- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Intermittent SSL decryption issues for some, not all.
- LIVEcommunity
- Discussions
- General Topics
- Intermittent SSL decryption issues for some, not all.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Intermittent SSL decryption issues for some, not all.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-21-2014 01:59 PM
My Palo Alto Firewall 2050 running 4.1.16. I am having a lot of intermittent SSL decryption issues. I'm not sure what to do with some of these. An example is https://app.plangrid.com.
I can this site when I have made this change and restart my browser:
> set system setting ssl-decrypt skip-ssl-decrypt yes
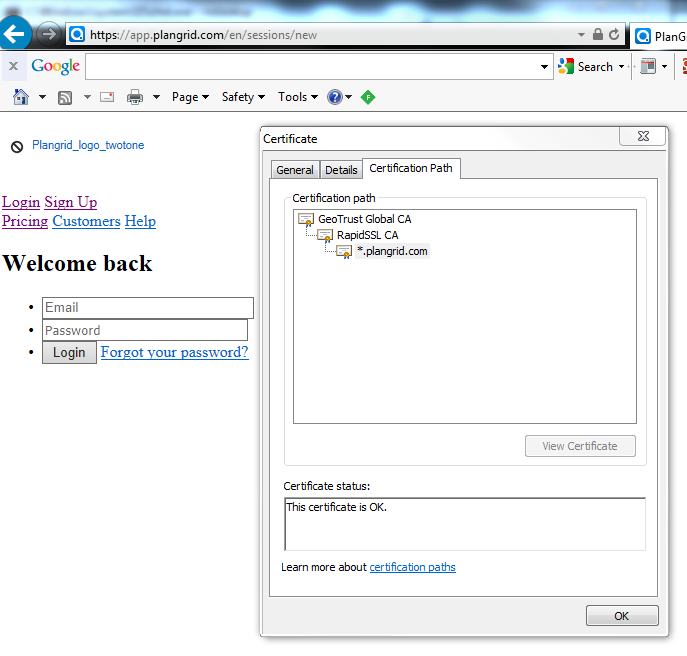
Setting this back to the no results in the page not loading correctly as shown below. This affects IE, Firefox, Chrome, and multiple computers.
I have added *.plangrid.com to the decryption certificate exclusion list, and cleared my ssl cache. This doesn't fix the problem.
> configure
# set ssl-decrypt ssl-exclude-cert *.plangrid.com
#commit
(wait)
#exit
>debug dataplane reset ssl-decrypt certificate-cache
I can see that this is implimented as the certificate path no longer shows my private signing certificate.
Usually I can exclude an IP address from SSL decrption and get past this. This particular site is hosted by Amazon CloudFront. I'm not about to disable SSL inspection on the entire CloudFront IP range, as this would be bad for obvious reasons.
This is just one of many sites that I am having issues with. https://www.mywot.com is another example.
How do I determine what is wrong, and how do I fix it?
- Labels:
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-23-2014 01:49 PM
The DNS entry app-assets.plangrid.com cnames to dogqy6r8czetd.cloudfront.net which points to IPs in Cloudfront.
The DNS entry app.plangrid.com cnames to gifu-9754.herokussl.com which cnames to elb037100-1517692282.us-east-1.elb.amazonaws.com which points to IPs in Amazon AWS.
Both of these use the exact same RapidSSL wildcard certificate.
The problem appears somehow related to https://dogqy6r8czetd.cloudfront.net/ With decryption turned on, I can't access this. With decryption disabled I can.
Is this a bug in PanOS 4.1.16? Or could this be related to SSL Decryption for Some Site Shows as Not Trusted ??
Could someone else running PanOS 4.1.16 with full decryption enabled see if they can connect to https://dogqy6r8czetd.cloudfront.net/ please?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-23-2014 02:48 PM
If I understand this issue correctly, the problem is that the PanOS 4.x cannot handle the SNI extension that is part of TLS.
Amazon Cloudfront added SNI support March 2014. Amazon CloudFront Adds SNI Custom SSL and HTTP to HTTPS Redirect Features
I can't whitelist the entire Cloudfront range; that would be a very bad thing. It seems like it could become a big deal.
It appears that PanOS 5.0.7 added basic support for SNI. I suppose it it time for me to upgrade off of the 4.x branch.
---
Q. What is the difference between SNI Custom SSL and Dedicated IP Custom SSL of Amazon CloudFront?
Dedicated IP Custom SSL allocates dedicated IP addresses to serve your SSL content at each CloudFront edge location. Because there is a one to one mapping between IP addresses and SSL certificates, Dedicated IP Custom SSL works with browsers and other clients that do not support SNI. Due to the current IP address costs, Dedicated IP Custom SSL is $600/month prorated by the hour.
SNI Custom SSL relies on the SNI extension of the Transport Layer Security protocol, which allows multiple domains to serve SSL traffic over the same IP address by including the hostname viewers are trying to connect to. As with Dedicated IP Custom SSL, CloudFront delivers content from each Amazon CloudFront edge location and with the same security as the Dedicated IP Custom SSL feature. SNI Custom SSL works with most modern browsers, including Chrome version 6 and later (running on Windows XP and later or OS X 10.5.7 and later), Safari version 3 and later (running on Windows Vista and later or Mac OS X 10.5.6. and later), Firefox 2.0 and later, and Internet Explorer 7 and later (running on Windows Vista and later). Older browsers that do not support SNI cannot establish a connection with CloudFront to load the HTTPS version of your content. SNI Custom SSL is available at no additional cost beyond standard CloudFront data transfer and request fees.
Q. What is Server Name Indication?
Server Name Indication (SNI) is an extension of the Transport Layer Security (TLS) protocol. This mechanism identifies the domain (server name) of the associated SSL request so the proper certificate can be used in the SSL handshake. This allows a single IP address to be used across multiple servers. SNI requires browser support to add the server name, and while most modern browsers support it, there are a few legacy browsers that do not. For more details see the SNI section of the CloudFront Developer Guide or the SNI Wikipedia article .
- 4650 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- SSH Proxy Decryption issue in Next-Generation Firewall Discussions
- Intermittent IPSec Tunnel Monitoring Issue in Next-Generation Firewall Discussions
- Action of allow but of Type policy deny in General Topics
- Issues with Pre-Defined Decryption Exclusion in General Topics
- application showing as incomplete + ipsec tunnel issue in General Topics



