- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Panorama (eth1/1) to firewall (Loop0 or vlan interface) configuration push
- LIVEcommunity
- Discussions
- Network Security
- Panorama Discussions
- Re: Panorama (eth1/1) to firewall (Loop0 or vlan interface) configuration push
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-27-2021 11:42 PM
Panorama (eth1/1) to firewall (Loop0 or vlan interface) configuration push
Hey guys
Not sure if it's a valid solution but I need your advise.
Panorama - M500
FW - PA3220
Scenario 1: Panorama (MGT Interface) <---------- (MGT Subnet) ----------> (MGT Interface) Firewall
- can push the config from Panorama to FW
- everything works, no issues.
Scenario 2: Panorama (Eth1/1 ) <---------- (Routed network) ----------> (Loop0) Firewall
- cannot push the config from Panorama to FW,
- even though they can ping to each other.
- can't see the firewall in Managed Device either.
Panorama eth 1/1 -settings
- Ping,
- SSH,
- Device Deployment,
- Device Management and Device Log Collection,
- Device Deployment
Could someone advise what's missing in my config or this is not possible?
Followed this post, looks like similar config worked for someone but not sure whether MGT interface was used or something else.
Solved: LIVEcommunity - Re: Panorama device management via loopback - LIVEcommunity - 341279
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-28-2021 03:13 PM
Thank you for posting question @sanjaypatel08
I have a few Firewalls that are managed by Panorama and not using management interface. This scenario is possible, you will only have to adjust Service Route Configuration to use Loopback interface instead of management interface. I can confirm that in Panorama the Firewall's IP address will be still displayed with management interface IP address even though it is not connected at all.
On Panorama side, I do not think you can completely eliminate Management interface. Based on documentation it states that: "When assigning Panorama services to various interfaces, keep in mind that only the MGT interface allows administrative access to Panorama for configuration and monitoring tasks."
For all other functions such as:
Device Management and Device Log Collection
Collector Group Communication
Device Deployment
You can use different interface than management. This should be functional in your case with Eth 1/1.
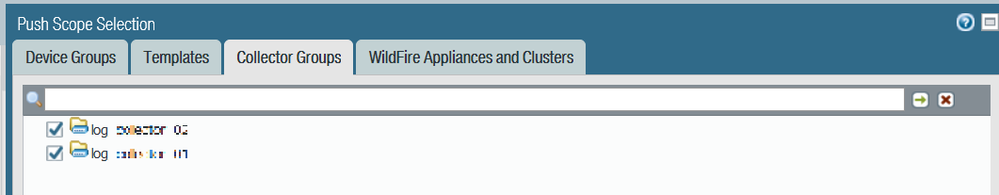
Could you make sure that you completed this step: Changes made to interfaces other than management (MGT) require a Collector Group commit to be effective. Below is a sample:
Since you mentioned that you can't see Firewall in Panorama under Device Management, this is fundamental issue and without seeing Firewall connected in Device Management, you will not be able to perform further tasks with pushing of configuration. Could you verify that on Firewall side you are pointing to the correct Panorama's IP address, Service Routes are in place and S/N registered in Panorama is corresponding?
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-05-2021 02:38 PM
Thanks @PavelK for your help, I followed the steps and it did work for me.
I had to make two changes:
1. The service route update from firewall
2. After seeing the traffic from firewall to Panorama eth1/1 interface, firewall was dropping it so I had to create another rule allow that flow.
And it worked well, with no issues 🙂
Thank you again!
Sanjay
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-28-2021 03:13 PM
Thank you for posting question @sanjaypatel08
I have a few Firewalls that are managed by Panorama and not using management interface. This scenario is possible, you will only have to adjust Service Route Configuration to use Loopback interface instead of management interface. I can confirm that in Panorama the Firewall's IP address will be still displayed with management interface IP address even though it is not connected at all.
On Panorama side, I do not think you can completely eliminate Management interface. Based on documentation it states that: "When assigning Panorama services to various interfaces, keep in mind that only the MGT interface allows administrative access to Panorama for configuration and monitoring tasks."
For all other functions such as:
Device Management and Device Log Collection
Collector Group Communication
Device Deployment
You can use different interface than management. This should be functional in your case with Eth 1/1.
Could you make sure that you completed this step: Changes made to interfaces other than management (MGT) require a Collector Group commit to be effective. Below is a sample:
Since you mentioned that you can't see Firewall in Panorama under Device Management, this is fundamental issue and without seeing Firewall connected in Device Management, you will not be able to perform further tasks with pushing of configuration. Could you verify that on Firewall side you are pointing to the correct Panorama's IP address, Service Routes are in place and S/N registered in Panorama is corresponding?
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-05-2021 02:38 PM
Thanks @PavelK for your help, I followed the steps and it did work for me.
I had to make two changes:
1. The service route update from firewall
2. After seeing the traffic from firewall to Panorama eth1/1 interface, firewall was dropping it so I had to create another rule allow that flow.
And it worked well, with no issues 🙂
Thank you again!
Sanjay
- 2 accepted solutions
- 5177 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect Connectivity Issue in GlobalProtect Discussions
- Palo Alto to Azure vpn tunnel fails at random in Next-Generation Firewall Discussions
- How to configure LACP at PA-440 firewall in Next-Generation Firewall Discussions
- GloablProtect + Explicit Proxy blocks WSL traffic. in GlobalProtect Discussions
- AI for FW management in Next-Generation Firewall Discussions