- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GlobalProtect not using AD group
- LIVEcommunity
- Discussions
- General Topics
- Re: GlobalProtect not using AD group
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-12-2017 05:58 AM
Hi,
I am running a PA-VM on AWS. It has two interfaces, one for management, one for data.
I have created an LDAP connection to our network and can log into GP using my AD credentials. So far, so good.
I need to have separation of users and assigned IPs based on group membership. I have an authentication profile with two sequences. One to match on the group that my account is a member of, the second uses local authentication.
In the GP gateway, I have the authentication set to the auth sequence (which uses the first authentication profile - the one that should match my account and group set first), and in the agent client settings, I have two entries. the first one should give me an IP address from the first range, the second entry is set to any/any and gives an IP from a different range.
When I connect, I use my username/password from AD but get an IP address from the second range.
The logs show these entries (note I have replaced the actual AD details):
1,2017/09/12 05:48:17,4E0FEDAE31E65C2,31,0x0,USERID,login,53,2017/09/12 05:48:17,0,0,0,0,,PA-VM,1,vsys1,10.7.2.10,xx\sfordham,,0,1,2592000,0,0,vpn-client,globalprotect,0,0,,2017/09/12 05:48:18,1
admin@PA-VM> show user group-mapping state all
Group Mapping(vsys1, type: active-directory): SaaS-Users
Bind DN : CN=xxx,OU=xxx xxx - Shared,DC=XX,DC=xxx
Base : DC=XX,DC=xxx
Group Filter: (None)
User Filter: (None)
Servers : configured 1 servers
213.78.96.130(389)
Last Action Time: 1607 secs ago(took 0 secs)
Next Action Time: In 1993 secs
Number of Groups: 1
cn=replaced_xxx,ou=security groups with mailbox,ou=security groups - shared,dc=xx,dc=xxx
admin@PA-VM>
admin@PA-VM> show user ip-user-mapping all
IP Vsys From User IdleTimeout(s) MaxTimeout(s)
--------------- ------ ------- -------------------------------- -------------- -------------
10.7.2.10 vsys1 GP xx\sfordham 2591689 2591689
Total: 1 users
admin@PA-VM>
From what I have read, GP in the above command *should* be AD
admin@PA-VM> show user user-ids
User Name Vsys Groups
------------------------------------------------------------------
xx.xxx\sfordham vsys1 cn=replaced_xxx,ou=security groups with mailbox,ou=security groups - shared,dc=xx,dc=xxx
Total: 22
admin@PA-VM>
So it looks like it is reading all of the necessary details - I can log in using my AD account, for example - it's just the mapping that's incorrect.
Can anyone advise?
Apologies if I have missed something blindingly obvious. I only started working with PA last week, so am learning as I go!
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-12-2017 08:05 AM
OK I is miffed, all the above works for me, i may be ciutching at straws but it could be worth changing your corp pool to a different subnet, I know user IP's are cached per user but not sure if this applies to different agent configs.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-12-2017 08:36 AM
Me too Mick!
So, I created a new AD group - first checking that spaces in OUs are OK (https://live.paloaltonetworks.com/t5/Management-Articles/Usernames-Not-Retrieved-by-the-Firewall-wit...) and added my user to that - also the other group was a distribution group, new group is a security group (just in case).
Edited the config to use the new group.
Changed the pool for Corp to 10.7.3.10-10.7.3.200.
Reconnected to the VPN - now getting a 10.7.3.10 address.
ever feel like you are going round in circles? 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-12-2017 08:57 AM
i dont think this is an issue with OU's as your name was retrieved when you started to type it in.
lets not give up hope as there are some clever peeps out there that have bailed me out on many occasions, and it's still quite a fresh call.
here are a number of things i would try, just for diags.
1, in your ldap profile and in your group id settings. just change the domain field to "test", commit, and then remove your name from the gateway config and add it again. it should auto populate under the domain "test" regardless of the real domain name.
try to connect again...
2, with the above still in place, clone your portal agent config, move it to the top and add your name here also.
i like to do this in the portal as the monitor/system tab shows you what portal config is being used, it does not seem to show this in the logs for gateway configs.
by the time you have done this, someone will jump in and make us both look stupid....
