- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
OpenVPN to a server behind PA
- LIVEcommunity
- Discussions
- General Topics
- Re: OpenVPN to a server behind PA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
OpenVPN to a server behind PA
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-13-2017 08:00 AM
I have a dest NAT setup with port translation thus:
untrust untrust public IP tcp 443 > private IP tcp 1194
Policy set as
untrust trust any src to public IP for 443.
The NAT works fine, but I see aged-out on the traffic monitor, and no traffic at all on wireshark on my PA > Server LAN.
Am I missing something?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-13-2017 11:59 AM
Could you take a screenshot of the actual rule you have configured.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-19-2017 10:39 AM
You hide important port of Your rules...
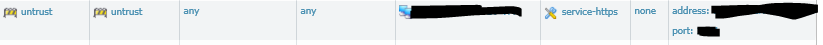
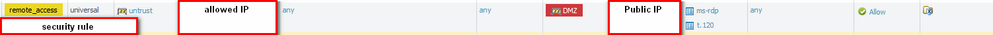
Please take a look at my example:
Security rule:
NAT rule
In You case in security rule insted of my ms-rdp and t.120 please put any but in service please create your own service with port 443.
In NAT as a "public IP" please put your public address of VPN serwer, as RDP 3502 please use Your serice 443. As "address k133" please put local IP (from DMZ) of Your VPN, insted of 3389 please put 1194. That's it.
I advice You to read carefully this article https://live.paloaltonetworks.com/t5/Tech-Note-Articles/Understanding-PAN-OS-NAT/ta-p/60965
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-20-2017 02:06 AM
Thanks for the response, how you describe is how I have it setup.
I have replicated (with diff address) the NAT, and policy rules, for an internal IIS server, and that connects fine. Hence my issue appears to be with the the ongoing LAN connection from inside the PA, to the OpenVPN server. No traffic reaches it. Whether this is a PA issue (I sense not, now) or an issue with the L2 path behind the PA on the LAN, I don't yet know.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-20-2017 02:49 AM
Hello
I'm glad to hear that is started working.
If You have problem with conenction from LAN to DMZ You need to create another rules (in PaloAlto knows as U-turn rules) please read tech doc that I mention or find using search button how to create it.
With regatrds
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-20-2017 03:06 AM
It isn't working. What I'm saying is that if I use the same NAT/Policy rules (with diff addresses) and try to connect to the IIS server using the destination NAT with port translastion, I see traffic from the PA internal LAN interface to the web server on that network.
When I use the same theory to connect to the OpenVPN server, there is nothing at all on the LAN between PA and OpenVPN.
e.g. NAT 1.2.3.4 port 443 translates to 10.1.1.2 port 1194. From an external source, if I try to connect to 1.2.3.4:443, then the PA performs the NAT translation, the traffic is allowed, but that's where it ends. There is no traffic between PA interface 10.1.1.1 and openVPN on 10.1.1.2.
Hairpinning is if I'm trying to connect from inside to out, on the external address, and back in. I don't need to do this as far as I'm aware.
- 7549 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- user-id - Firewall is not learning upn name format in Next-Generation Firewall Discussions
- Error when calling “Get number of users at location(s)” API in Prisma SASE Aggregate Monitoring APIs in Prisma Access Discussions
- Push Cortex XDR datasets/logs to dedicated syslog server in Cortex XDR Discussions
- Sectigo Root CA Trusted Store Request in General Topics
- all incidents are missing in Cortex XSOAR Discussions