- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
- LIVEcommunity
- Get Started
- News & Events
- Events
- Ask Me Anything (AMA) Event Discussions
- Who rated this post
Who rated this post
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-29-2021 11:13 AM - last edited on 08-05-2021 02:16 PM by jdelio
@jforsythe wrote:
What’s the number one thing individuals aren’t doing but should to secure their virtual worlds?
From my perspective, the answer would be, believing that their current rule sets are properly configured and providing adequate projection.
The typical IT professional is very busy through his/her day, and there never seems a moment in time to just re-prioritize and focus on your current security posture.
Example:
Can someone, right now, tell me EXACTLY how many application their network has seen in the past 30 days.
Can you tell me if all of these applications are needed (think.. Acceptable Use Policy of your employer...) just because someone uses an application does not mean it is a business justified one.
Do you have rules limiting the risk level of your applications?. There are 143 Risk Level 5 applications detected by the PANW FW. Have you reviewed the 143? Do you have security rules/posture to block the apps that are not being used?
If you look at your application usage and only three risk level 5 (say, FTP, SMTP, and Skype) are needed... and you do not see any other risk level 5 in your network... are you actively creating policies to BLOCK the apps that your enterprise is not even using.
This is called "Reducing the Attack Surface"
There are 3563 applications known on the PANW appliance. Have you taken the time to review the application and appropriately TAGGED the application using the "Sanctioned" tag. Imagine how easy your security policy could be if you only allowed SANCTIONED applications? Your security rules numbers could be easily reduced.
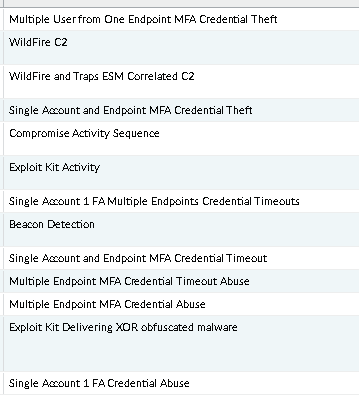
For those with Panorama... are you looking and utilizing the the Automated Correlation Engine? If the Panorama is the "single pane of glass" to your security posture, have you reviewed its output against these events:
And lastly, when was the last time your company ran its configuration through the PANW created Best Practice Assessment tool, available in your support account. It takes your configuration and finds EVERY single area of improvement that needs to be performed (according to the recommendations of PANW_ to secure and improve the posture of your network. Perform these 2 to 4 times a year, to keep current.
The list could go on, in ways to improve. Review the CyberElite comments and take advantage of the knowledge and experience from these experts.