- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GlobalProtect Authentication failed Error code -1 after PAN-OS update
- LIVEcommunity
- Discussions
- General Topics
- Re: GlobalProtect Authentication failed Error code -1 after PAN-OS update
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
GlobalProtect Authentication failed Error code -1 after PAN-OS update
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-24-2019 06:49 PM
We are on PAN-OS 8.0.6 and have GlobalProtect and SAML w/ Okta setup. It has worked fine as far as I can recall.
However when we went to upgrade to 8.0.19 and any later version (after trying that one first), our VPN stopped working.
The client would just loop through Okta sending MFA prompts.
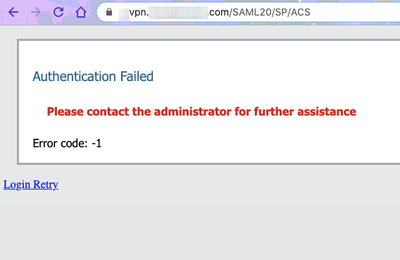
On the web client, we got this error: "Authentication failed Error code -1" with "/SAML20/SP/ACS" appended to the URL of the VPN site (after successfully authenticating with Okta.
When I downgrade PAN-OS back to 8.0.6, everything goes back to working just fine. No changes are made by us during the upgrade/downgrade at all.
Any advice/suggestions on what to do here?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-24-2019 08:01 PM
Since you are hitting the ACS URL it would appear that the firewall is sending the request, but it isn't getting anything back from Okta. I'd make sure that you don't have any traffic getting dropped between Okta and your firewall over port 443, just to verify something within the update didn't modify your security policies to the point where it can't communicate.
If communicate comes back okay you should really contact TAC and have them verify your configuration and work with you to ensure that everything is working okay. If it isn't a communication issue you'll need to start looking at packet captures and a tool like the SAML DevTools extension to see exactly what your response is and ensure that everything actually lines up.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-24-2019 08:40 PM
Is TAC the PA support? If so I did send a case in.
As far as changes, would I be able to load configuration from old backup onto the newer OS to override any of those changes if there were any security changes for example?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-18-2020 03:07 PM
Did you find a solution? I am having the same issue as well.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-18-2020 03:47 PM
Hello, I’d found that this was a certificate issue and I needed to renew a certificate even though it wasn’t technically expiring for another month.
when you get this error, what does the system log say? It should be a very recent entry after you get the error.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-19-2020 07:20 AM
I am getting the following error, I re-posted because I should have taken some of the URLs out. It is strange it is not showing a user name.
Client '' received out-of-band SAML message: <?xml version="1.0" encoding="UTF-8"?><saml2p:Response Destination="https://xxx.gov:443/SAML20/SP/ACS" ID="idxxx" IssueInstant="2020-02-19T15:13:57.156Z" Version="2.0" xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"><saml2:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameid-format:entity" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">http://www.okta.com/xxx</saml2:Issuer><ds:Signature xmlns:ds="http://www.w3
02/19 08:13:57
SAML SSO authentication failed for user ''. Reason: SAML web single-sign-on failed. reply message 'Reason: SAML web single-sign-on failed.'
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2020 03:54 PM
Did you find the issue with the client <username> being empty @David_Worley ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2021 11:46 AM
I am also facing the same issue with Panorama -> Prisma -> 10.0.4 version as well. Using the Prisma App provided in Okta portal. Any guidance or direction would be appreciated. Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-20-2021 09:14 AM - edited 05-20-2021 09:15 AM
I had same issue on my firewall. resolved after re configuring ntp (time settings ). this was because of time difference between SAML authentication URLs and your firewall. default maximum deference is 60s
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-20-2021 12:52 PM
Hi All,
Sorry, forgot to update this thread. Apparently, PAN doesn't support 'IdP initiated workflow' at the present.
Their recommendation is to create a bookmark and hide the original Prisma Access app.
Reference - https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Cm2oCAC
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-20-2021 12:52 PM
Sadly, this didn't work for me.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-11-2022 01:48 AM
Thanks. You are right. Resolved by changing time.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2023 11:20 AM
Hello, Did you change NTP servers or something else? Thanks
- 45422 Views
- 18 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA Global Protect in GlobalProtect Discussions
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions
- [Let me know reason & workaround] Global Protect Agent ver6.3.3 “PanPUAC_xxx.dat” does not work (auto create or renew, failed to open). in GlobalProtect Discussions
- CIE for user/group mapping for firewall on-premise in General Topics
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions