
- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources

This blog written by Omri Itzhak.
The new Cortex XDR Lite - Incident Handling playbook is a new addition to the Palo Alto Networks Cortex XDR - Investigation and Response content pack. Used as the default playbook in this content pack, it streamlines incident response workflows for Cortex XDR incidents ingested into XSOAR, automating manual tasks associated with the enrichment, investigation and resolution of Cortex XDR incidents. Easy to deploy and with no additional integrations needed, this playbook can significantly reduce the time your analysts spend remediating XDR incidents.
The Cortex XDR Lite Incident Handling playbook is triggered by fetching a Palo Alto Networks Cortex XDR incident and includes sub-playbooks and tasks that facilitate analyst investigation by automating responses to Cortex XDR incidents.
The Palo Alto Networks Cortex XDR - Investigation and Response integration fetches Cortex XDR incidents and triggers the Cortex XDR Lite - Incident Handling playbook for each incident.
First, the playbook retrieves data fields of the specific XDR incident, including a list of alerts with multiple events, alerts, and key artifacts.
Enrichment
For automated data enrichment, the playbook uses the Entity Enrichment Generic v3 sub-playbook which takes all the entities in the incidents and enriches them with the available products in your environment.
Investigation
To aid incident investigation, the playbook uses the Command-Line Analysis sub-playbook to analyze the command line to determine if command line usage was malicious or suspicious based on the following findings:
The playbook also uses the Cortex XDR - Get entity alerts by MITRE tactics sub-playbook to search for XDR-related alerts with a medium severity or higher, based on MITRE ATT&CK tactics used to identify malicious activity performed on the endpoint, or by the user.
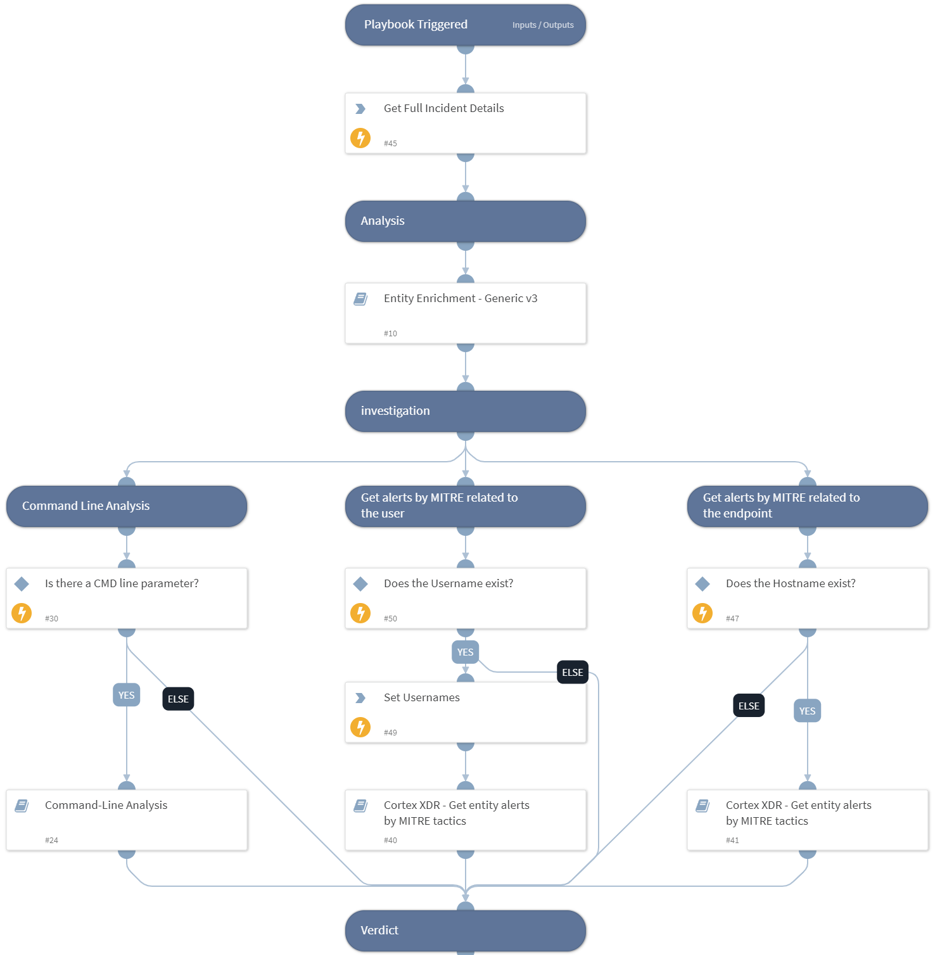
Verdict
Based on the analysis and the investigation results, the playbook determines the incident severity by considering indicator enrichment data, user and host risk levels, command line analysis verdict, and the number of related XDR alerts (medium severity or higher) to the user and the endpoint mapped to MITRE ATT&CK tactics.
