- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Exclude all Zoom traffic from GlobalProtect VPN
- LIVEcommunity
- Discussions
- General Topics
- Exclude all Zoom traffic from GlobalProtect VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-17-2020 03:24 AM
We have been trying to exclude all Zoom-related traffic from the GlobalProtect VPN tunnel.
So far we have tried with: "*.zoom.us" exclusion configured directly on the GP gateway as a domain in:
Network --> GlobalProtect --> Gateways --> GW NAME --> Agent --> CLient Settings --> Split tunnel --> Domain and Application
But this seems to not completely do the trick as Zoom use some AWS default domains, not under *.zoom.us.
What approaches will work that does not involve having to manually exclude all the IP ranges as defined here?
The Zoom binary path seems to be this one, but I'm not sure PA supports wildcards on the path like this:
C:\Users\*\AppData\Roaming\Zoom\bin\Zoom.exe
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2020 03:07 AM
Hi,
This config is working just fine for me.
The config was tested on PAN-OS 0.04 and PAN-OS 9.0.6 and it's working in both cases.
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2020 03:17 AM
What GlobalProtect version are you using?
We did some more tests and we conclude with: Win10 and:
- With Global Protect 5.1 is working fine
- We are not yet sure about GlobalProtect 5.0
- With GlobalProtect 4.1 is not working
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2020 04:13 AM
We are using GlobalProtect client version 5.0.2
Thanks
.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2020 04:10 AM
Hi,
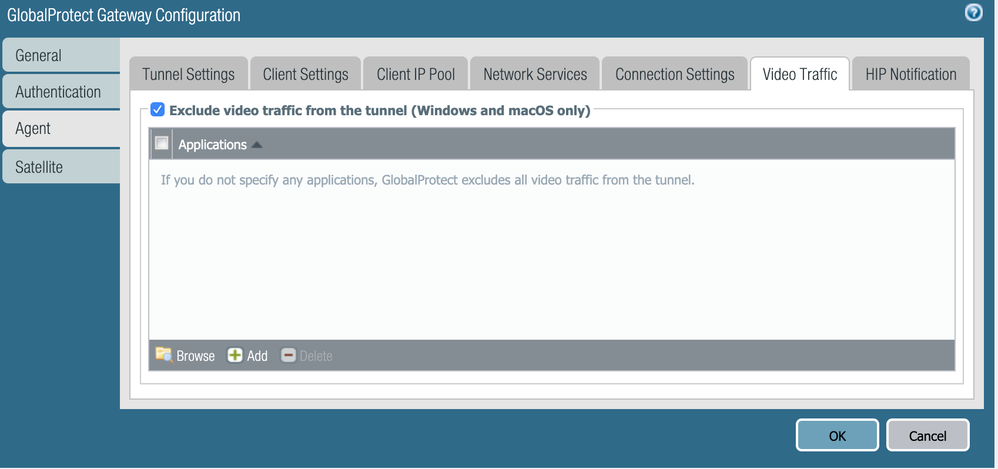
Did you get the feature exclude video traffic from vpn tunnel to work?
For me, I'm sure we are using the correct config and we upgraded the GlobalProtect Gateway appliance to PAN-OS 9.0.6 ( the issue was fixed in this release) but still no positive result.
I went through debug and dump logs. Checked the monitoring tab in the PA and I'm still seeing the video streaming traffic go across the tunnel (dailymotion for example).
I opened a case with support but still no answer yet.
Any help will be appreciated.
