- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Firewall bypass due to Java/Python FTP Injections
- LIVEcommunity
- Discussions
- General Topics
- Re: Firewall bypass due to Java/Python FTP Injections
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-28-2017 01:47 AM
Hi. Reading the article below on firewall bypass I was wondering if Palo Alto Networks by default blocks active FTP connections.
http://blog.blindspotsecurity.com/2017/02/advisory-javapython-ftp-injections.html
That would mitigate the threat. Anyone an idea?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2017 09:16 PM - edited 03-01-2017 09:16 PM
content 667 was released:
Notes:
Palo Alto Networks has released a content update to add coverage for FTP Java/Python FTP Injection vulnerability as discussed in the security advisory [1]. Customers are advised to upgrade all devices to Content Apps and Threats Version 667-3876 or later and review policies to ensure desired actions are configured on all security policies. References [1] - http://blog.blindspotsecurity.com/2017/02/advisory-javapython-ftp-injections.html
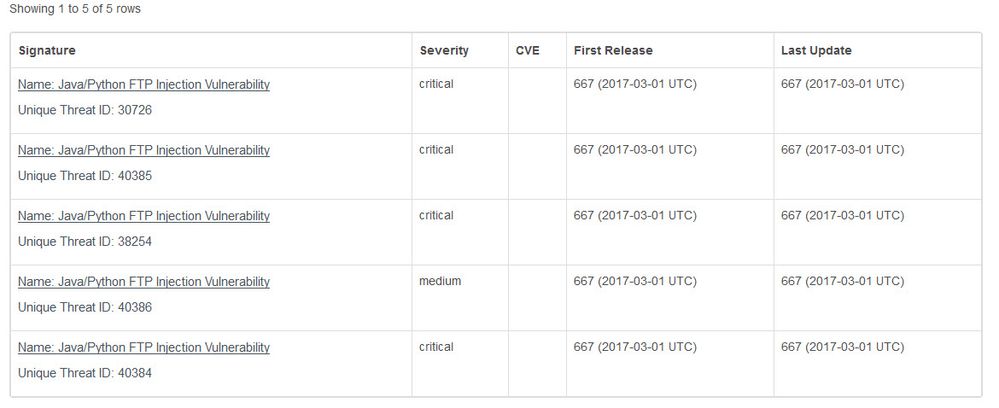
I can find FIVE "Java/Python FTP Injection Vulnerability" vulnerability signatures in it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2017 10:50 PM - edited 03-01-2017 10:51 PM
I check in PANW Threat Vault has update Content Apps and Threats Version 667-3876 for FTP Java/Python FTP Injection vulnerability already. Thank you for information.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-28-2017 05:40 AM
If you don't have a security policy that would allow FTP sessions into your network then it would be blocked, if you for some reason have any 'any any' rule from your trust to untrust then the session would be allowed.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2017 09:07 PM
Yes i understand about we can blocking with don't use allow FTP in security policy but if someone want to use policy ftp for allow FTP service to untrust or any zone. I think firewall should have a FTP Injections signature to protect this vulnerability.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2017 09:16 PM - edited 03-01-2017 09:16 PM
content 667 was released:
Notes:
Palo Alto Networks has released a content update to add coverage for FTP Java/Python FTP Injection vulnerability as discussed in the security advisory [1]. Customers are advised to upgrade all devices to Content Apps and Threats Version 667-3876 or later and review policies to ensure desired actions are configured on all security policies. References [1] - http://blog.blindspotsecurity.com/2017/02/advisory-javapython-ftp-injections.html
I can find FIVE "Java/Python FTP Injection Vulnerability" vulnerability signatures in it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2017 10:50 PM - edited 03-01-2017 10:51 PM
I check in PANW Threat Vault has update Content Apps and Threats Version 667-3876 for FTP Java/Python FTP Injection vulnerability already. Thank you for information.
- 2 accepted solutions
- 5534 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Text injection issue on firewall in Advanced Threat Prevention Discussions
- Service object injected from Panorama, local view on firewall says destination port [ object Object ]. in Panorama Discussions
- Firewall bypass due to Java/Python FTP Injections in General Topics
- FTP Protocol Injection Bypass Palo Alto Firewall in General Topics