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-12-2017 08:59 AM
also, are you on V8.x
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-12-2017 10:09 AM
hmm... forget option 1. tried again and didn't work second time....
perhaps just change the domain name to the bit that you hace squiggled out. omitting .local.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 01:55 AM
the below snippet applies to user group mapping and server profiles, not sure if this may be the issue.
By default, the User Domain field is blank: the firewall automatically detects the domain names for Active Directory servers. If you enter a value, it overrides any domain names that the firewall retrieves from the LDAP source. Your entry must be the NetBIOS name
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 02:09 AM
Also.. to test your group membership and domain ID..
from the cli..
test authentication authentication-profile "your LDAP server profile" username "your username" password
you do not enter your password above, on CR you will be prompted for your actual password.
if your server profile or username includes spaces then use quotes as above
you know that LDAP is working already but this gives some extra info that may be helpful.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 02:40 AM
Morning Mick!
yes I am on 8.0.3.
I tried a few variations of the test command.
If I add myself explicitly then it works via the CLI (not by the client though at the moment):
admin@PA-VM> test authentication authentication-profile SaaS-VPN username sfordham password
Enter password :
Allow list check error:
Target vsys is not specified, user "sfordham" is assumed to be configured with a shared auth profile.
Do allow list check before sending out authentication request...
User sfordham is not allowed with authentication profile SaaS-VPN
admin@PA-VM> test authentication authentication-profile SaaS-VPN username XX\sfordham password
Enter password :
Allow list check error:
Target vsys is not specified, user "XX\sfordham" is assumed to be configured with a shared auth profile.
Do allow list check before sending out authentication request...
User XX\sfordham is not allowed with authentication profile SaaS-VPN
admin@PA-VM> test authentication authentication-profile SaaS-VPN username XX.local\sfordham password
Enter password :
Target vsys is not specified, user "XX.local\sfordham" is assumed to be configured with a shared auth profile.
Do allow list check before sending out authentication request...
name "XX.local\sfordham" has exact match in allow list
Authentication to LDAP server at XXX.XX.XX.XXX for user "XX.local\sfordham"
Egress: 10.7.0.89
Type of authentication: plaintext
Starting LDAP connection...
Succeeded to create a session with LDAP server
DN sent to LDAP server: CN=Stuart Fordham,OU=XXXX,OU=UK,OU=XXXX-XXXXX Staff,DC=XX,DC=local
User expires in days: never
Authentication succeeded for user "XX.local\sfordham"
admin@PA-VM>
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 02:56 AM
Mornin....
what is in your allow list for server profile, perhaps you could change this to the group you are trying to get working with GP.
Also.. set system setting target-vsys vsys1 prior to testing ldap
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 04:35 AM
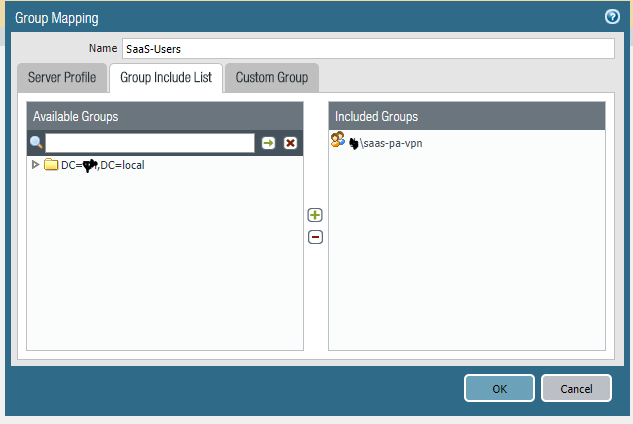
The included group is saas-pa-vpn
Just to put my mind at rest, I created a new OU and moved the saas-pa-vpn group to that, so the possibility of issues with spaces is eliminated.
I also created a new auth profile, and edited the old one to look at the new group, and edited the global protect details to match this new group.
Using just the group details, it all fails.
If I add myself (just "sfordham") to Test2, it succeeds:
admin@PA-VM> test authentication authentication-profile Test2 username sfordham password
Enter password :
Target vsys: vsys1
Do allow list check before sending out authentication request...
name "sfordham" has exact match in allow list
Authentication to LDAP server at xxx.xx.xx.xxx for user "sfordham"
Egress: 10.7.0.89
Type of authentication: plaintext
Starting LDAP connection...
