- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Decryption
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL Decryption
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Decryption
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-04-2019 03:17 AM
Hi guys,
Nowadays I am playing with a PA-VM (no license) and decryption policy. Basically there are many articles and that explain how Decryption policy works and how to set it up. I have checked and double checked my setting and I cannot make facebook.com for instance work when I enable the Decryption.
Here are the rules:
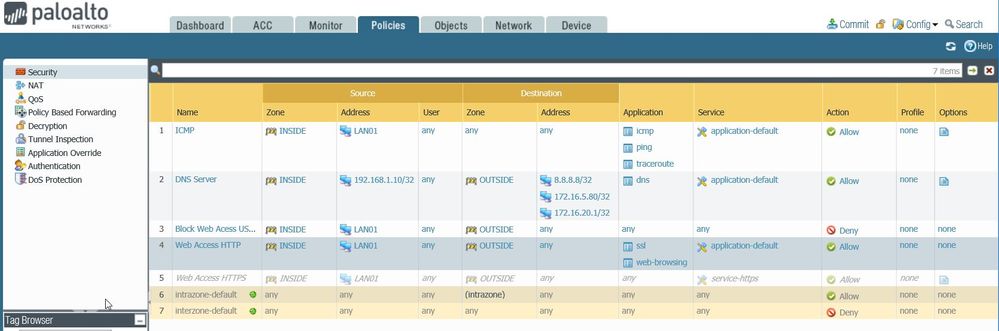
Cheers
Danilo
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-04-2019 03:35 AM - edited 02-04-2019 03:40 AM
Hi @DaniloBarbosa,
Am I missing something because I don't see you allowing the facebook app in your policy which is what you're trying to achieve in your example ... correct ? I see you only allowing ssl and web-browsing.
Also your policy order seems incorrect as you have a block all rule in front of your allow ssl and web-browsing rule as far as I see it, preventing you from ever hitting your allow rule.
Cheers !
-Kim.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-04-2019 12:24 PM
Hi kiwi,
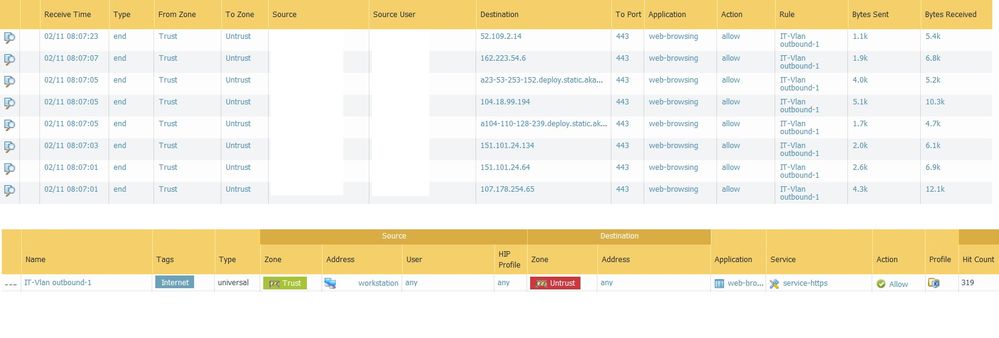
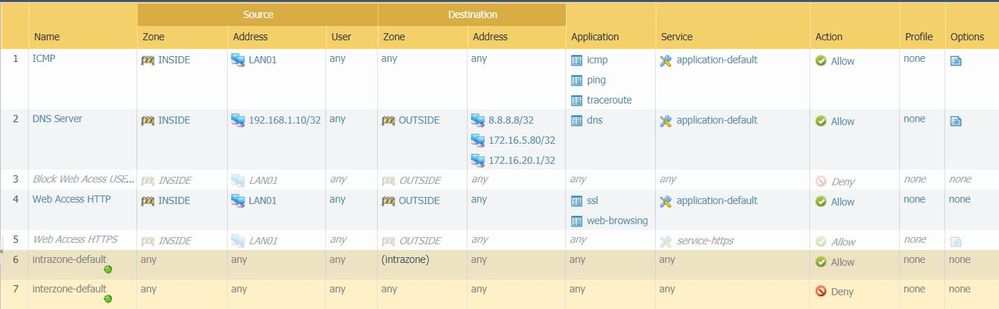
Basically I was using "User ID" before remove the users from user tab and take a screen shot for this post. So the Rule number 3 was blocking Internet access for a specific user and the rule 4 was allowing access to everyone else inside the windows domain. I did remove the users but I forgot to disable rule 3. Check the new screen shot. 😉
Another think that I haven't explained. I am allowing full Internet access, but I want to see the Palo decrypting facebook page. So on the Decryption rule 1 (OUTBOUND) I am olny decrypting "social-networking" that included Facebook.
