- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Decryption issue (wrong certificate)
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL Decryption issue (wrong certificate)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 08:00 AM - edited 02-06-2017 11:05 AM
Hi All,
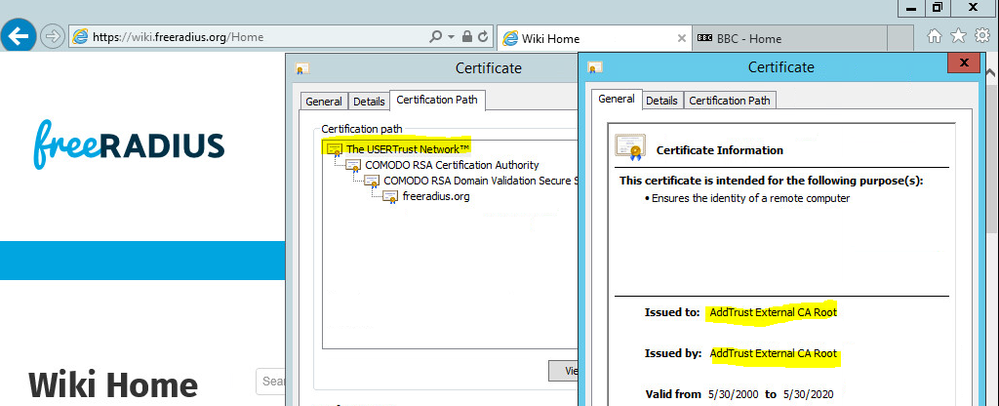
Having SSL Decryption issue with one of the websites at the moment (https://wiki.freeradius.org/Home)
So testing without decryption and checking certs chain:
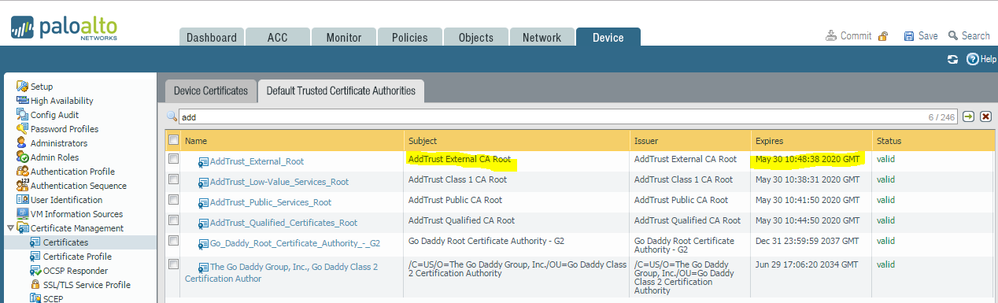
Can see root CA on Palo:
So all looks good. Implementing SSL Decryption (test version only) with two certs generated on PA one for forward trust another is for forward untrust:
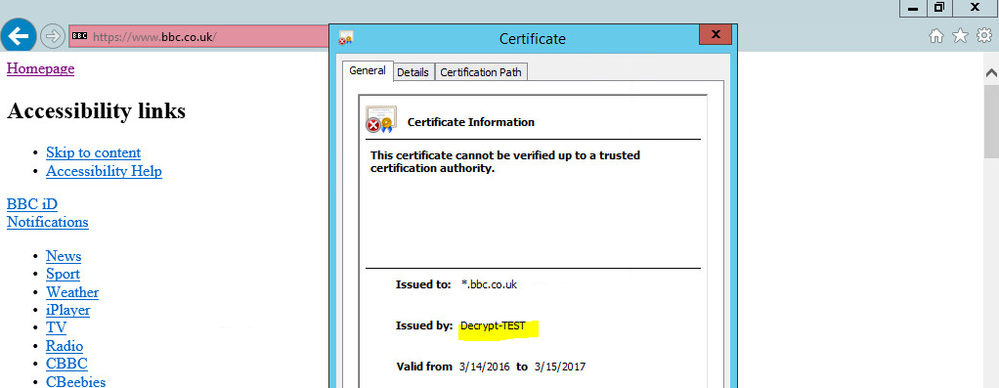
Doing a test with some websites reviewing a forward trust cert. As an example bbc.co.uk:
l didn't import cert to the test PC as want to confirm first everything is working fine.
