- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Issues with SSL Forward Proxy in Lab Environment
- LIVEcommunity
- Discussions
- General Topics
- Issues with SSL Forward Proxy in Lab Environment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2021 05:32 PM - edited 10-30-2021 05:47 PM
Hi!
I've recently been trying to setup decryption on my PA-220 in a lab environment and have not been able to get it set up correctly so far. It is licensed, up-to-date, and currently running 8.1
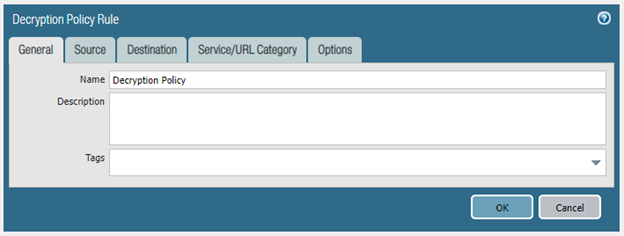
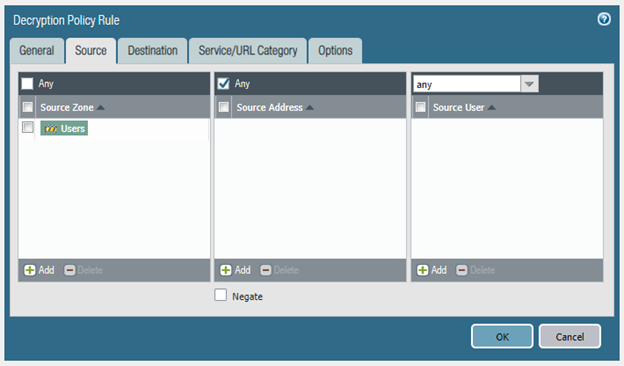
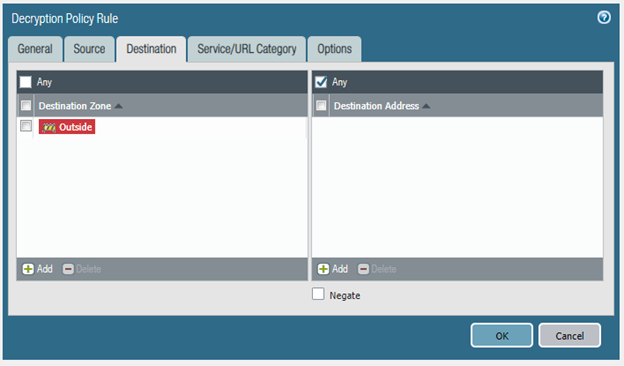
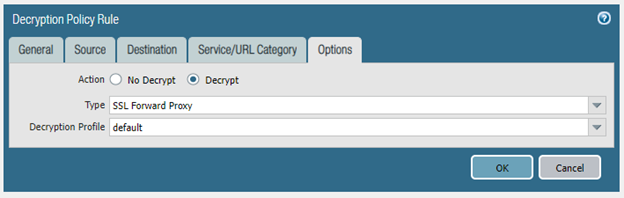
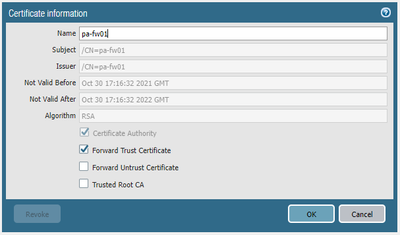
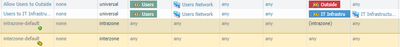
The steps that I've taken so far are to setup a decryption policy (the settings of which are included above), generate a self-signed certificate, set that certificate as the Forward Trust Certificate, commit and install the certificate onto one of the machine's.
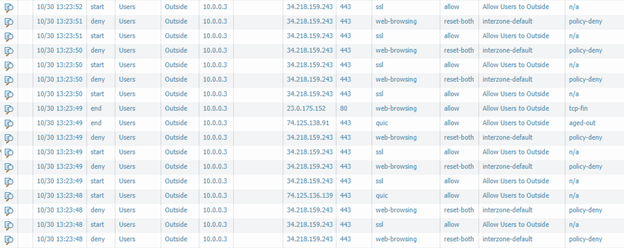
However, after each attempt, I'm getting the above traffic; I seemingly get an allow followed by a policy-deny against the interzone-default.
Does anyone have any ideas what I may be doing incorrectly? Any help is greatly appreciated.
Thanks!
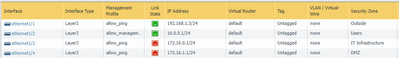
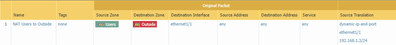
Additionally, I'm including my general setup below. If any additional information is needed, feel free to ask.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2021 08:38 PM - edited 10-30-2021 08:58 PM
Hi @benball ,
This is very common with PAN-OS 8.1 and below. Once the traffic is decrypted, the NGFW recognizes the decrypted application as web-browsing. Web-browsing on tcp/443 does not match any of your rules and therefore is dropped by the interzone-default rule.
Create a new rule to allow web-browsing on service-https, and your configuration will work. This means that you configured decryption correctly! [Edit yet again.] Now that you are decrypting traffic, your NGFW will recognize many more web apps like facebook, google, etc. So, you may as well allow any app outbound on 443 until you decide if you will build a full whitelist.
PAN-OS 9.0 added secure ports to applications so that web-browsing with application-default will work with SSL decryption and you do not need to create a separate rule. https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-release-notes/pan-os-9-0-release-information/fea...
Thanks,
Tom
PS You can also add the Decrypted column in the traffic logs to verify if the NGFW is decrypting traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2021 08:38 PM - edited 10-30-2021 08:58 PM
Hi @benball ,
This is very common with PAN-OS 8.1 and below. Once the traffic is decrypted, the NGFW recognizes the decrypted application as web-browsing. Web-browsing on tcp/443 does not match any of your rules and therefore is dropped by the interzone-default rule.
Create a new rule to allow web-browsing on service-https, and your configuration will work. This means that you configured decryption correctly! [Edit yet again.] Now that you are decrypting traffic, your NGFW will recognize many more web apps like facebook, google, etc. So, you may as well allow any app outbound on 443 until you decide if you will build a full whitelist.
PAN-OS 9.0 added secure ports to applications so that web-browsing with application-default will work with SSL decryption and you do not need to create a separate rule. https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-release-notes/pan-os-9-0-release-information/fea...
Thanks,
Tom
PS You can also add the Decrypted column in the traffic logs to verify if the NGFW is decrypting traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2021 08:11 AM
Thank you for the help! That was the problem. I updated to PAN OS 9.0 and everything worked as expected.
- 1 accepted solution
- 3745 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GloablProtect + Explicit Proxy blocks WSL traffic. in Prisma Access Discussions
- Limitations Observed with XQL Custom Widgets and Issue Visibility in Cortex XDR Discussions
- Smart Alert Triage Across Multiple Tenants and Environments in Advanced Threat Prevention Discussions
- web file blocking in Next-Generation Firewall Discussions
- Log forwarding from Cloud NGFW in Azure to Log Analytics Workspace for Sentinel in VM-Series in the Public Cloud