- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Please share your useful XQL queries!
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Please share your useful XQL queries!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Please share your useful XQL queries!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2022 03:57 PM
Hello!
as a beginner with Cortex XDR I asked me, what are interests of others in the query section.
If you have some interesting and useful queries, please share and describe them in a short way.
Thank you!
BR
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-27-2022 03:15 PM - edited 03-27-2022 03:18 PM
Hi Rob,
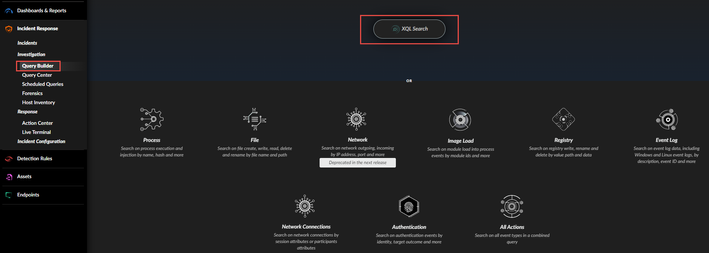
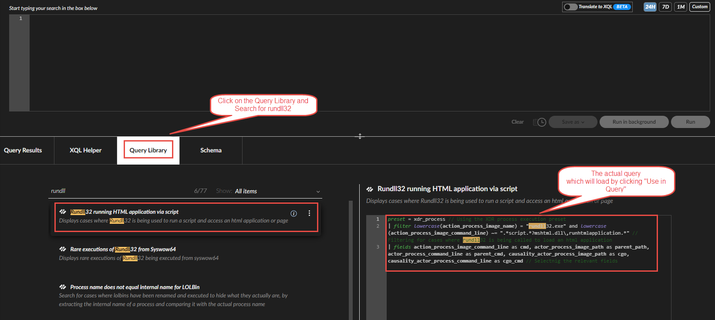
If you need an example of useful XQL queries, you could click on Query Builder and then click on XQL Search which will open an IDE for XQL, in the bottom you will have 4 tabs out of which select Query Library and take a look at the XQL query example. Lets say in your in-built XQL library there is query for "Rundll32 running HTML application via script"
Query from XQL Library:
preset = xdr_process // Using the XDR process execution preset
| filter lowercase(action_process_image_name) = "rundll32.exe" and lowercase(action_process_image_command_line) ~= ".*script.*?mshtml.dll\,runhtmlapplication.*" // Filtering for cases where rundll32 is being called to load an html application
| fields action_process_image_command_line as cmd, actor_process_image_path as parent_path, actor_process_command_line as parent_cmd, causality_actor_process_image_path as cgo, causality_actor_process_command_line as cgo_cmd // Selectnig the relevant fields
Description (According to me):
This query is useful in monitoring of html/hta file execution via rundll32.exe. Generally mshta.exe is used for execution of malicious html/hta files but rundll32.exe can also be used hence the query hunt.
Searches for any process name which executed with an image name of rundll32.exe where the command line of the process matches a regex patterns which could match a command line such as below:
Importance:
HTML code could be used to run scripts such as javascript/vbscript which can be used maliciously in an environment.
KS
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-13-2022 05:22 AM
This Query search for CVEs CVE-2022-0025 and CVE-2022-0026
dataset = endpoints
| fields endpoint_name , endpoint_type , ip_address , endpoint_status, last_seen, agent_version , content_version , last_content_update_time
|alter content_version = to_integer(replex(content_version, "-", "" ))
| filter content_version < 33000000 or (agent_version ~= "7.7.0" and content_version < 50000000)
Regards
Ernander
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-13-2022 05:43 AM
Hi Rob,
Below is the query for scan errors for all endpoints
dataset= endpoints
|fields endpoint_name as hostname , endpoint_status , last_seen , install_date as Installationdate, agent_version, scan_status , agent_license_type , installation_type , ip_address, last_successful_scan as LastScan
|filter endpoint_status = ENUM.CONNECTED or endpoint_status = ENUM.DISCONNECTED
|filter scan_status = ABORTED or scan_status = CANCELED or scan_status = SCAN_ERROR
|sort desc last_seen
Thanks
Naga
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-23-2023 10:13 AM
Thank you so much!
BR
Rob
- 12360 Views
- 4 replies
- 2 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Inquiry regarding Tenant Backu & Recovery in Cortex XDR Discussions
- Cortex XDR Device Control Violation Alerts in Cortex XDR Discussions
- Request for Query to Retrieve Endpoint Security Details. in Cortex XDR Discussions
- XQL query to get a list of current applications installed on hosts in Cortex XDR Discussions
- XQL Query in Cortex XDR Discussions