In case we find a solution with the support team I will share it here
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2020 06:13 AM
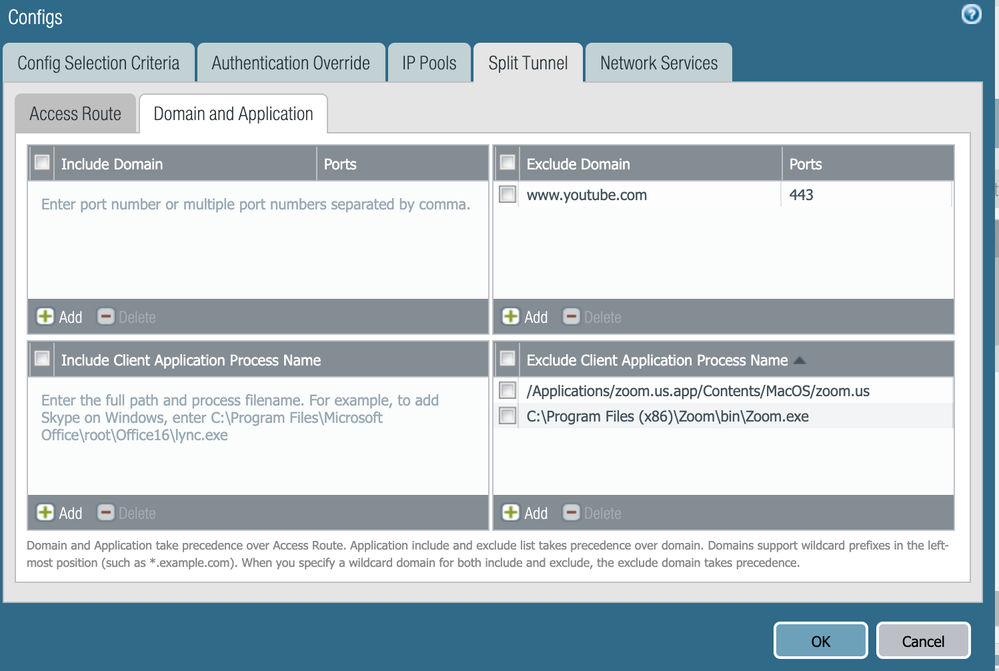
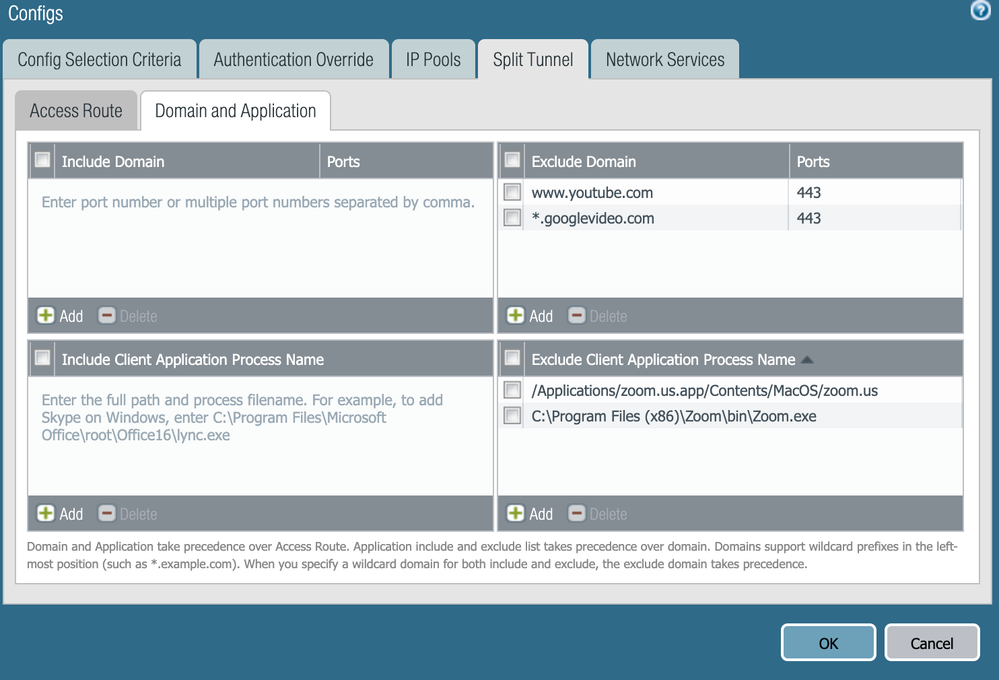
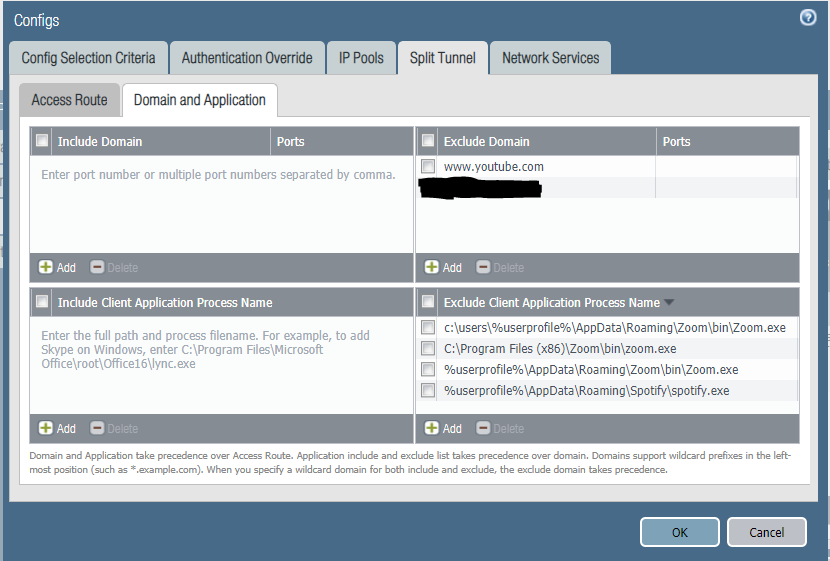
Try configuring both the "Exclude Video Application" option on agent and also domain name under exclude domains. Can you share a screenshot of config
~ Sai Srivastava Tumuluri ~
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2020 06:49 AM
The simple trick I use is following
Method 1
- Go to URL logs and filter the traffic of interest
- The domain the URL logs, is the domain I would recommend to match
Method 2
Wireshark capture
Following is the screenshot I saw for youtube, try adding regex around Youtube
~ Sai Srivastava Tumuluri ~
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2020 06:05 PM
