- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Standalone Prisma Access and LDAP Group Mapping
- LIVEcommunity
- Discussions
- Secure Access Service Edge
- Prisma Access Discussions
- Standalone Prisma Access and LDAP Group Mapping
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2020 08:04 AM
I'm trying to implement group-based policies in a standalone Prisma Access deployment. The instructions for achieving this are really lacking. Can anyone clarify how to configure group based policy mapping on standalone Prisma Access deployments with no master device?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2020 11:57 AM
Hi Raymond,
To configure standalone group mapping, you need to have the following configured under the mobile users' template:
Please note that in a standalone scenario, you won't be able to pull the group-names on Panorama GUI. Therefore, you will have to type as per the instructions from your comment the DN long format entry in your policy and configuration.
For testing purposes, you can create a security policy, set the policy on the top and deny traffic to a specific IP to a specific group, this is just one example of many ways you can test.
Please let us know if you have any further questions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2020 08:06 AM
Unclear instructions from the KB article:
Implement User-ID in Security Policies For a Standalone Prisma Access Deployment In a standalone Prisma Access deployment without a Master Device, you can use group-based policy using long-form DN entries in Panorama. Prisma Access uses the DN entries to evaluate the User-ID-based policies you have configured in Panorama. For example, given a User named Bob Alice who works in IT for Organization Hooli in the United States, a matching security policy may have ou=IT Staff,O=Hooli,C=US if the policy is to be applied to all IT staff, or CN=Bob Alice,ou=IT Staff,O=Hooli,C=US if the policy is only to be applied to Bob Alice.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2020 11:57 AM
Hi Raymond,
To configure standalone group mapping, you need to have the following configured under the mobile users' template:
Please note that in a standalone scenario, you won't be able to pull the group-names on Panorama GUI. Therefore, you will have to type as per the instructions from your comment the DN long format entry in your policy and configuration.
For testing purposes, you can create a security policy, set the policy on the top and deny traffic to a specific IP to a specific group, this is just one example of many ways you can test.
Please let us know if you have any further questions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2020 06:11 PM
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-12-2020 09:38 AM
Hi @RaymondMullin, that is correct.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-12-2020 10:29 AM
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-12-2020 11:05 AM
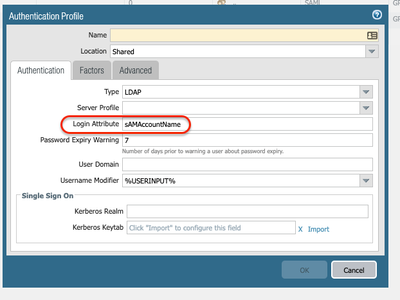
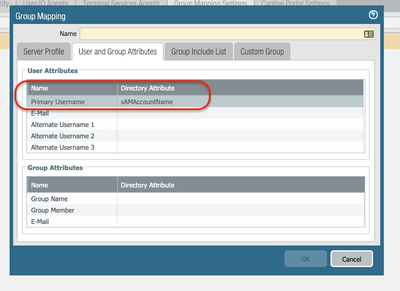
The user mapping should always work because the userid is learned from the authentication.
Whereas in the case of the group mapping, we need to pull the information from your LDAP server and group-mapping configuration.
Hence, the group-mapping attribute fields need to be aligned to the user authentication profile attributes.
Here is an example:
If you are using sAMAccountName on your Authentication Profile, make sure you add the same format on your Group-Mapping configuration.
- Best practice configuration:
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/user-id/map-users-to-groups.html
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2020 07:50 AM
Thanks for all the help. It's working now with the long form.
- 1 accepted solution
- 12965 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access CIE and User-ID mapping not working for groups in Prisma Access Discussions
- The user information linked in the CIE does not match the match criteria in the GP's application settings. in Prisma Access Discussions
- Bidirectional User-id redistribution between Prisma access and on-prem Firewalls in Prisma Access Discussions
- Prisma Access with CIE in Prisma Access Discussions
- Incidents coming empty to ServiceNow from Prisma Strata Cloud Manager in Prisma Access Discussions