Succeeded to create a session with LDAP server
DN sent to LDAP server: CN=Stuart Fordham,OU=xxx,OU=UK,OU=xxxx-xxxx Staff,DC=xx,DC=local
User expires in days: never
Authentication succeeded for user "sfordham"
admin@PA-VM>
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 05:00 AM
ok so set auth profile Test2 to only allow auths for your new group.
then.. set system setting target-vsys vsys1
then test auth and send output for failed auth.
then, remove user domain from auth profile and re test.
also from cli... "show user group list"
this will display all user groups within group id settings.
find the group you should be in and type:
show user group name "the full path to your group" (include quotes if any spaces)
check you are seen in this group and any domain info...
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 05:09 AM
The auth profile does not have the domain set (so is blank). Here is the cli output:
admin@PA-VM> set system setting target-vsys vsys1
Session target vsys changed to vsys1
Device not in multisys-mode
admin@PA-VM> show user group list
cn=saas-pa-vpn,ou=vpngroups,dc=xx,dc=local
Total: 1
* : Custom Group
admin@PA-VM> show user group name cn=saas-pa-vpn,ou=vpngroups,dc=xx,dc=local
short name: xx\saas-pa-vpn
source type: ldap
source: SaaS-Users
[1 ] xx\sfordham
admin@PA-VM>
So from the CLI it can interrogate AD correctly to show that my user account is in the correct & allowed group, but Test2 fails if I remove my account and just have the group in there.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 05:16 AM
yes. ok, cool.
now... make sure your group is in the auth profile
set system setting target-vsys vsys1
and test your auth.
I know you have done this and that it failed but you have not sent a screen dump of this.
well.. you did but not before using set system setting target-vsys vsys1
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 05:25 AM
The target vsys is set to vsys1 (in previous output posted).
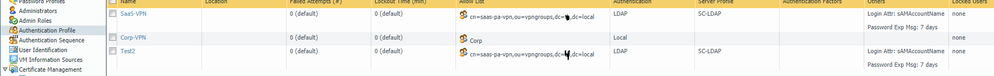
This is the auth profiles:
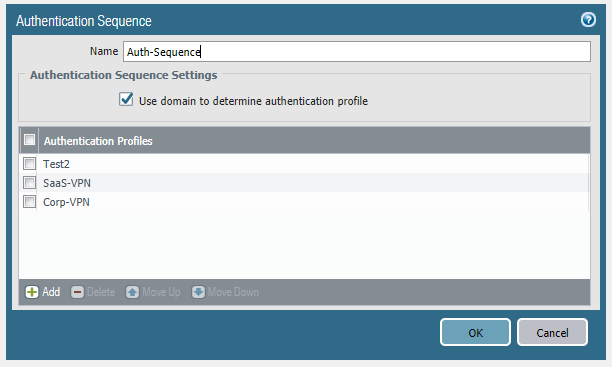
This is the auth sequence:
This is the cli test:
admin@PA-VM> test authentication authentication-profile Test2 username sfordham password
Enter password :
Allow list check error:
Target vsys: vsys1
Do allow list check before sending out authentication request...
User sfordham is not allowed with authentication profile Test2
admin@PA-VM> test authentication authentication-profile SaaS-VPN username sfordham password
Enter password :
Allow list check error:
Target vsys: vsys1
Do allow list check before sending out authentication request...
User sfordham is not allowed with authentication profile SaaS-VPN
admin@PA-VM>
I have tried various combinations, such as appending the NetBIOS domain name, the fqdn domain name and doing sfordham@xx.local.
Still get the same.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-13-2017 05:44 AM
i only mention set system setting target-vsys vsys1 as i seem to hop back to multimode every now and again.
so... now....
ad xx to your user domain ing test2 auth profile and test again. (not xx.local) just xx (i assume this is the same as the bits you have obscured)
- 20204 Views
- 46 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PAN OS version 11.1.13-h1 is remediate or not? in General Topics
- Panorama SDWAN in Panorama Discussions
- Global Protect Portal / Clientless VPN does not recognize SAML username after update to 10.1.14-h20 in GlobalProtect Discussions
- How do I access init-cfg.txt in VM-Series in the Public Cloud
- Global Protect Connectivity Issue in GlobalProtect Discussions