- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
unknown-tcp and web application
- LIVEcommunity
- Discussions
- General Topics
- unknown-tcp and web application
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2016 12:27 AM
Hello Experts
Just want to know,
1- If PA can not identify the web application then it will classify it as SSL/Web-browsing or unknown-tcp?
2- unknown-tcp and unkown-udp is only for client/server application?
Regards,
GR
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2016 02:07 AM
Hi @ghostrider
in scenario 1, if the application has already been identified as ssl or web-browsing and no 'deeper' application can be determined, the session will remain ssl or web-browsing
for scenario2: if no application can be determined at all (a custom application or something completely new) but the session appears to flow normally (tcp handshake, normal flow of acks or in the case of udp, normal stream of packets) the session's application will be set to unknown-tcp/unknown-udp after about 2000 bytes/8 packets (4 packets after tcp handshake). This would also apply for peer-to-peer
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2016 01:39 AM
If PA sees exchange of keys as they happen in SSL (and TLS) session the application will be recgnised as SSL and nothing further can be recognised unless you decrypt the session.
If traffic matches http protocol and no specific http application is recognised then the application will be recognised as web-browsing.
If the traffic is neither http protocol nor SSL/TLS session then it will be unknown TCP.
This is not official info, but I think it's correct.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2016 02:07 AM
Hi @ghostrider
in scenario 1, if the application has already been identified as ssl or web-browsing and no 'deeper' application can be determined, the session will remain ssl or web-browsing
for scenario2: if no application can be determined at all (a custom application or something completely new) but the session appears to flow normally (tcp handshake, normal flow of acks or in the case of udp, normal stream of packets) the session's application will be set to unknown-tcp/unknown-udp after about 2000 bytes/8 packets (4 packets after tcp handshake). This would also apply for peer-to-peer
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2016 03:51 AM
Thank you both.
1- In case of SSL decryption, then PA will then identify as web-browsing if no deeper application is identified?
2- Also for if deeper application is identified by PA and I only allow web-browsing in policy then PA will reject the traffic? I am asking because I have security policy for BLUECOAT PROXY to go to internet, if I allow only SSL, Web-browsing then it will work? as it is impractical to identify whole bunch of http applications in policy.
Appreicated your reply
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2016 04:36 AM
1 - yes
2 - if you only allow web-browsing and SSL from your proxy to internet then you will have a lot of unhappy users and a lot of work. There are many ways to come to a good application policy. Either use application categories or make 2 groups (like GoodApps and BadApps) and try to fill them with apps that your users use. You can also make a combination of both; use categories and groups together where groups act like a white list or black list for overriding rules by categorization.
And in every scenarion your first decision will be; how to start. Either with all apps blocked except specific groups/categories and then slowly open more. Or only bad apps blocked and then slowly add more to blocked group.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2016 12:04 PM - edited 11-07-2016 12:12 PM
Thank for reply. Again sorry for my ignorance but want to ask:
1- In genral if I allow only web-browsing and SSL in security policy (assuming doing the SSL decryption) and PA identify the deepr application like fb-chat then in this case the access to that deeper application will be blocked? In short allowing web-browsing and SSL only, will not allow all web-applications?
2- Coming to proxy question, how I can know all the web applicaitons on internet, user will browse on internet and allow in policy?I just want allow all web-browsing and SSL from proxy to internet. What can I do?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2016 11:10 PM
1. Yes
2. Work with app categories or application filters as they are called. Or allow port 80 and 443 and only block selcted apps and/or categories.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-09-2016 04:18 AM
@santonic Just one question, if I am not doing SSL decryption on PA, then all internet web-browsing would be boils down to SSL and web-browsing applications? So in security policy if I allow only web-browsing and SSL applications for bluecoat to internet traffic (browsing) then it would be fine right?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-09-2016 04:45 AM
Nope.
On http traffic you will have a lot of applications always as it's not encrypted.
On https traffic most of sessions will be recognised only as SSL without decryption. But in same cases (like for example TeamViewer where destination for CONNECT command is always something like *.teamviewer.com) specific application will be recognised even without decryption.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-09-2016 07:16 AM
Hi @ghostrider
santonic is right.
If you check Objects > Applications and filter on Technology 'browser-based' you will find over 900 applications that fall into this category ... allowing only SSL and web-browsing appication won't be enough to allow them :
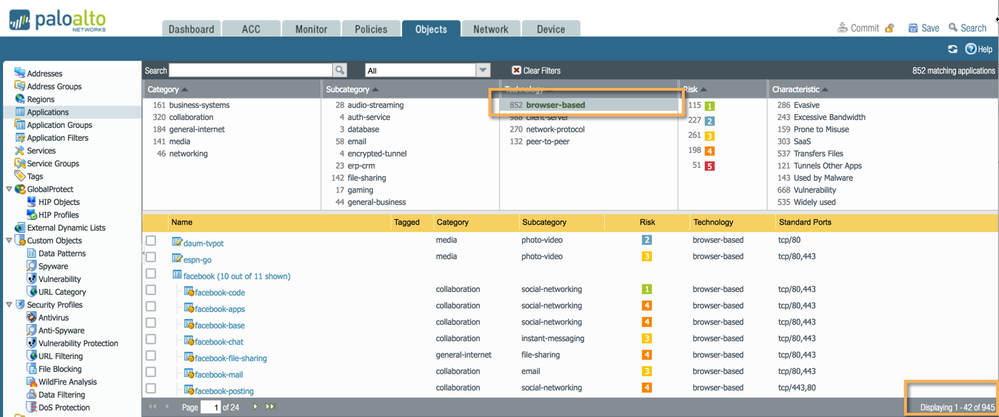
Cheers !
-Kim.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- 1 accepted solution
- 11360 Views
- 11 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- False Positive (Generic.ml) in VirusTotal
- Correlating a file path to application inventory in Cortex XDR Discussions
- Cortex XDR Tenant Auto-Upgrade 3.17 → 5.0: UI mixed theme, AI pages stuck loading, Marketplace/Playbook Catalog empty + ingestion quota warning in Cortex XDR Discussions
- SD-WAN with ION's running 6.5.1-b5 performance issues in Prisma SD-WAN Discussions
- Get Application Tags via API in Strata Cloud Manager