Hi,
Same issue here GP version 5.1.1-12
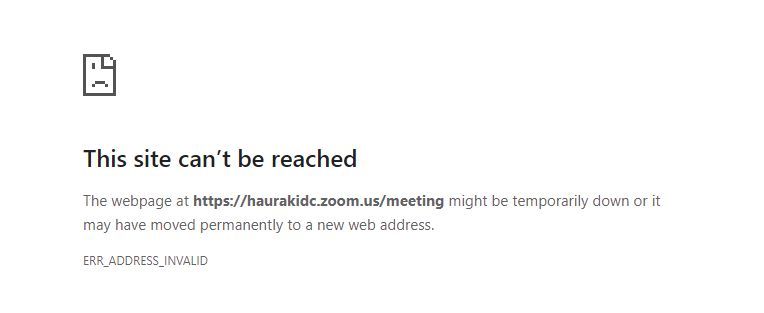
Have added both the Program files and AppData paths to the exclude client apps but udp 8801 is still traversing the VPN. ALso if i add *.zoom.us to teh exclude domains and open a web browser the site errors as below. take it out and good to go again.
Any ideas?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2020 04:03 PM - edited 03-27-2020 06:24 PM
Hello Everyone,
I have tested this on 5.0.8 and 5.1.1 and got a successful result.
When tested, I closed the zoom app before connecting to Prisma Access VPN, upon connecting, I opened the zoom client and join a meeting.
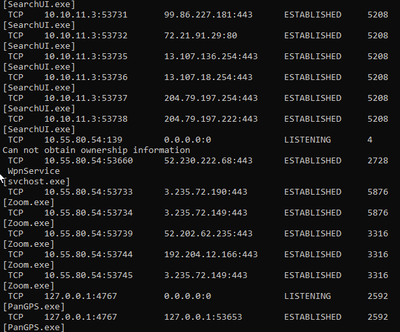
Here is an example of the "netstat -anob" output from my windows machine:
10.10.11.3 is my Prisma Access GP IP and 10.55.80.54 is my local (physical interface) IP.
