestions for the NAT rules to accomplish.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2018 01:54 PM
This may be possible by creating multiple VSYS and then a transit zone, but I would be really careful with having the same IP subnets on the same firewall in the same VSYS. We ran into an issue where we had the same public facing network on outside multiple interfaces and ran into an issue where bi-directional NAT feature did not work as it would randomly chose to start advertising the MAC address on an interface that did not have rules for that particular NATed IP. We had to then create both inbound and outbound NAT rules. Not even sure how this would look or what potential issues you could run into.
In our case we have a separate firewall for sandbox testing.
- Matt
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2018 01:54 PM
This may be possible by creating multiple VSYS and then a transit zone, but I would be really careful with having the same IP subnets on the same firewall in the same VSYS. We ran into an issue where we had the same public facing network on outside multiple interfaces and ran into an issue where bi-directional NAT feature did not work as it would randomly chose to start advertising the MAC address on an interface that did not have rules for that particular NATed IP. We had to then create both inbound and outbound NAT rules. Not even sure how this would look or what potential issues you could run into.
In our case we have a separate firewall for sandbox testing.
- Matt
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-20-2018 06:09 AM
I would say that the only way to properly do this is by having multiple VSYS as already mentioned by @mlinsemier. That would allow you to keep the traffic fully seperated and only allow inter-VSYS communications exactly where needed. This also ensures that you can build out security policies for your test/dev enviroment that will never apply to your production traffic until you actually role out to production.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-20-2018 12:46 PM
Thank you guys for the feedback. I just created my first transit network (without a new vsys).
But still need to configure it in a more specific way.
I am in process of that and researching creating a new vsys. Will report back, update, and close this week.
- 1 accepted solution
- 3637 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- Investigate Bandwidth utilization on Palo Alto Firewall in Next-Generation Firewall Discussions
- Devices pinging only after clearing ARP table in General Topics
- Welcome to the General Topics Discussions! in General Topics
- Welcome to the Custom Signatures Discussions! in Custom Signatures