- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
FTP passive mode issue
- LIVEcommunity
- Discussions
- General Topics
- Re: FTP passive mode issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
FTP passive mode issue
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-03-2015 01:59 AM
Hello All,
I was read somewhere on this forum similar article from October 2014, and seem that problem with passive ftp was on new content ID. However some time passed since, I have issue with ftp passive mode on my VM-100 (panos 6.0.5, content ver. 483-2549..).
I catch traffic with pcap on pan directly (all stages) and noticed that had drop stage. From traffic log everything goes well (3way handshake, authentication, change directory, ftp commnds..). But since PASV request from client, server respond with entering into passive mode with port xxxx, client send syn sequence to offered port xxxx and never establish connection, with dropped packets from FW for that connection and port.
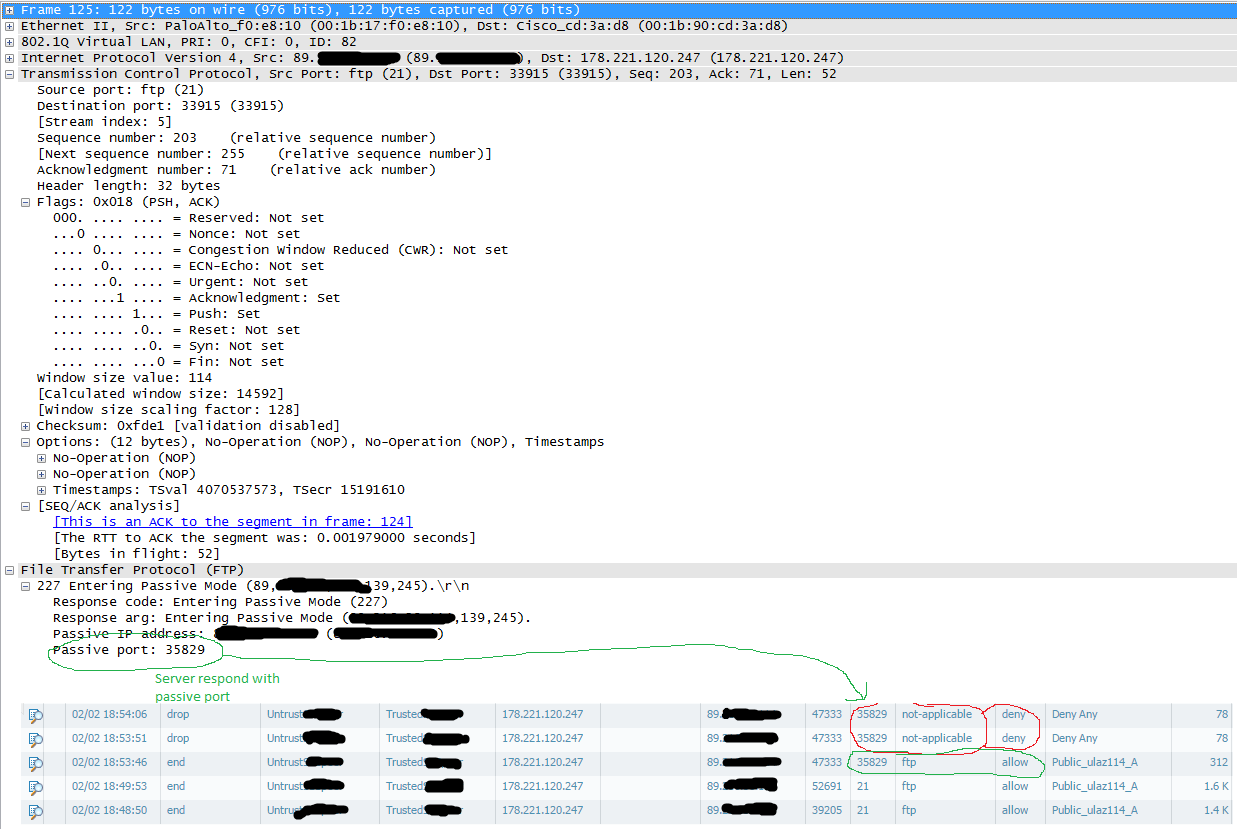
Forward stage on firewall pcap with traffic log for that connection
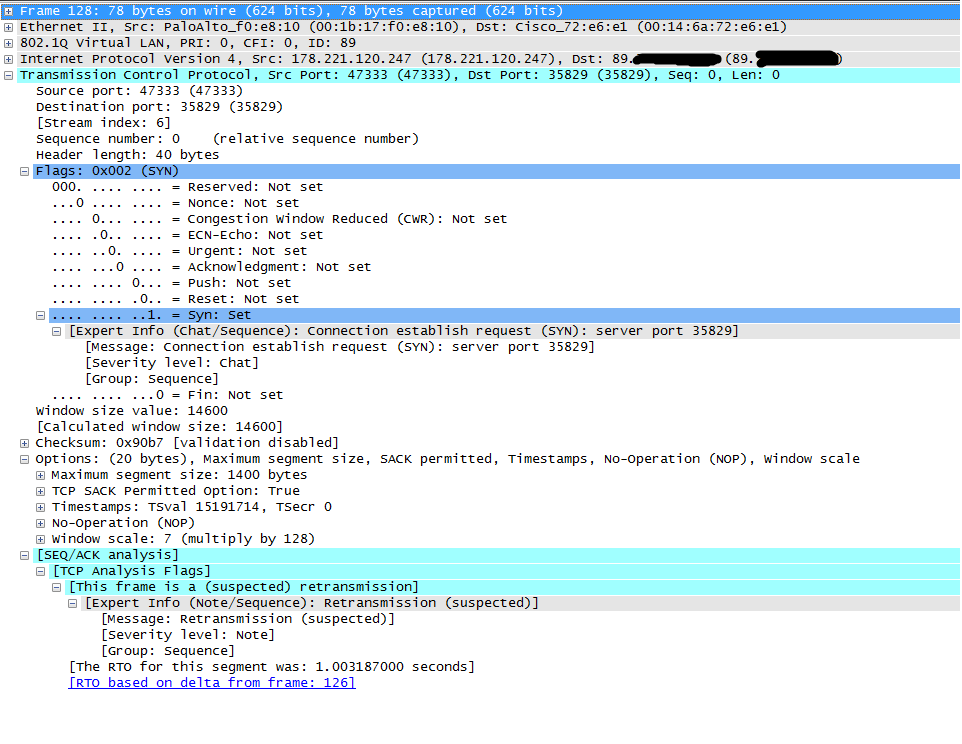
Tx stage with re-transmission
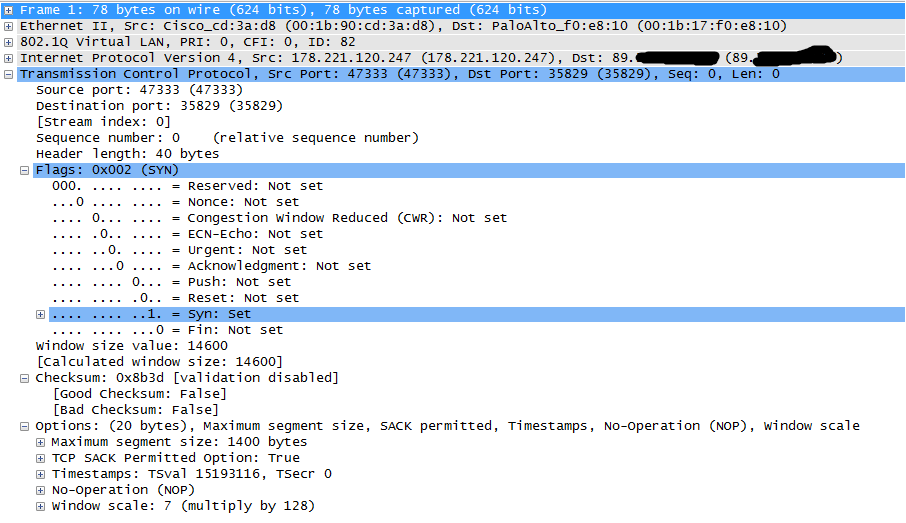
drop stage on FW for syn and all other packets destined to passive ftp port
Security policy was created to permit FTP with default-app in service field. From CLI I catched output that ftp-data session was created to destined ftp server and port xxxx.
Tician
- Labels:
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-03-2015 08:43 AM
Hello Tician
Could you please check the predict session on this firewall for that FTP connection. I think, the PAN is unable to open the pinhole for the new connection on port 35829.
a similar discussion thread: Re: About ftp passive mode App-ID insufficient-data
