- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
PA-220 Not Decrypting any HTTPS Traffic even after I have followed ALL the Palo Alto Live Videos
- LIVEcommunity
- Discussions
- General Topics
- Re: PA-220 Not Decrypting any HTTPS Traffic even after I have followed ALL the Palo Alto Live Videos
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
PA-220 Not Decrypting any HTTPS Traffic even after I have followed ALL the Palo Alto Live Videos
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2018 08:01 PM
For some reason SSL Decryption is not working on my PA-220 - I have followed many many many of the palo alto instructions to try to get it to work but some how it is still not working - the PA-220 is simply not decrypting any of the Https Traffic. I cannot even decrypt a single https traffic for some reason.
I have installed the Certificate that was generated by the PA-220 into my computers
My browser will now recognise and use the certificate generated by my PALO ALTO firewall.
but for some reason, when I go to facebook, it does not decrypt the facebook page
All http traffic will work with the browser, but all https traffic will not work. the browser simply does not decrypt https traffic for some reason. I have follow the above instruction exactly. and I can see that all my browser is using the firewall generated certificates, but it is just that for some reason the firewall does not decrypt the facebook traffic or any https traffic. everytime it goes to a https website the browser gets this error message :
Secure Connection Failed
The connection to the server was reset while the page was loading.
The page you are trying to view cannot be shown because the authenticity of the received data could not be verified.
Please contact the website owners to inform them of this problem.
NET::ERR_CERT_AUTHORITY_INVALID
And at times the browser keeps on saying - Connection Reset
Will installing a top level paid SSL Certificate into the PA-220 solve this issue ?
Can someone please recommend a good and affordable SSL Certificate company/website that has been tested/confirmed to work for the PA-220. After i have installed the paid ssl certificate into my PA-220, all HTTPS traffic should be able to be decrypted by all the network PC's.
Hope to hear from you soon. THANK YOU !!!
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2018 12:01 AM
Hi,
First, you cannot use a paid SSL certificate with SSL Decryption. Your firewall generates certificates on-the-fly for the sites your users browse to and a regular, paid, does not provide this functionality.
The last time I enabled SSL decryption with Palo Alto self-generated certificates (as opposed to, for example, Microsoft Active Directory CA services) I followed this path:
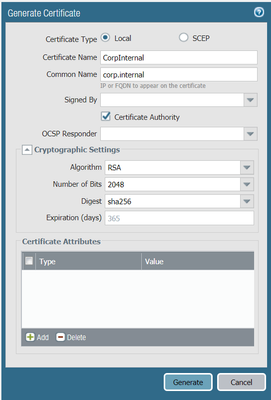
1. Generated a top-level cerftificate
For example: Name: PAN-CA, common-name: ca.paloalto.local, 'Certificate Authority=checked'
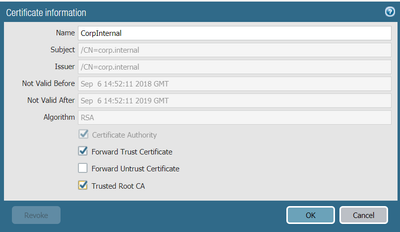
After Generation mark as trusted-root-CA
2. Generate a decryption certificate
For example: Name: PAN-Fwd-Trust, common-name: trusted.paloalto.local, Signed-By='PAN-CA', 'Certificate Authority=checked'
After Generation mark Forward Trust Certificate
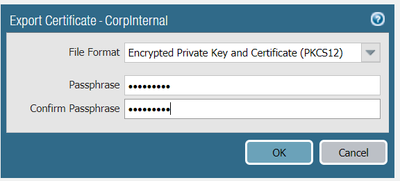
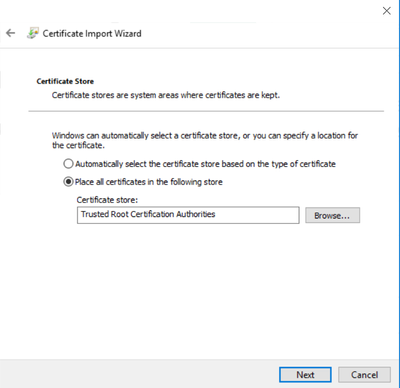
3. Exported the PAN-CA (from step #1) certificate and added it to Computer-Trusted-Root-CA (mmc, certificates, computer account)
4. Added a decryption rule from one source IP for testing
5. Checked forthe 'decrypted' flag in the traffic monitor
Don't forget that depending on your rulebase, you might need a rule with Application=web-browsing & Service=tcp/443.
Hope this helps,
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2018 12:57 AM
Hi @CatCatCat
From the error you see it looks like you did not import the root CA cert correctly. Or did you import the cert into windows certificate trust store but the tests you have done with firefox? Firefox has its own certificate store where you also need to import the cert.
What page did you try where you get this error?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2018 04:43 PM
Make sure
- In Device - Certificate Management - Certificates - Device certificates you can see your decryption cert is there, has a tick as both a CA and Key, is Valid and has a Usage of Forward Trust Certificate.
- In Policies - Decrpytion has a rule there for the traffic and the options are set to dcrypt, Type SSL Forward Proxy.
- Commit.
As has been said, the cert needs to be exported then installed on your PC as a trusted root certificate, firefox has its own store so you need to go into the options to install it there also.
If that doesnt work, and you go to a HTTPS page, what certificate does your browser show is trying to be used? Is it your firewall certificate?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2018 08:00 AM
Hi Mate,
Few screenshots below. There is not so many steps to get up an running.
*don't forget to create a forward untrust cert as well to get presented when the site has untrusted certs applied..
best regards,
R
- 5707 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Palo Alto FW manage by SCM - problem with HA in Strata Cloud Manager
- Stealth Rule Question in Next-Generation Firewall Discussions
- port issue / nmapping in Next-Generation Firewall Discussions