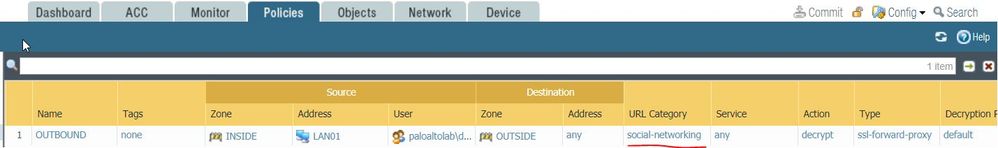
The main goal here is just to see the PALO working as Man-in-the-middle, decrypting traffic between user and facebook page.
Cheers
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-04-2019 12:35 PM
You will need to remove the "application-default" on that rule, because once the SSL is stripped and the underlying application is seen, it's still on port 443 which is not in the list of default ports on 'web-browsing'.
The logic may seem odd, but it follows this flow:
1. Traffic is identified as SSL when the Client Hello is seen.
2. Decryption starts here, and when the TLS handshake is completed the app-id switches from "SSL" to "Web-browsing".
3. Because the app has changed, it is re-evaluated in security policy. Since the app is web-browsing, but it's not on port 80 as defined in the app, rule 4 will be skipped.
4. The application has no matching rules, so it falls to the Interzone-default which denies the rest of that session.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-08-2019 11:22 AM
Hi @gwesson@DaniloBarbosa@kiwi
I think they should release an application list update, which add working port 443 for web-browsing application.
I also notice that once you decrypt traffic on 443-SSL it becomes 443-web-browsing, so policy rule that allow web-browsing on application-default will not work, because the application-default is 80.
You need to create another policy to allow web-browsing application on 443 port.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-08-2019 01:08 PM
So here's the thing with what you are asking, it breaks the app-id for anyone that isn't decrypting traffic. So say for example the app-id is updated to allow tcp/443 in addition to the standard of tcp/80, for anyone that isn't decrypting traffic seeing web-browsing on tcp/443 would be a concern.
Because of that, the guide for enabling SSL-Decryption specifically calls out the fact that you'll see web-browsing on tcp/443. As you have to actively enable SSL-Decryption, it makes sense to break things for people who are actively enabling a new feature versus breaking things for everybody else.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-08-2019 02:08 PM
Thank you for the reply,
So for the users who decrypting the traffic, do we need to create custom application for web-browsing on 443?
Because with the current situation I need to create another policy rule to allow web-browsing on 443.
I think it will be better to create new application like: Secure web-browsing.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-08-2019 08:51 PM
That would be more of a personal preference. If you want to build out a new application signature and create a new app-id for identifying traffic you can certaintly do so; however, with that being said most environments would bypass that and simply allow web-browsing on tcp/443 via a seperate policy.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2019 01:06 AM
Hi @gwesson,
I did follow you advice and changes the service from "application-default" to "any" but it did not work.
Here is the Any on service tab for SSL and web-browsing.
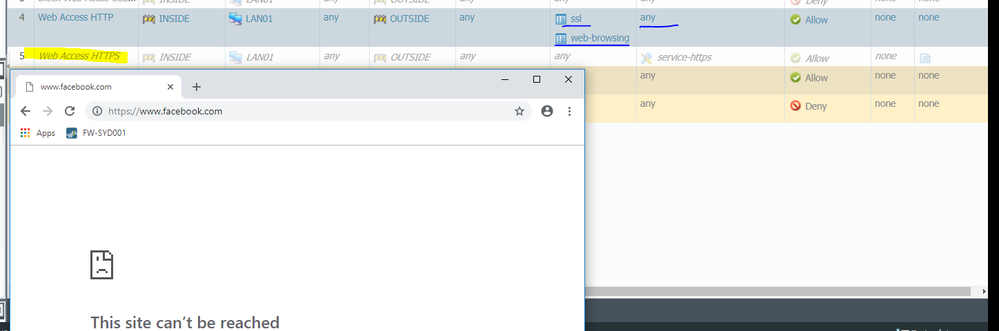
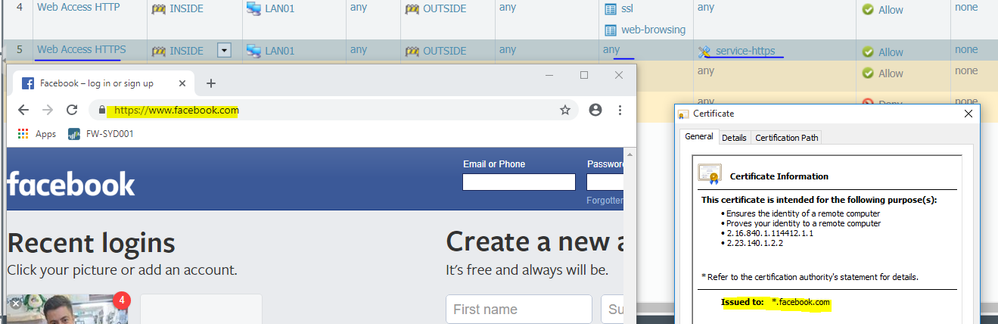

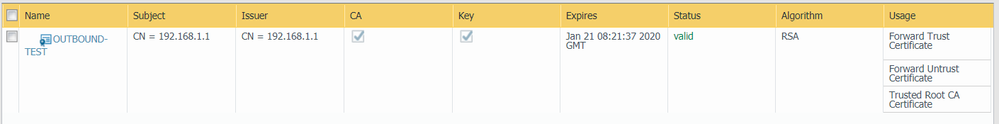
The decryption rule is not working because I should see the certificate from the firewall not from facebook. But let's not discuss this issue now, let's go back to the SSL/HTTPS issue.
