- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Free wildfire
- LIVEcommunity
- Discussions
- General Topics
- Re: Free wildfire
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Free wildfire
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2015 01:15 PM
I thought there was a limited version of wildfire that you could use for PE files. But it isn't working, I do a test registration and it fails. Is there something that is missing in the instruction that I have
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2015 08:08 AM
SSL decrypt does not require a license.
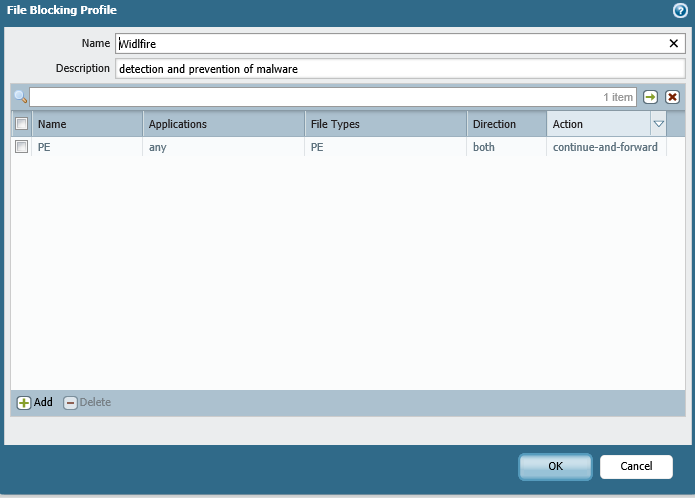
can you post your FileBlocking profile config and show where's applied to the security policy?
Then, as others have request, show us the traffic monitor for the file download session in question.
This type of configuration is something we do on a regular basis for hungreds of clients.
c
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2015 09:24 AM
I looked at the statistics throught the CLI while running the test and got this
error counters
FWD_ERR_CONN_FAIL
Number of times an attempt to establish an SSL tunnel between the device and the WildFire cloud has failed. A connection is either immediately retried or attempted at a 1 minute interval, depending on the function being performed.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-11-2015 09:28 PM
Is the contral plane apble to communicate to the WF cloud, do you have a rule or service route that lets the approprite App-ID off of your network?
Easy way to check is the enable logging on Interzone rule and see if the traffic is being dropped.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2015 01:08 AM
Hi jprovine
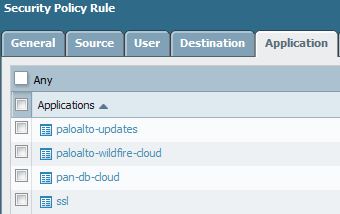
you'll want to have a security policy that allows ssl and paloalto-wildfire-cloud out to the internet from the management interface without security profiles (or you might recapture that same executable)
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2015 05:13 AM
@ethiSEC and @reaper are both correct but in my opinion issues arise sooner in the workflow. If there was just a rule missing we would still be able to see "Forward" action in the Data Filtering log. According to @jdprovine Data filtering log is empty.
Can you try this in the CLI:
test security-policy-match from srcZone to dstZone source srcIP destination dstIP protocol 6 destination-port 80
Enter the srcZone, dstZone, srcIP and dstIP for the session in which you download the test file.
Output will be the security rule that was used for accessing the test file. Then make sure the File Blocking profile you pasted earlier is applied to that rule.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2015 07:48 AM
That is the first time anyone has mentioned the need for a security policy to allow access to the wildfire in the cloud. So how was it able to register?
Test wildfire
Testing cloud server ca-s1.wildfire.paloaltonetworks.com ...
wildfire registration: successful
download server list: successful
select the best server: us-west-1.wildfire.paloaltonetworks.com
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2015 10:22 AM
TAC remoted in and identified updated the destination zone in order to allow it access to the internet. So my next question is can you only put it on security policies that have access to the outside/untrust/internet zone?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2015 10:27 AM
You should be able to apply it to any security policy, I have it setup this way so it scans between my VPN users zone and my 'trust' zone. Only the management interface, or the interface as defined by your services used for the PAN to communicate with the wildfire cloud, need to be allowed to the untrusted (internet) zone.
Hope this makes sense.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2015 06:03 AM
So the security policy doesn't necessarily have to have direct access to the internet. So how do I configure it to -
interface as defined by your services used for the PAN to communicate with the wildfire cloud, need to be allowed to the untrusted (internet) zone.?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2015 09:33 AM
So in my case, I have the services use the management port. So I have a policy to that allows the management port to get out to the internet for specific applications and URL's.
I hope this makes sense. Feel free to message me privatly if you would like additional info.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2015 10:56 AM
so you created a security policies just for these functions? It seems like you should be able to it without that, that isn't a part of the instruction that TAC provided
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2015 11:00 AM
If you allow all outbound traffic, then correct you wouldnt need a specific rule. We tighten down our outbound access as well so we have a special policy just for the PAN to reach out to the internet and then we lock down what it can get to, source, destination, applications, etc.
However you can search your logs for those particular applications and/or URL's to see if your PAN is reaching out to the cloud.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-21-2015 12:26 PM
setting security policies may not always be an option in which case a service route may help solve the issue, by binding the source interface of a specific service to the external dataplane interface instead of the management interface
PANgurus - Strata specialist; config reviews, policy optimization
- 15258 Views
- 52 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Forensics free trial license expired in Cortex XDR Discussions
- False Positive (GitButler) in Cortex XDR Discussions
- WildFire auto update agent failed to download Wildfire version 865169-869036 in General Topics
- Setup > Management > Cortex Data Lake > Cortex Data Lake Status > Show Status in AIOps for NGFW Discussions
- Error while uploading file to wildfire sandbox in Cortex XSOAR Discussions