- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Multicast Packets forwarding
- LIVEcommunity
- Discussions
- General Topics
- Re: Multicast Packets forwarding
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Multicast Packets forwarding
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2013 07:38 AM
Hi Guys,
Looking for some help!
Quick simplifiy overview of the setup.
PA is the DHCP Server for two subnets:
Subnet A
10.101.0.0/16
Subnet B
10.102.0.0./16
All wireless clients are in subnet A conencted via seperate enterprise Wireless LAn Controller and Apple TVs also connected to the same WLC are in Subnet B. Subnet A and B and in seperate VLANs (VLAN101 and VLAN102)
At the moment no clients can see the Apple TVs as the multicast Bonjour packets are not forwarded between these subnets. Is it possible to make the PA forward these packets between these subnets and then the icing on the cake would be then to use a policy to decided who can communicate with each Apple TV.
Anybody tried anything similiar and can point me in the right direction??
Thanks,
Jaggie
- Labels:
-
Networking
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2013 08:39 AM
You can forward multicast packets by enabling multicast in the virtual router and adding the interfaces in the interfaces tab. Some tweaking may be needed for the interface source/destination - this might help To determine who can communicate with what, I'm guessing you can just add the Apple TV's or TV subnet to an address object and permit/deny access using User-ID or subnets/objects. Depending on if you are L3 or L2 firewalling, this article may help as well
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2013 08:50 AM
Hi das,
Thanks for the reply.
I am working in L3.
All the subnets are connected to the same Vrouter and I have added IGMP and PIM on all of the interfaces.
I am a little confused about the "Group Permissions" tab under VR - Multicast - Interface Group - If I leave it balnk does that mean that all Multicast packets will be forwarded between all of the interfaces???
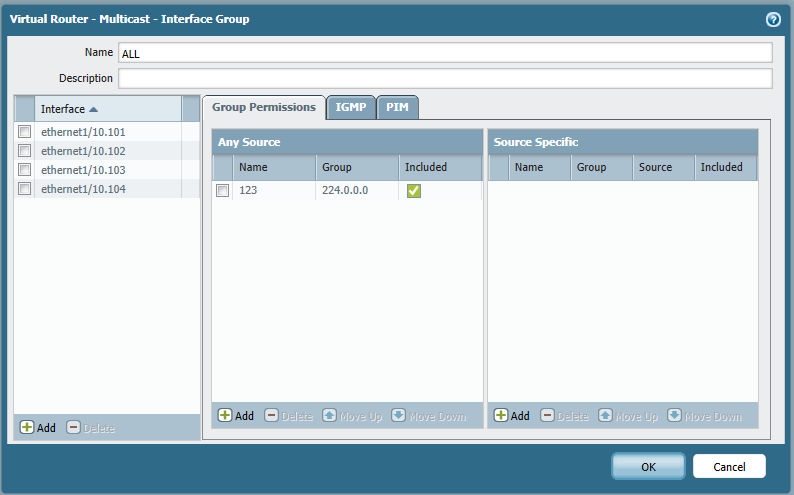
I have then create a policy rule to allow all Multicast traffic though the required zones. I don't seem to see any Multicast traffic on the "Monitor" tab - is this normal?
Thanks,
Jaggie
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2013 08:59 AM
As seen in the guide:
Also:
Specify general rules for multicast traffic:
|
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2013 11:00 AM
I am also interested in this.
I am curious, however: We are in a similar boat, but instead of messing with the firewall, I just dropped the Apple TV in the appropriate VlAN 101 and called it good. Do you have reason the Apple TVs can not be on VLAN 101?