If the verdict for the incident is not definitively malicious (based on the enrichment and investigation tasks), an analyst will need to determine whether the incident is malicious or not - by looking at all the details gathered by the playbook and presented in the layout.
Response Actions
If an incident verdict is set to malicious, the playbook will perform remediation actions, isolating the endpoint and blocking all the indicators that were extracted from the incident either manually or automatically using the Block Indicators - Generic v3 sub-playbook. Upon completion of the remediation stage, the playbook will close the incident.
If the incident verdict is set to benign, the playbook will close the incident.
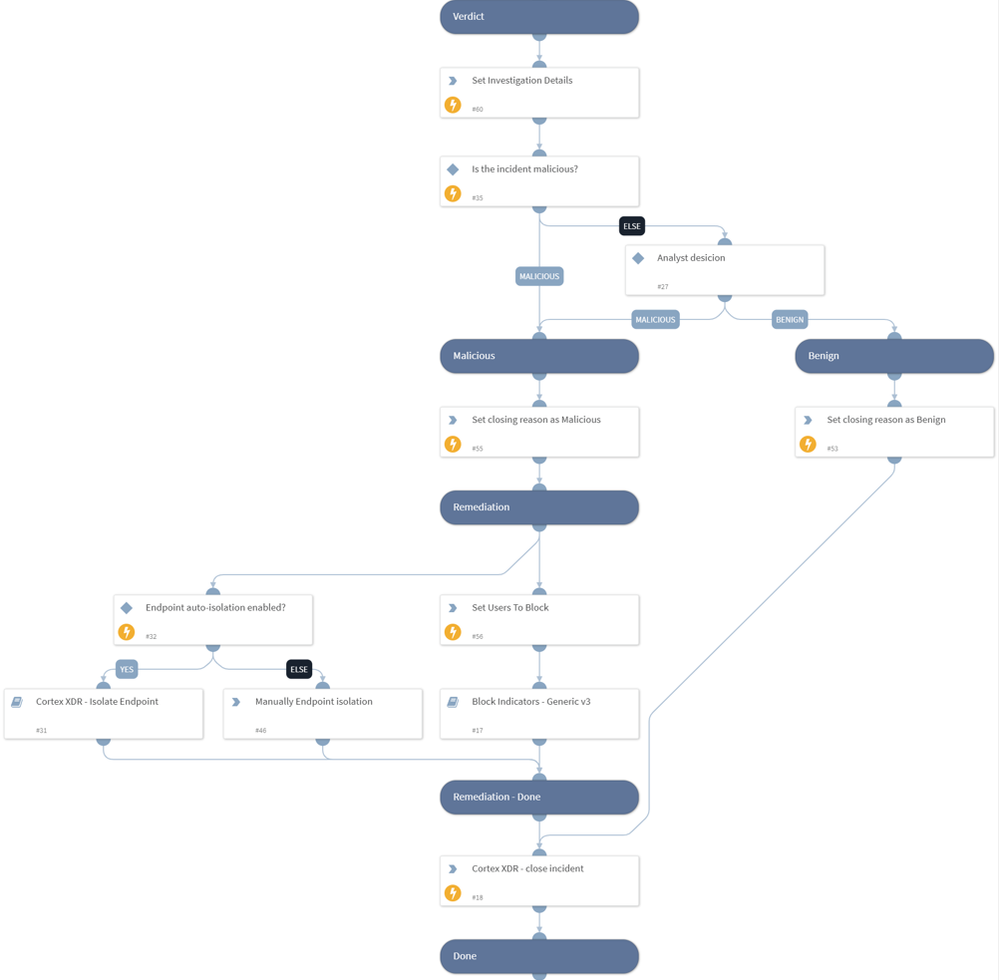 The Verdict & Response section of the workflow
The Verdict & Response section of the workflowThe Verdict & Response section of the workflow
As part of this playbook, a comprehensive layout that presents incident details, analysis, investigation findings, and the final verdict is provided out-of-the-box. Additionally, the layout offers convenient remediation buttons for quicker manual actions.