My goal is create a rule that allow HTTPS (application) on its default port (443) and protocol (TCP) only, any other application on tcp/443 will be blocked or if https on any port that is not 443 will be blocked.
I don't want a generic rule allowing TCP on port 443, that would match any application.
Cheers
Danilo
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2019 01:07 AM
Hi @SShnap
I will try that. Maybe you gave me the answer and I didn't noticed...lol
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2019 01:20 AM
Not yet SShnap, I cannot see what I am missing.
Have you created an rule with application web-browsing and service-https that worked?
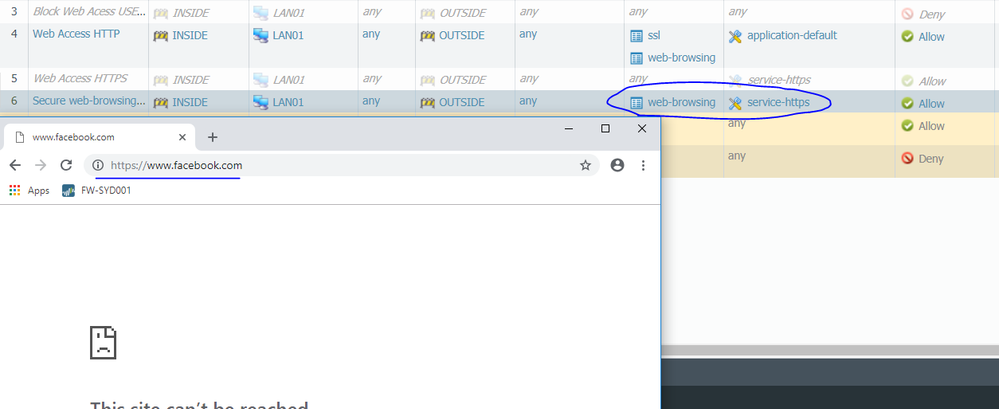
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2019 08:15 AM
Please check the logs if the traffic is being decrypted,
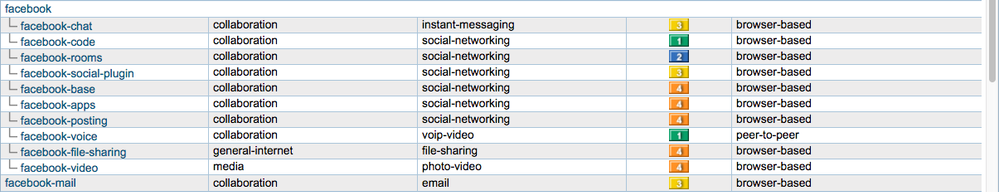
Pay attention, for Facebook site palo alto identify the application as facebook-base that's why it being blocked, for Facebook site you should add facebook-base for allowing it.
See my attachment, regular sites that palo alto identifies applicaiton as web-browsing will be match to that policy rule, if the site uses other application you need to allow that specific application.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2019 11:42 AM
It's still being blocked because you're only allowing 'web-browsing' and 'ssl'. Facebook has a large number of unique app-id definitions depending on what you're doing. From Applipedia:
Start with a rule allowing all apps for yourself, then use the traffic log to see the list of apps seen by the firewall when you hit that rule. Then, you can create a more complete rule to allow only what you want.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2019 04:12 PM
Hi @SShnap
I cannot chekc the logs because it is a VM without license. I am testing the solution before invest some money on it.
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Cm2mCAC
Cheers
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-11-2019 04:13 PM
Hi @gwesson
I thought the main facebook page would pass on the web-browsing rule (without login into facebook), then if I log in all the extra "Apps" would need another rule.
I will give a try.
- 13708 Views
- 18 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Decryption suddenly failed for all Webpages using Sectigo Certs in General Topics
- Chatgpt enteprise login only in Next-Generation Firewall Discussions
- web file blocking in Next-Generation Firewall Discussions