- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Azure SAML Authentication with multiple PAs
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Re: Azure SAML Authentication with multiple PAs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Azure SAML Authentication with multiple PAs
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-16-2021 09:18 PM
Hey,
We have a GP configuration with 8 GP Gateways and 2 of them are acting as a GP Portal for backup.
We are using SAML authentication with Azure and wanted to know how to you deploy GP with SAML authentication in large scale.
Currently I have configured 3 SAML apps on Azure one for each PA device but I think it is not the right configuration since now I am getting that each SAML App's domain need to be unique and the Portal domain is for example: vpn.company.com and I need to deploy it to 2 SAML Apps.
My assumptions are that because we only use SP Initiated SAML authentication meaning that the authentication process starts at the PA device I can just add all of the domains that are relevant on a single SAML App and install that Metadata file on all of the Pas. Am I right ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-17-2021 03:35 AM
I just have installed 2 standalone Palo Alto's with SAML. With only 1 Enterprise App in Azure.
So i don't think you need more apps.
Why would you need 2 Apps ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-17-2021 04:05 AM
probably my missunderstanding.
so you have put both of the PA's URLs on the SAML App on Azure ?
and import the metadata to both of the PAs ?
thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-17-2021 05:22 AM
Hi,
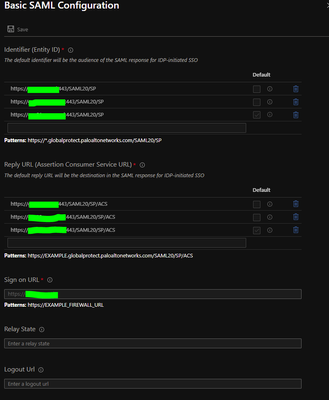
Yes i've add both PA URL's in Azure in the same app, see below.
In our case we use an Azure Loadbalancer for the balanced portal configuration.
That portal points to the direct addresses of the firewall for the gateway connectivity.
See:
The whole point of SSO/SAML is to use a single identity provider/authentication provider (Azure AD in this case) and have multiple serviceproviders (GP Portal and Gateways in this case) use it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-25-2021 12:26 AM
Did you manage to get it working ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2022 12:41 AM
with single enterprise agent deployed you should be fine.
You just need to add multiple Identifier ( each fw for example ) and reply URL
It is working.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-05-2022 03:38 AM
Hi, is this working? I'm trying to implement the same
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-05-2022 03:39 AM
I have added different identifier and still not working,
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-06-2022 01:12 AM
yes it is working as i described, 1 enterprise SAML application with all the domains that your PA are using by the way if you have a lot i thing your can use *.my.domain for example (although i don't think it is best practice)
if you have problems you can try the "miniOrange SAML Tracer" extention maybe you will see the SAML Assertions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-06-2022 11:36 PM
Thank you for the reply, I use the Globalprotect portal in Azure, like this, "vpn-xxx.domain.com" and it's working fine. For gateway , its running in on-prem firewall "vpn-yyy.domain.com" , I have added vpn-yyy.domain.com in the "vpn-xxx.domain.com" ( same Azure Enterprise app) and imported metadata. Still not working. I'll try the fresh installation.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2022 08:29 PM
Hi @BalaBWV , if AAD responds with "invalid identifier" make sure you've included the port in the Entity ID in the Enterprise app like in @sebastianvd's screenshot, i.e. https://vpn-yyy.domain.com:443/SAML20/SP as that is what the auth profile presents to the client / SP in the request. As long as you have both identities and ACS included in the app it should work for both portal and gateway.
- 12440 Views
- 10 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Cert+SAML in GlobalProtect Discussions
- Global Protect Connectivity Issue in GlobalProtect Discussions
- PA Global Protect in GlobalProtect Discussions
- Azure Virtual Desktops integration with Global Protect nightmare in GlobalProtect Discussions
- Global protect multiple authentication methods on same portal in GlobalProtect Discussions