- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
BPA Release Notes v3.14
- LIVEcommunity
- Community Legacy Content
- Best Practice Assessment
- Best Practice Assessment Release Notes
- BPA Release Notes v3.14
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 07-11-2019 07:59 AM - edited on 07-29-2019 09:12 AM by Retired Member
Security Rule Hit Count
New Feature
Details: This tracks how often traffic matches the policy rules you configured on the firewall. It also identifies the inactive rules. When enabled, you can view the total Hit Count for total traffic matches against each rule along with First Hit and Last Hit.
API Key Lifetime
New Feature
Details: Set the API key lifetime to protect against compromise and to reduce the effects of accidental exposure. To ensure that your keys are frequently rotated and each key is unique when regenerated, you must specify a validity period that ranges between 1-525,600 minutes. Refer to the Audit and Compliance policies for your enterprise to determine how you should specify the lifetime for which your API keys are valid.
Server Monitoring Transport Protocol
New Feature
Details: Using the Windows Remote Management (WinRM) protocol greatly improves the speed, efficiency, and security when monitoring server events to map usernames to IP addresses. Leverage one of the WinRM protocols to monitor Active Directory Windows Servers 2008 or Microsoft Exchange Servers 2008 or later.
Time to Refresh FQDN
New Feature
Details: Set a limit on how fast the firewall refreshes FQDNs that it receives from a DNS. This check ensures the FQDN is not outdated by setting refresh interval at default 30 sec.
GRE Tunnel Keep-Alive
New Feature
Details: Configure Keep-Alive on the GRE Tunnel to ensure stability and monitoring of tunnel activity.
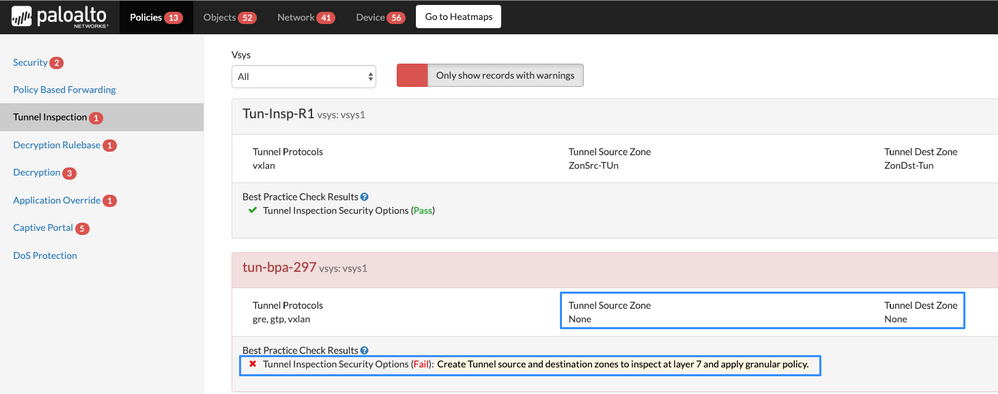
Tunnel Inspection Security Options
New Feature
Details: The best practice is to create tunnel zones for your tunnel traffic. Thus, the firewall creates separate sessions for tunneled and non-tunneled packets that have the same five-tuple (source IP address and port, destination IP address and port, and protocol). By doing so, we can inspect at Layer 7 for Applications, Threat, URL filtering and apply granular policy conditions to permit just the right traffic.
Inter-vsys User-ID Data Sharing
New Feature
Details: To simplify User-ID source configuration if you have multiple virtual systems, you can now share user mappings across virtual systems. To share User-ID IP address-to-username mappings, choose a virtual system to use as a User-ID hub that collects and stores the mappings in a centralized table that is accessible by all the virtual systems. This helps in not retaining the same user IP addresses multiple times on the firewall for each single vsys. This also helps in increasing the User-ID limit on the device by not retaining the same names multiple times.
WildFire File Size Limits Updated for PAN-OS 9.0
Enhancement
Details: The best practice file size limit for each file type has changed for PAN-OS version 9.0. We have updated the checks with new file sizes as per best practices for PAN-OS 9.0.
- API Key Lifetime
- best practice assessment
- BPA
- GRE Tunnel Keep-Alive
- Inter-vsys User-ID
- PAN-OS 9.0
- Refresh FQDN
- Security Rule Hit Count
- Server Monitoring Transport Protocol
- Tunnel Inspection Security Options
- wildfire
- 3042 Views
- 0 comments
- 0 Likes
- New Ransomware URL Filtering Category (BPA Version 7.3.0) in Best Practice Assessment Release Notes
- BPA Release Notes (Version 6.4.0) in Best Practice Assessment Release Notes
- BPA Release Notes (Version 6.3.0) in Best Practice Assessment Release Notes
- BPA Release Notes (Version 6.2.0) in Best Practice Assessment Release Notes
- BPA Release Notes (Version 6.1.2) in Best Practice Assessment Release Notes