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-03-2015 10:54 AM
Hi Hulk,
yes but if you look at the first session on traffic tab, you can see that first session was established on port 35829 and correctly decoded as FTP app. After that all others was detected as not-applicable and dropped.
Can you tell me how to enable predict sessions only for ftp?
Tician
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2015 10:15 AM
Hi all,
I found cause off this behavior. Problem is on NAT device which is behind PAN firewall. Client initiate connection and one ftp session was created, but in moment where client send PASV request to server and server respond with port XXXX, client initiate connection to server on port XXXX. In that moment FW create new session ftp-data in INIT state with default time out 5 sec, but NAT device took long time to respond, more than 5 sec which is default timeout for INIT sessions on PAN fw. In that stage has no valid-opened session, firewall considered such session as not-applicable and had dropped a result.
So if I increase INIT sessions to 10 sec, there are no drops and ftp-data sessions were transit from INIT to FLOW. But I'm not happy with increasing session time out, so I need tracing issues on NAT device and cause of long time respond.
Regards,
Predrag
- 9997 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA1420 IKE packet disappear between receive (ingress) and firewall session state in General Topics
- while do the factory reset of pa 5250 showing error: findfs: unable to resolve 'label=sysroot0 in Next-Generation Firewall Discussions
- PAN-OS HA UGRADE PATH in Next-Generation Firewall Discussions
- Tuning Panorama HA Timers to Stop False HA1 Alerts over MPLS in Panorama Discussions
- HA ACTIVE firewall is failing when commit in General Topics