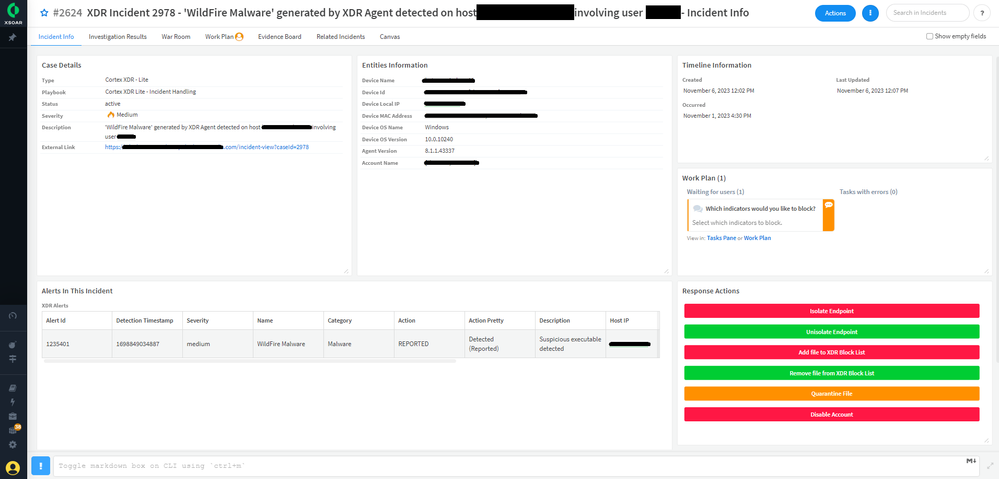
The Incident Info tab provides important information about the incident. This includes the case details, entity information (user and endpoint details), the incident timeline, the assigned analyst, the alerts in the incidents, whether any task needs human input, the close reason for the incident, and buttons to help with some quick actions related to the incident.
The Investigation Results tab holds all the information about the investigation and the indicators associated with the incident. This includes the investigation verdict, investigation results that summarize all the results that led to the verdict, any XDR-related alerts tied to MITRE tactics performed on the endpoint or by the user, and the indicators associated with the incident.
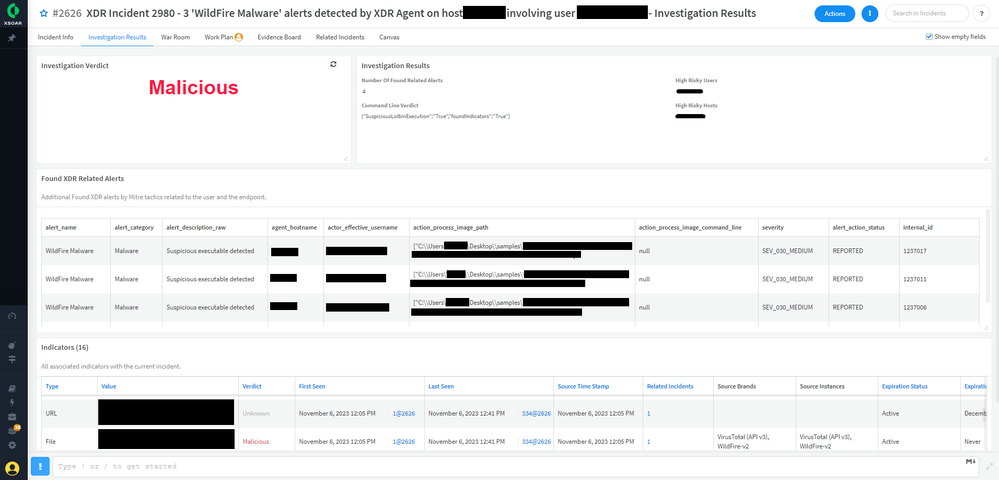 Layout - Investigation Results tab
Layout - Investigation Results tab
Handling and responding to Cortex XDR incidents with XSOAR has never been easier, thanks to the "Cortex XDR Lite - Incident Handling" playbook. No additional integrations are required outside of the Cortex XDR incident response pack, to use this playbook.
These updates are now available in XSOAR as part of the Cortex XDR content pack available via our Cortex Marketplace.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
| Subject | Likes |
|---|---|
| 3 Likes | |
| 2 Likes | |
| 1 Like | |
| 1 Like | |
| 1 Like |