Thanks,
Bob
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2013 11:14 AM
HI Bob,
The reason that the ATVs cannot be in VLAN 101 is two fold:
FIrst of all, we are talking about an eventual 100 odd ATVs and the the ipad will only ever show 9 ( I think this s the correct number) in the list.
second is that as the clients are on an enterprise wireless solution they are in about 16 different buildings, but because they are in the same VLan no matter where they are they end up seeing ATVs that are over 1km away!!!!!
the idea is to separate the ATVs into the separate subnet and VLAN and then create rules in the PA for each ATV. I was then going to make a little app that the user launches and then choose the ATV that they want to see from a list. After submission from the app a server side routine updates the PA via the XML api to allow the users IP to access the ATV.
well at least that is the plan! At the moment I have the clients and the ATV separated but cannot get the interface with the ATVs to forward the multicast packets to the interface with the clients on it.
any ideas for me!?
thanks,
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2013 11:29 AM
Not really a Palo Alto related fix, but, I have enabled a multicast filtering option in on my wireless "Drop multicast packets from associated clients". Thus the only units which can see the Apple TVs, must be connected to the same AP. There may be some options like that in the switches as well depending on the switch.
Adding all those rule to the PA sounds like a nightmare!
Hope that helps,
Bob
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2013 11:05 PM
Hi das,
I have followed the guides but I am still not getting anything. This is maybe more a question for support but if you havea ny ideas then I would be appreicative.
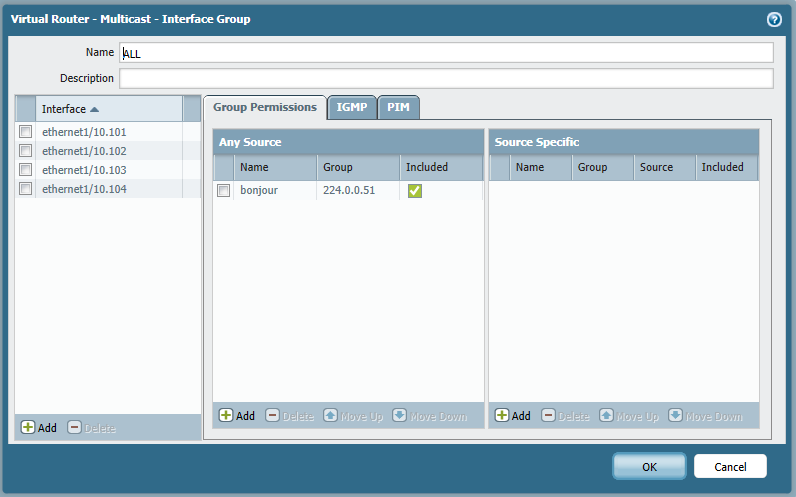
Thanks,
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-26-2013 06:17 PM
Hi There,
I could be wrong, but I don't think simple Multicast Routing will accomplish this. This is almost more of a protocol forwarding option, like DHCP forwarding. I haven't done research on this, but I would first google to see if there is a way of accomplishing this with a normal router. If it can be done by configuring Multicast in a certain way then we may be able to do it on the firewall using standard Multicast configuration. If not, broadcasting ATV traffic across L3 boundaries may take some type of proprietary solution, such as protocol (bonjour?) forwarding. Note, that there is a reason why these protocols have broadcast-domain scope - they can be quite chatty, so it may not be in your best interest to break that model.
Cheers,
Kelly
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2013 04:29 PM
Hi, I'm not sure if you've got this resolved yet, but I had a very similar requirement to route Multicast traffic between two different networks. I found that we could get multicast sessions working fine from our Cisco switches, but when it needed to be routed, it wouldn't work. After going through the switch logs, it became apparent that the default IGMP query interval on the switches and the PA firewall are different. It was 60 seconds on the switches and 125 seconds on the firewall. These query intervals need to be synchronous for it to work. After setting it to 60 seconds on the firewall, I could get multicast sessions working over different networks, routed by the firewall.
I took the example they gave here: https://live.paloaltonetworks.com/docs/DOC-4197 which is designed for multcasting between two PA firewalls and re-accomodated it for multicast routing on just 1 firewall.
- 10450 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA-415-5G not working with fresh T-Mobile SIM in General Topics
- Trying the DNSProxy feature for Static Response in General Topics
- Interface Errors after upgrade - VM Series in Next-Generation Firewall Discussions
- Issue to send security policy forwarding log by email in General Topics
- Using GlobalProtect with NAT in GlobalProtect Discussions