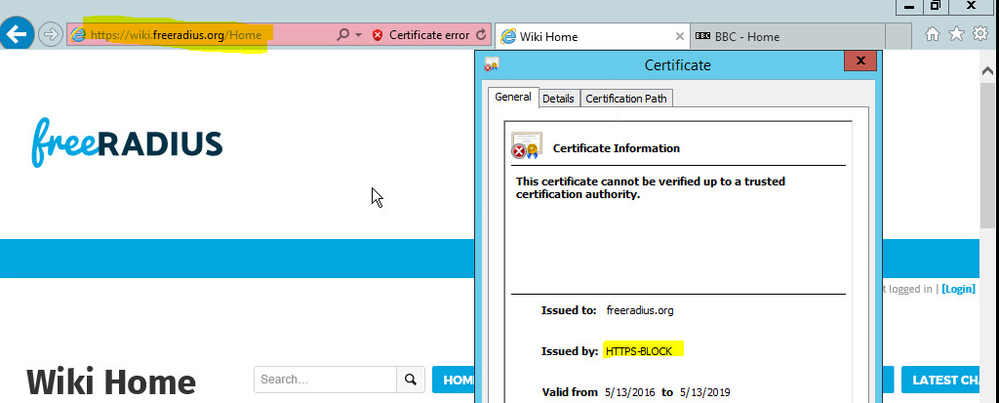
Done another test with the websites which allow decryption all looks good correct cert is forwarded. But for the website https://wiki.freeradius.org/Home getting the wrong cert which is forward untrust:
Don't know why. Cache is cleared, and the new cert is recreated for untrust but still the same.
PA-5050 Active/Active PAN-OS 7.1.5
Am l missing something simple?
Regards,
Myky
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:07 AM - edited 02-06-2017 11:09 AM
Check the results there is your answer:
https://www.ssllabs.com/ssltest/analyze.html?d=wiki.freeradius.org&hideResults=on
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:12 AM
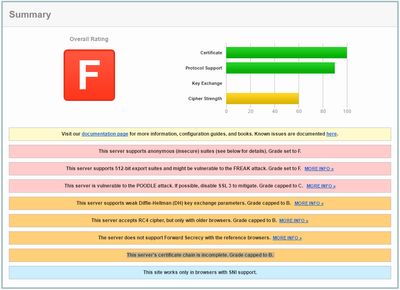
I'm not certain, but this might be caused by an incomplete certificate chain (per ssllabs.com):
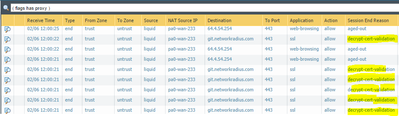
The traffic log complains about cert-validation as well:
https://www.ssllabs.com/ssltest/analyze.html?d=wiki.freeradius.org
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:07 AM - edited 02-06-2017 11:09 AM
Check the results there is your answer:
https://www.ssllabs.com/ssltest/analyze.html?d=wiki.freeradius.org&hideResults=on
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:12 AM
I'm not certain, but this might be caused by an incomplete certificate chain (per ssllabs.com):
The traffic log complains about cert-validation as well:
https://www.ssllabs.com/ssltest/analyze.html?d=wiki.freeradius.org
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:17 AM
@jvalentine @Retired Member thanks all. Looks like l missing something simple. Why the web-browser is not complaining without ssl decryption in place?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:20 AM
Its because you use IE.
IE wil try to dowload the missing certificates in the chain.
Try firefox and it will complain.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:25 AM - edited 02-06-2017 11:28 AM
@Retired Member ok with firefox l am not even able to open this website. Chrome also is not complaining:
I am new to SSL so if you can let me know what is actually happening with the server cert l will appreciate:0
Thx,
Myky
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:34 AM - edited 02-06-2017 11:40 AM
Its not a problem of the PA or your decryption settings.
The website certificate is incorrect configured, the intermediate certificates are missing.
Thats why the PA sends the "not trusted" certificate to your browser.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:36 AM
Hi @Retired Member
Ok cool as you said before IE and Chrome will ignore this, right? As long as it has a root CA.
Thx,
Myky
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:40 AM
Yes, Chrome(uses the windows cert store) and IE will try to download the intermediate certs as long as they have a valid root CA in their certificate store.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 11:50 AM - edited 02-06-2017 11:53 AM
Cool l have learned something new today. Thanks/ Last thing Do you have any good article explaining this?
Thx,
Myky
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-06-2017 12:06 PM
Your welcome.
I don't have documentation on this issue specific. ( its all in my head 😉 )
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2017 05:26 AM
To fix the issue for this particular website l did import a COMODORSADomainValidationSecureServerCA.crt to the box:
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2017 05:53 AM
In my opinion is importing the intermediate certificate in this situation wrong.
The behaviour was as expected and correct.
With this "fix", you are covering a warning that the site is misconfigured.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2017 06:03 AM
I do agree with you as really it is a "masquerading" of the problem.
- 2 accepted solutions
- 8756 Views
- 13 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- web file blocking in Next-Generation Firewall Discussions
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- Trendmicro application identified as "ssl" despite of proper SNI, CN, SAN. in General Topics
- No "certificate used by" field when generating certs for SSL forward trust and untrust? in General Topics
- Azure "az" command and decryption in Next-Generation Firewall Discussions