- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
In my PAN firewall, I can see a lot of spyware detection in Monitor tab.
- LIVEcommunity
- Discussions
- General Topics
- In my PAN firewall, I can see a lot of spyware detection in Monitor tab.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
In my PAN firewall, I can see a lot of spyware detection in Monitor tab.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2014 02:51 PM
Hi,
I can see a lot of spyware detected by PAN firewall. The threat is like- "Suspicious DNS Query (conficker:xtujyzyo.net)" .
Does anybody knows about this kind of issue?
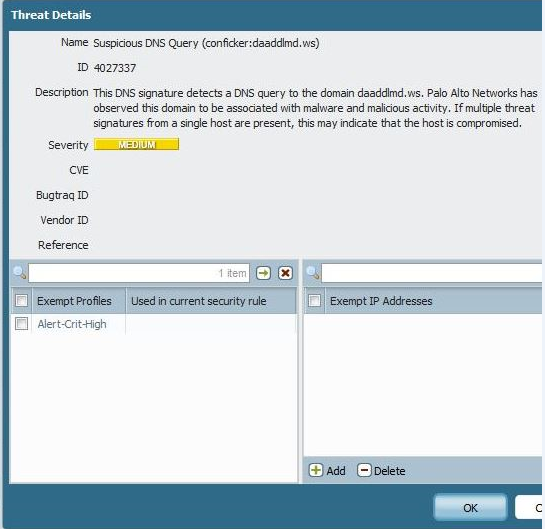
- Labels:
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2014 02:56 PM
Generally hosts that generate this log have been infected and you will need to visit the computer and remove the spyware or virus infection. These reports help you identify these hosts.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2014 03:31 PM
Thank you guys for your response.
@Steven Puluka- PAN is showing only one host, i.e., my Primary DNS server. What I am guessing is my other Secondary DNS servers are infected too. But PAN is not showing other host address.
@HULK- I am sorry, I am new to PAN- From where I can find the installed version of Threat database?
@Harrdik- So thought the system is infected, the DNS query is blocked by PAN? From some search, I found- How to Deal with Conficker using DNS Sinkhole - Is it good idea to implement this ?
Regards,
Nishant
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2014 03:52 PM
Hello Nishant,
Let us know if you need anything related to PAN FW, since you are very new. The threat database version can be visible from:
1. GUI > Dashboard > Genaral Information >Threat Version.
2. GUI > Device > Dynamic Updates > Application and Threats.
3. From CLI > show system info
Example:
admin@31-PA-3020> show system info
hostname: 31-PA-3020
sw-version: 6.0.2
global-protect-client-package-version: 0.0.0
app-version: 445-2292
app-release-date: 2014/07/08 14:43:28
av-version: 1317-1787
av-release-date: 2014/07/10 08:20:01
threat-version: 445-2292 >>>>>>>>>>>>>>>>>>>>>>>>>> Threat database version
threat-release-date: 2014/07/08 14:43:28
wildfire-version: 32185-38576
wildfire-release-date: 2014/06/17 14:11:02
url-filtering-version: 2014.07.11.221
global-protect-datafile-version: 1405115510
global-protect-datafile-release-date: 2014/07/11 21:51:50
logdb-version: 6.0.6
platform-family: 3000
logger_mode: False
vpn-disable-mode: off
operational-mode: normal
multi-vsys: off
Hope this helps.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2014 03:56 PM
Hi Nishant,
with bellow document, you can get regular mails for infected hosts, so its a consolidated information. That way you can block all user in one attempt.
Yes, its a good implementation.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2014 04:32 PM
Sorry, I wasn't paying close enough attention. With DNS flags like this you do get your DNS server as the source. But this is a false positive because you DNS server is just forwarding the request on behalf of your infected clients. So you need detailed logs from the DNS server to back track the requests to the ultimate host. You will likely need to increase the logging level to find this information.
See a fuller discussion in this previous thread.
Re: Suspicious DNS Query - how to find source computer?
This is what the new PanOS 6 DNS Sinkholing feature is designed to help you do. Get logging for the infected computers instead of the DNS server.
How to Configure DNS Sinkholing on PAN-OS 6.0
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- 4292 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- powered down V-wire port in General Topics
- Windows Clients – Captive Portal Not Triggering with GlobalProtect Always-On Enabled in General Topics
- Issues with SSH and Telnet access only on the passive firewall. GUI access is working fine. in Next-Generation Firewall Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- static route with path monitor down not removing BGP route in General Topics



