- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Tunnel between PaloAlto and PaloAlto
- LIVEcommunity
- Discussions
- General Topics
- Tunnel between PaloAlto and PaloAlto
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Tunnel between PaloAlto and PaloAlto
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2013 06:59 AM
Hello,
i'm trying to get this constellation running:
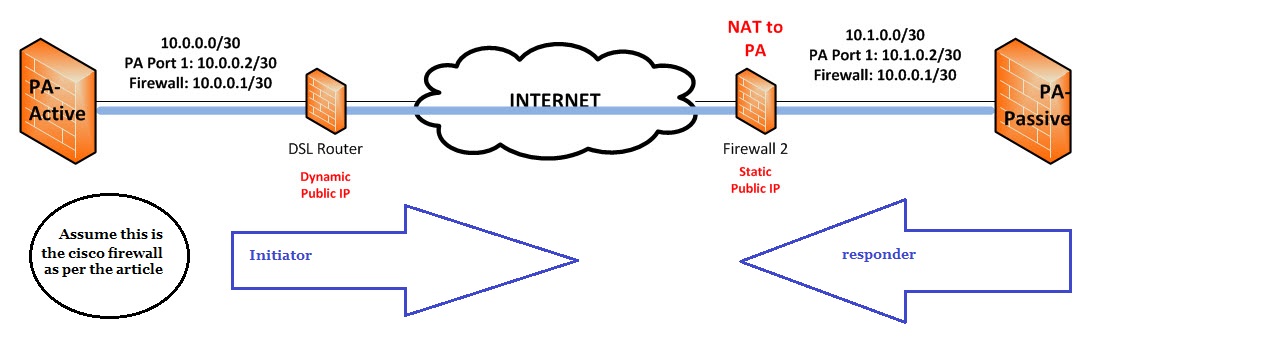
Two PA 200 behind a DSL-Home-Router and a firewall with a fixed public IP at the passive site.
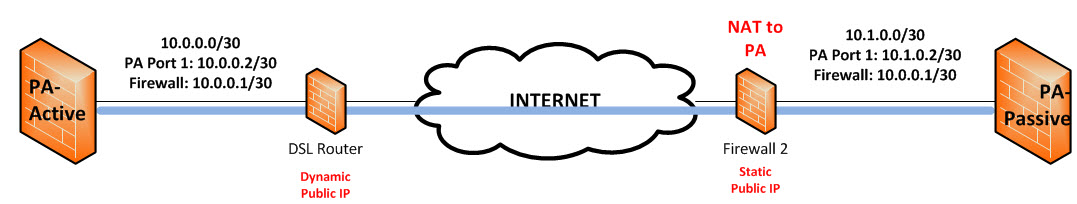
This image is just an example how it looks like....
First i want to get the active site ("PA-Active"; PA 200; Version 5.0.6) running...
I configured the IKE Gateway, Tunnel interface and also the IPSec Tunnel, but the PA doesn't want to establish/initialize the connection at all...I cannot see any log files in "traffic" either in "system"...Firewall policies should allow the traffic...