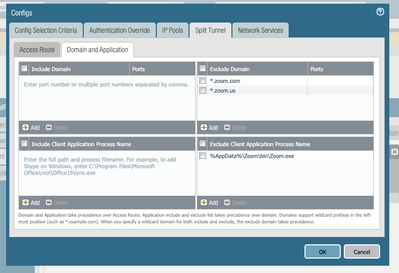
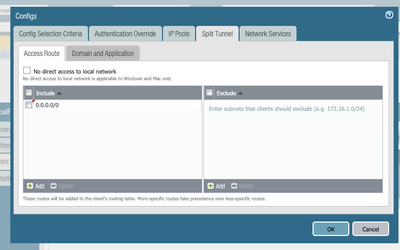
This is how my configuration looks like:
I also tried adding the 0.0.0.0 on the include list, and the result was the same.
If you are still having issues, please open up a tac case and a member of our team will be more than happy to assist troubleshooting this issue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2020 05:32 PM
Everyone,
Can you start a zoom meeting with screen sharing and video ON. Add at least 2 people with video
While on meeting run - netstat -aenob
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClQjCAK
Also, for IPs in the traffic logs, enable host lookup, by checking the box at the bottom. Resolve hostname. And share the screenshot again. The above link will help
========================
You can open tac case with the above information or update it here
~ Sai Srivastava Tumuluri ~
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-31-2020 12:53 AM
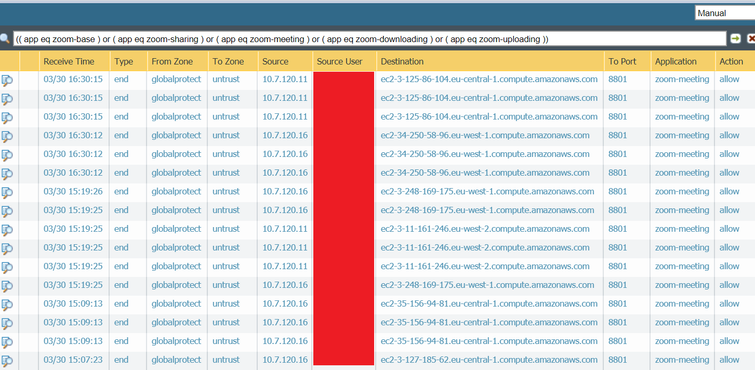
Did some more tests and I can see that all traffic going through the tunnel is:
- Going to port udp/8801
- It belongs to IP network ranges not defined here, as far as I can see:
( addr.dst in 3.125.86.104 )
( addr.dst in 34.250.58.96 )
( addr.dst in 3.248.169.175 )
( addr.dst in 3.11.161.246 )
( addr.dst in 3.127.185.62 )
( addr.dst in 52.211.174.178 )
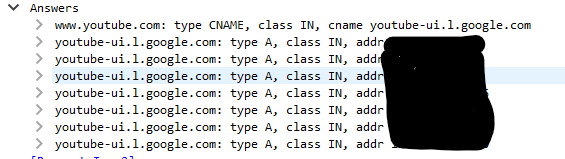
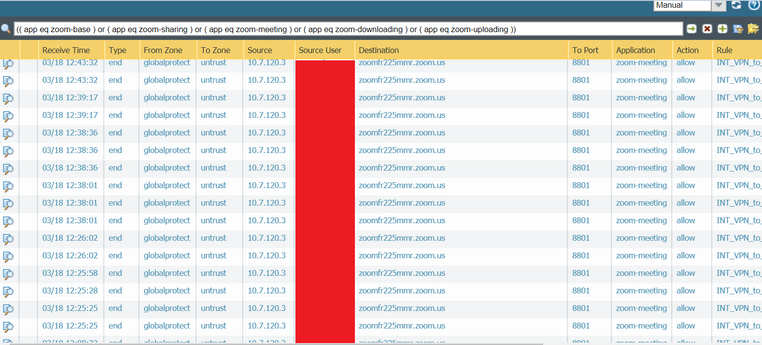
The screenshots you were asking for: most of them resolves as amazonaws.com domain, but some other resolves as zoom.us domain too:
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-03-2020 09:07 PM
I am trying setting up to split zoom traffic via physical adapter following the link. All traffic goes thru tunnel except zoom.
