- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
XQL Search- to get the source of the file
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- XQL Search- to get the source of the file
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
XQL Search- to get the source of the file
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2023 12:28 AM
I want to know the XQL query or filters which helps in the analysis of alerts & to know the source of file where it is coming into our system.
For example- whether user downloaded the file from browser or someone sent through outlook, from portable device, etc.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2023 04:11 PM
Hello Seth_Sakshi
1- For the incident and alert data, they are not currently exposed to any XDR dataset , hence you cannot directly query incident and alerts but this is subject to change in the future.
However, leads and data that is collected by the XDR agent they are exposed to XQL by using the dataset = xdr_data.
To query file actions for example, you can use in your search either of the below as your data source :
dataset = xdr_data
OR
preset = xdr_file
Then you can consult eh schema buy navigating to the "Schema" tab to see what fields are there that you can use to build your filter based on your use case such as
action_file_name
action_file_path
action_file_previous_file_path
And more.
Please note, downloading a file doesnt trigger an event that is exposed to XQL since it is not a type of event that is natively collected by the XDR agent unlike executions events like file actions and process executions, such as File write and File create, ...
Example below for a query that looks for Binary file dropped to Public user folder:
preset = xdr_file // Using the XDR file preset
| filter lowercase(action_file_path) ~= "c:\\users\\public\\.*?.(exe|dll|sys|scr|msi)" and event_sub_type = ENUM.FILE_WRITE and action_file_sha256 != null //Filtering for binary files created under c:\users\public with a sha256 value
| fields action_file_path as file_path, action_file_sha256 as file_sha256, actor_process_image_path as process_path, actor_process_command_line as process_cmd, causality_actor_process_image_path as cgo_path, causality_actor_process_command_line as cgo_cmd // Selecting the relevant fields
| dedup file_path, file_sha256, process_path, process_cmd, cgo_path, cgo_cmd by asc _time // Dedupping values to only show the first time a file was written
Hope that was helpful and shed some light!
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2023 10:08 PM
Hello Zarnous,
Thanks for your input.
I have some more queries regarding this-
- Can we get the logs of a file which is not executed but only detected during the weekly malware scan? I want to know by when and where this file comes into the system.
Thanks in advance.
Regards,
Sakshi Seth
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-07-2023 07:38 AM
as long as this information was captured by the agent then yes for sure, you can start with something as simple as looking for a file name or a part of the file name/ extension:
For example, i am looking for file that have ".json"
preset = xdr_file
| filter (action_file_name contains """.json""")
Then you can define the Event sub type you are looking for, such as
FILE_CREATE_NEW
FILE_REMOVE
FILE_RENAME
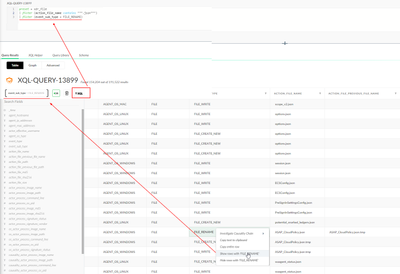
Or you can just leave it with no specific sub event type to see all actions taken on that specific file , like in the below screenshot that looks for all files with ".json" with no specific sub event type specified
Then lets say you want to filter on more actions / field, you can do that by simply filter on the field you would like to look for then you can easily export the grid filter up toe the XQ-Filed as seen below
This way you can build your filters to apply to the use case you are looking for
Hope that helps!
- 5523 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- File search query for Android in Cortex XDR Discussions
- Search Files by Query on Android (Cortex XDR) in Cortex XDR Discussions
- Splunk integration - Mirroring not working in Cortex XSOAR Discussions
- Toutrial: Detecting Tor Traffic in XSIAM in Cortex XDR Discussions
- Understanding ENUM Constants in Cortex XSIAM XDR Data XQL in Cortex XDR Discussions