Here are the settings i made:
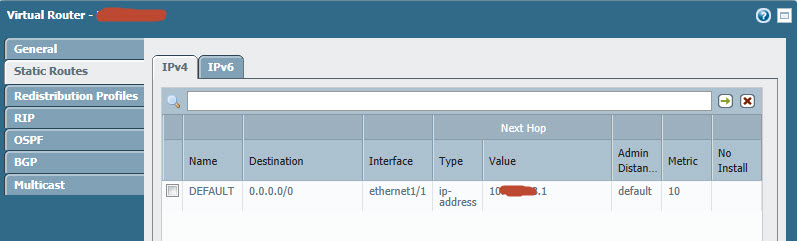
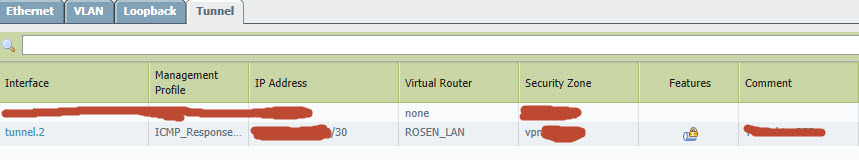

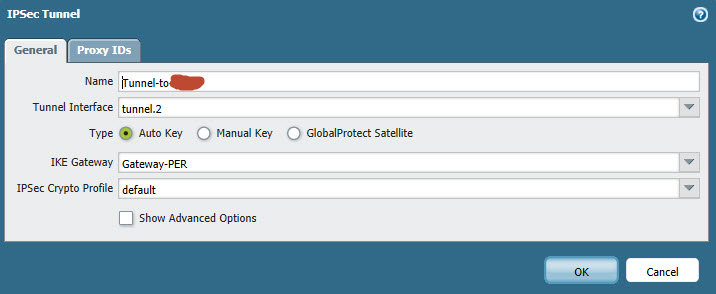
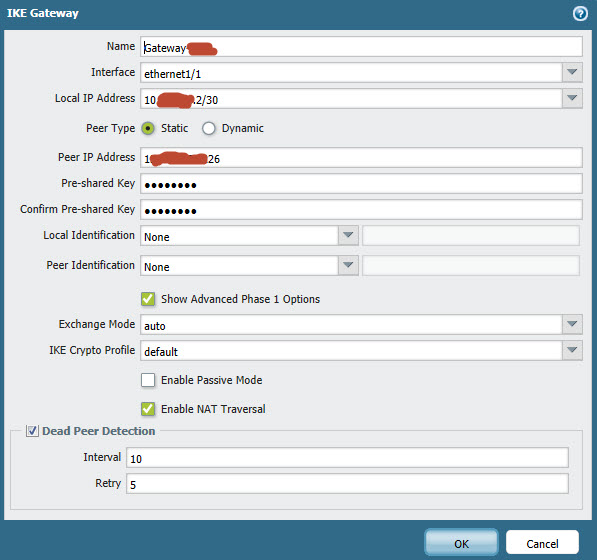
Can someone help? Did i missed a config?
- Labels:
-
Configuration
-
Networking
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2013 07:13 AM
Hi Hithead,
Do you have a policy to permit ike and ipsec application from the untrust zone to the untrust zone, if at all there is a clean up rule at the bottom of the firewalls ?
What are the IKE identities that you are using on the remote PA firewalls?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2013 07:15 AM
Are you also permitting ike and ipsec traffic on the firewall 2?
To rephrase my earlier question, may I know what local and remote peer IDs have been configured on each of the PA 200s?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2013 07:20 AM
Hi...You need to add a static route for the IP network that is found across the tunnel. Let's say the remote LAN has IP subnet 10.11.12.0/24. You would add static route dest=10.11.12.0.24 use interface=tunnel.2. Then you need to generate traffic like pinging a host at 10.11.12.x to force traffic to the tunnel & bring the tunnel up. Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2013 07:25 AM
The static route is the thing that's needed as said.
Also I would suggesting building a tunnel monitoring profile on both sides... I have Palo Alto to Palo Alto IPSec tunnels in production, and I noticed that the tunnels wouldn't come back up if I rebooted one side of the tunnel without tunnel monitoring in place (which kind of makes sense.. the IPSec SA was never being torn down on one side, I had to clear it manually to get the tunnel back up).
I will say that my PA to PA tunnels have been rock solid though, after that one little gotcha.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2013 07:41 AM
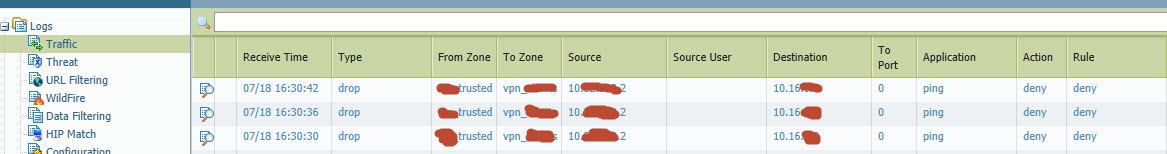
Hi,
i added 10.0.0.0/8 (because all traffic should go through the tunnel)...And also make a ping from the interface 1/1... and still no reaction or something else to initialize a tunnel...
