- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
EDL - Talos block list
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: EDL - Talos block list
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
EDL - Talos block list
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-18-2017 03:24 AM
I have various EDLs setup on various different PA models. Some work, and populate the list with IP's and effectively block in security policies. However, for Cisco Talos block list, it just will not work:
http://www.talosintelligence.com/feeds/ip-filter.blf
It won't populate the list at all when I request to see the list I get:
vsys1/Cisco Talos IP Black List:
Next update at : Tue Sep 19 02:08:23 2017
Source : https://www.talosintelligence.com/feeds/ip-filter.blf
Referenced : Yes
Valid : Yes
Auth Valid: Yes
Total invalid entries : 1
Valid ips:
No error
Service route is set, as other EDLs work fine. All I can think is that this Talos URL resolves to an Amazon AWS address. It still won't work if I tinyurl that AWS address, and add that as the EDL.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-28-2017 07:43 AM
Had same issue, try changing URL in EDL to https://talosintelligence.com/documents/ip-blacklist and in CLI run
request system external-list refresh type ip name "Cisco Talos IP Black List"
Give it a second, then try
request system external-list show type ip name "Cisco Talos IP Black List"
post results.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-28-2017 08:37 AM - edited 09-29-2017 05:39 AM
Assuming you're running Windows, here's a quick and dirty powershell script I just wrote to download the list for internal hosting. It gets the content, dumps it to CSV file without headers, which I found I had to do otherwise if I just dumped it to a text file, it was one compelte stream of text without any carriage returns, instead of seperate IP addresses. Throw that file on an internally hosted website dedicated for hosting firewall blacklists, and use IP restrictions so only your firewall can pull the data. I also do this for IP addresses I want blocked for longer than the built in max of one hour.
Try not to run the script more than once per hour once it's working so they don't temporarilly block you. Change the foldername to the name of the site in IIS.
$talos = 'C:\inetpub\wwwroot\NAMEOFINTERNALWEBSITE\talosTemp.csv'
Invoke-WebRequest -uri https://talosintelligence.com/documents/ip-blacklist -OutFile C:\inetpub\wwwroot\NAMEOFINTERNALWEBSITE\talosTemp.csv
if((gc $talos | Measure-Object).count -gt 100){
gc -path $talos | Out-File C:\inetpub\wwwroot\NAMEOFINTERNALWEBSITE\talos.txt -Force -ErrorAction SilentlyContinue -Encoding ascii
}
This is very rudamentary, but it is working for me so far.
EDIT: forgot to add the ascii encoding, feel free to tweak it how you see fit, add more conditional logic as needed, that measure-object is just there to make sure the file isn't empty.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-07-2017 11:10 AM
You might want to give MineMeld a try. Either the community version or the AutoFocus hosted one would do the job.
Deatails on how to mine this list at https://live.paloaltonetworks.com/t5/MineMeld-Discussions/Talos-Blacklist/td-p/190671/jump-to/first-...
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-08-2017 05:51 AM
EDL download by firewall only works if the web server which hosts the file allows TLS1.0 connections. The firewall does not support higher TLS versions for EDL downloads.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-30-2019 12:42 PM
Yes, I do realize this is an older thread but here is what I experienced:
I can open the URL in a browser and see the list of IPs. The firewall does not download the list even though it recognizes the URL. The base URL as published redirects to a much longer URL that changes frequently with updates. That much longer URL is more than the 255 character limit for the URL field. I believe the redirect is where my issue lies. When I try to edit the exclusion list after refreshing the list there are no entries thus I never get a list.
Maybe this can help someone else.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2020 03:17 PM
Hello,
Try it with http instead of https.
Just a thought.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-07-2020 01:01 AM
Hello,
URL : https://www.talosintelligence.com/feeds/ip-filter.blf won't populate the list as it is giving 'URL Access error' when i do Test source URL on firewall. Now when i am browsing above url, it is getting redirected to amazon aws link. If we even try to put redirected URL to Test it on firewall, it will not allow as URL is crossing 255 characters, and palo alto can accept at most 255 under url-test node under EDL.
So this may be the issue here.
- Mayur
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-16-2020 06:54 PM
@solarstoneIs it resolved ?
Mayur
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-05-2022 07:37 AM
I have the same problem, I tried the refresh by cli and had this return:
Details:EDL(vsys1/Dynamic_List_Talos ip) Unable to fetch external dynamic list. No error. Using old copy for refresh.
EDL(vsys1/Dynamic_List_Talos ip) Manual Refresh job success
When I test it through the GUI it returns URL access error
The url I'm using is https://talosintelligence.com/documents/ip-blacklist
Another point that only a few days ago we started to receive the log in system Unable to fetch external dynamic list. No error. Using old copy for refresh.
was there any kind of change?
what was the solution to this problem?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-24-2022 12:39 PM - edited 12-24-2022 12:40 PM
Hi @Adriano_R94 ,
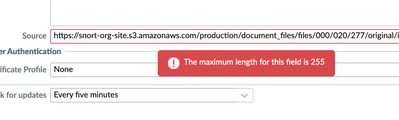
As @SutareMayur says, I believe that the problem is that the above URL redirects to an AWS URL which is 373 characters long. The maximum size for the EDL Source field is 255, which I think is applied redirects also. To demonstrate, I pasted the AWS URL in the field below:
I solved this problem by fetching the Talos list here -> http://opendbl.net/. It has the update date. I did a quick count now on the Talos list, and it had 741 IP addresses just as OpenDBL says.
Thanks,
Tom
- 26880 Views
- 10 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Aug-Sep, 2025 in Advanced WildFire Discussions
- Port 5060 Remains Blocked Despite Threat Exemption in Advanced Threat Prevention Discussions
- EDL Dynamic Domain list that is allowed in Anti-spyware profile> DNS Polices is getting sinkholed in Advanced Threat Prevention Discussions
- Blocking Scammer website (cryptocurrency) in Advanced Threat Prevention Discussions
- OneNote Extension File blocking in Advanced Threat Prevention Discussions