- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Syslog - LFP options
- LIVEcommunity
- Discussions
- General Topics
- Syslog - LFP options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Syslog - LFP options
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2020 05:16 AM
Hi Guys
We have PA with version 9.0.4 and have to configure Syslog server log forwarding on the same. Created (syslog) server profile..Now creating "Log Forwarding Profile" there are options "forward method" and "built-in-action" available there. which is not giving so much clarity what need to be configure there, Referred few articles available on Internet but no-one giving much clarity for the configuration side.
Requesting suggestion for further configuration.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2020 05:54 AM
Good Day
You will be using the forward portion of the Log Forwarding Profile.
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/monitoring/configure-log-forwarding.html
Essentially
Create the profile.
Add in what notifications you want (Threat logs... ok... ALL logs?... log geq medium? ok.)
Where do you want these log messages to be fwd to? SNMP, email, syslog, Panorama. ok... good
Next, modify your security policy and apply the log forward profile to whatever rules you want to be, well, log forwarded to.
Let me know how else I can assist.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2020 06:22 AM
Hi Steve,
What if we configure, as found some more ways probably (except Log Forwarding Profile)
1- Configure Syslog Server Profile
2- Device - Log Setting - System -> call Syslog Server created in profile -> Filter logs as per levels Critial , High, informational, Low, Medium.
Once configure, commit.
Is'nt also the correct way ..?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2020 06:44 AM
Well, that will work only if there are SYSTEM logs that match the various levels.
But if a CRITICAL malware or vulnerability came through the FW, this would NOT show up as a SYSTEM log message, and would not be forwarded.
If the concern is about SYSTEM logs.. that is fine.. but you are missing out on 99% of the threat notifications on the FW.
Is this what you are intending?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2020 06:50 AM
Hi Steve,
Thanks for Quick and instant responses.
Well, We need to check with client what they are actually intending. if they are OK with system logs then we are almost done as you rightly said with "Log setting" options.
But if they want Threat and other related logs to be available on Syslog then have to go for "LFP" option.
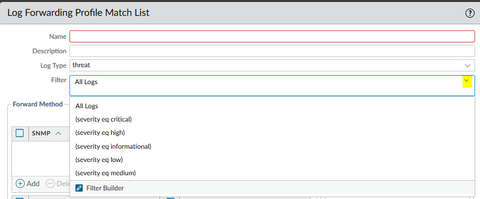
One more point at this moment : Where do we get option to set log levels (Critial , High, informational, Low, Medium) under Log Forwarding profile option. I can't find these anywhere there...
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2020 07:27 AM
here is a quick screen capture
I hit the dropdown arrow, and the choices are there.
- 4322 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- "Bugs" on Syslog Field Descriptions documentation PAN-OS 11.1+ in General Topics
- XSIAM API pagination in Cortex XSIAM Discussions
- Sending USB Alerts via syslog (Cortex XDR) in Cortex XDR Discussions
- Push Cortex XDR datasets/logs to dedicated syslog server in Cortex XDR Discussions
- Export Issues and Cases from XSIAM in Cortex XSIAM Discussions