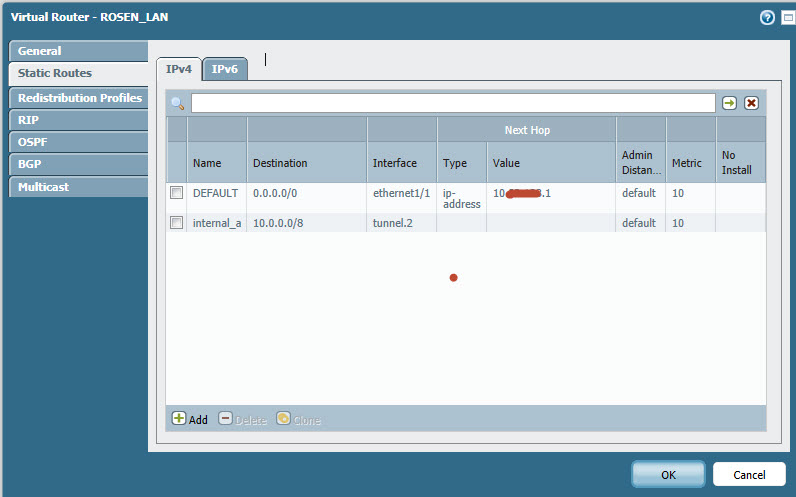
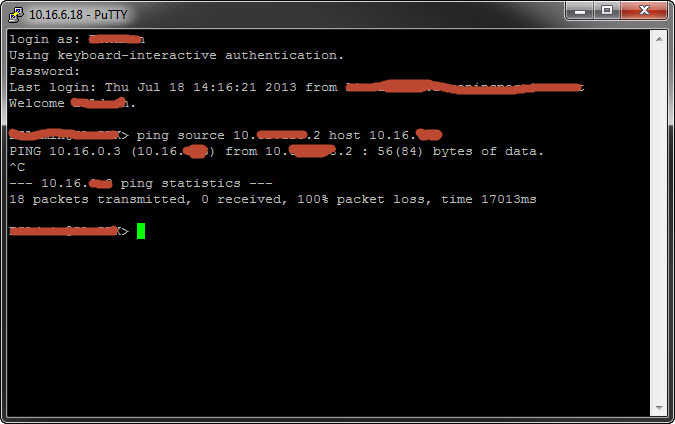
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2013 07:56 AM
Do you have a catch all NAT policy configured on your PA? If you do, you need to set up a noNAT for the traffic you're trying to send over the tunnel. That's usually the culprit when I can't figure out why a tunnel isn't seeing interesting traffic and coming up
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2013 08:07 AM
Hi..
no there is no NAT configured for this traffic.
Can you please do me a favour and provide some screenshots of your configuration?
Because i'm really confused why my PA didn't try to establish a VPN tunnel...
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2013 08:16 AM
Your traffic log shows the ping are being dropped so the tunnel will not come up. Make sure you have a security rule allowing the traffic to the tunnel zone. Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-18-2013 08:28 AM
Hi HIthead,
I am still wondering if the Phase-1 is getting established or not. Are the phase 1 and the phase 2 up?
>show vpn ike-sa
>show vpn ipsec-sa
I have an apprehension that we are failing in the negotiation itself.
BR,
Karthik
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2013 07:01 AM
Thanks a lot,
after allowing ping to the tunnel zone the PA tries to establish a tunnel.
BUT, now i need to get NAT Traversal running. Because both PAs are behind a NATing firewall and DSL router, so the IKE will be lost on the way... In the IKE gateway settings i enabled the NAT traversal option and the PA still try to use IKE Port UDP500... Is it correct? Or how can i solve the NAT problem to prevent the UDP packet lost?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2013 10:24 AM
Don't know if you understood the problem...but...
The IKE UDP packet doesn't get received at the other end... Does IKE works with NAT? Have i change something at PA or somewhere else to get it run?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2013 11:20 AM
Hi,
Could you please make the PA firewall as initiator which is behind the dynamic public IP address. Also set the IKE negotiation in aggressive mode. Since we don't have any address to use to contact the peer ( to the dynamic side). . Also set the IKE gateway "Peer type" as dynamic with a suitable local and peer identification ( FQDN, IP address, email Address).
Thanks
Gantait
- 7696 Views
- 16 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- linux /etc/iproute2/rt_tables filled with 231 pangp.include and 232 pangp.exclude in GlobalProtect Discussions
- Suggestion for a good model. in Next-Generation Firewall Discussions
- Whatsapp (IOS) Traffic not recognized in PaloAlto Firewall in General Topics
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- Working overseas - Unable to connect PaloAlto global protection VPN in GlobalProtect Discussions