- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Palo Alto DNS Security - Remote Sites
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- Palo Alto DNS Security - Remote Sites
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Palo Alto DNS Security - Remote Sites
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2023 01:19 PM
Hello,
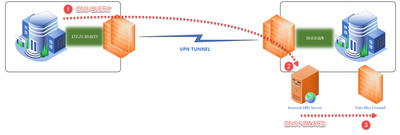
We have a site-to-site hub and spoke vpn setup, Palo Alto being the hub and multivendor spokes.
Is it possible that our remote sites are able to utilize the DNS Security feature installed on Hub for DNS Sinkhole?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2023 01:47 PM
Hi @popoymaster ,
I don't see why not as long as Internet traffic goes through the hub and your AS security profiles are applied to the security policy rules.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2023 01:52 PM
Hi @TomYoung ,
Thanks for your response.
You are talking about backhauling the internet traffic to from remote sites to the hub right?
I don't think that is the direction our client wants to do it.
Thanks,
Wendell
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2023 02:21 PM
Hi @popoymaster ,
Then you would need to at least back haul all DNS requests from remote sites to the hub.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2023 02:26 PM
Hi @TomYoung ,
This is the part we want really full understanding, so pointing users DNS Server to Palo Alto interface?
Will Palo Alto acts as a DNS Server?
Thanks,
Wendell
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2023 02:55 PM
Hi @popoymaster ,
It is sufficient for the DNS traffic to go through the PA. You can configure the remote sites to use the DNS servers at the hub. It is very important that the Anti-Spyware profiles are applied to the traffic.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-14-2023 06:53 PM
Hello all,
Just a side note : make sure all DNS queries are seen by the firewall, not only the request on udp/53.
(thinking about DoH / DoT, more info here https://live.paloaltonetworks.com/t5/blogs/protecting-organizations-in-a-world-of-doh-and-dot/ba-p/3...)
Olivier
PCSNE - CISSP
Best Effort contributor
Check out our PANCast Channel
Disclaimer : All messages are my personal ones and do not represent my company's view in any way.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2023 12:58 AM
Hello Popoymaster,
I never said it is not possible 🙂
(on the webUI, in network, you have "DNS Proxy").
And Tom suggested there was no requirement for carrying the DNS service, as long the firewalls inspect the traffic, DNS Security (if licensed) can inspect the queries and sinkhole risky domain names.
The issue I raised : if an user (tech-savy) changed the DNS, you lost the control on those traffic.
(and actually, an attacker on a compromised machine can change it as well).
Olivier
PCSNE - CISSP
Best Effort contributor
Check out our PANCast Channel
Disclaimer : All messages are my personal ones and do not represent my company's view in any way.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2023 04:02 AM
That is what exactly we want to implement, to push the traffic from remote sites going to the HUB, and let the Palo Alto do DNS Sinkholing (Licensed).
So my question is how? I am thinking to provision a DNS Server in the HUB, then that DNS Server push the DNS Query through PA for inspection.
Thanks,
Wendell
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2023 06:38 AM
ok @popoymaster
I don't see any issue then.
You make sure the traffic is going to the Central site (static default route or advertising the default route over some routing protocol between the central site and the remote sites)
And you simply have to set the anti-spyware profile for the traffic (remote site> any) on the PANW firewall.
The DNS Sec is configured in the anti-spyware profile.
Also if you have read the link I shared earlier, you may take measure regarding DoH and DoT.
Olivier
PCSNE - CISSP
Best Effort contributor
Check out our PANCast Channel
Disclaimer : All messages are my personal ones and do not represent my company's view in any way.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2023 11:46 AM
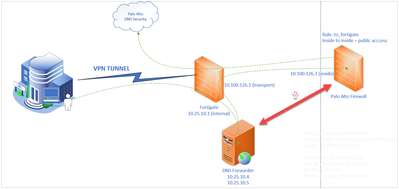
@ozheng ,
Our VPN concentrator is Fortigate, it has 2 vlans, Internal and Transport.
Internal where the DNS Server resides.
Transport is connecting to the Inside interface of the Palo Alto.
Now, how is it possible to forward the traffic from Internal DNS Server and point to Palo Alto for DNS Security Filtering?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2023 01:22 PM
Hello,
If you are not backhauling all the traffic from the remote offices then you should have all the security features enabled on all of the Palo Alto's. In this case all will be able to perform threat detection etc. Here is a video for secure DNS made a few years ago that will work regardless if you backhaul or dont. Just make sure to use the secure DNS providers IP's for DNS.
https://www.youtube.com/watch?v=ROIAYSEbTuo
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2023 01:33 PM
Thanks @OtakarKlier, great video there.
Our client's External DNS (Cisco Umbrella) is expiring soon, so they want to utilize the Palo Alto DNS Security, problem is im having some trouble figuring how to route remote sites to use the Central Site's Palo Alto.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2023 01:43 PM
Hello,
You dont need a license to use the basic features of Umbrella, eg already known bad sites. You just dont get a dashboard and customizable DNS filtering. From my understanding of the topology, not all the sites have Palo Alto devices. In this case, I would recommend a backhaul to the central site and let that device handle all the filtering etc. This is a common practice to save on costs at the remote offices, just increase bandwidth at the central location (bandwidth is cheap compared to all the licensing costs for each site). Also can help if you have any type of regulations you need to adhere to since all sites now have a secure and filtered connection to the internet. Here is what CISA has to say about this topology: https://www.cisa.gov/resources-tools/resources/trusted-internet-connections-tic-30-core-guidance-doc...
Here is another write up about zero trust that you might have a look at: https://skrzsecurity.net/zero-trust
Cheers!
- 5444 Views
- 14 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- GUEST WIFI for new client in Next-Generation Firewall Discussions
- HA Links Over DWDM in Next-Generation Firewall Discussions
- Admin GUI Login Fails on WAN Interface - Slow Load & "Single Sign-On" Error on PA-410 in Panorama Discussions
- NGFW Blocking Router Login Traffic After Policy Update – Requesting Guidance in Next-Generation Firewall Discussions