I am not able to get it work without adding route in excluded access route. We have Gateway subscription license but not portal license.
Just want to confirm if we follow the following link (not mention adding route in excluded tab), Link says it needs Global protect license, Is it portal license or just gateway subscription license
Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-03-2020 11:31 PM
Hi Daniel Li,
You need a GlobalProtect subscription for the following feature:
Split tunneling based on destination domain, client process, and video streaming application.
Excluding routes does not require an additional license.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2020 08:36 AM
Thank you SuperMario for the reply.
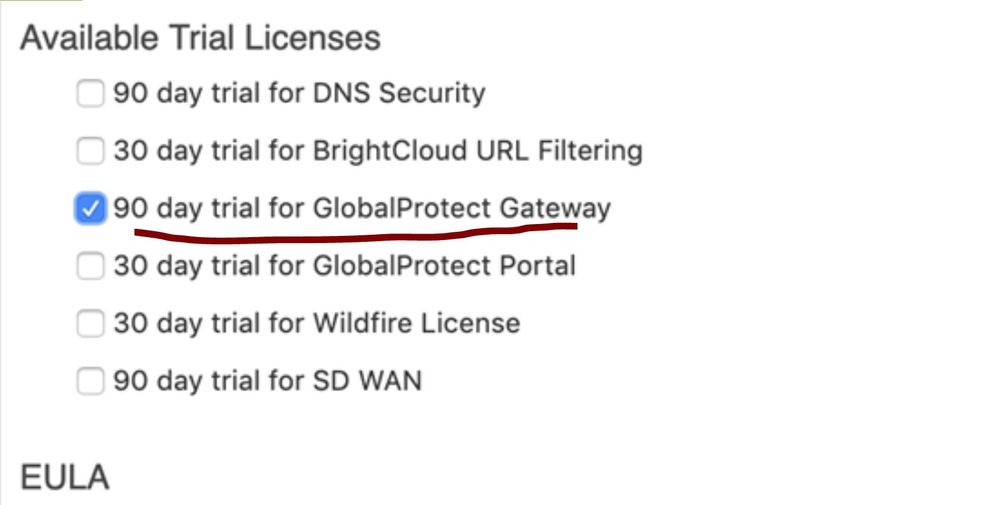
I have installed 90 days trial Global protect gateway. Is that enough ? It does not work after following the link. tracert zoom.us on Window 10 shows going thru tunnel interface, not physical one ( restart GP service a few time, no access route configured ), I use GP 5.1 for window client. Any suggestion is appreciated
Configuration is used in the link
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2020 08:39 AM
HI Sai
I installed 90 days trial Global protect gateway. Is that enough ? It does not work after following the link. tracert zoom.us on Window 10 shows going thru tunnel interface, not physical one ( restart GP service a few time, no access route configured ), I use GP 5.1 for window client. if add route in excluded access route. it works but zoom.us IP is changing sometime. Any suggestion is appreciated
Configuration is used in the link
- 69035 Views
- 59 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Always-On (6.3.3-c711) – Users Stuck in “Connecting” State but Still Have Internet Access in General Topics
- GloablProtect + Explicit Proxy blocks WSL traffic. in GlobalProtect Discussions
- linux /etc/iproute2/rt_tables filled with 231 pangp.include and 232 pangp.exclude in GlobalProtect Discussions
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions
- Globalprotect VPN assign a public IP to an internal server in GlobalProtect Discussions