- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Implement Google Cloud Organization Restrictions
- LIVEcommunity
- Articles
- General Articles
- Implement Google Cloud Organization Restrictions
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-03-2023 05:03 PM - edited 05-03-2023 05:07 PM

Introduction
Security administrators can use Google Cloud IAM to control who can access resources within a Google Cloud organization. However, companies may require the ability to restrict access to resources and APIs that reside in different Google Cloud organizations.
The combination of Palo Alto Networks URL filtering and Google Cloud organization restrictions, enables security teams to restrict employee access to sanctioned Google Cloud organizations. The capability provides a variety of security benefits including, preventing insider attacks and also stopping data exfiltration.
Use-Cases
There are many use-cases for organization restrictions, for example:
- In combination with Palo Alto Networks URL Filtering, you can monitor and control sites users can access, prevent phishing attacks by controlling the sites to which users can submit valid corporate credentials, and enforce safe search for search engines like Google.
- You can restrict access so employees can only access resources in your Google Cloud organization and not other organizations.
- You can allow your employees read-only access to any Cloud Storage resources, but restrict all other types of access to only resources in your Google Cloud Organization.
- You can allow your employees to access a vendor Google Cloud organization in addition to your Google Cloud organization.
How it works
The diagram below shows the required components to enforce organization restrictions. When a managed device accesses a Google Cloud resource, the URL Filtering profile defined within the security policy, inserts the value for the organization restrictions header, X-Goog-Allowed-Resources.
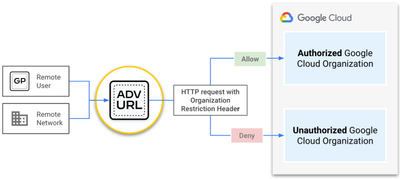
- Managed device: Any device that adheres to the organizational policies of the company and is connected to, or routed through, a Palo Alto Networks enforcement point with URL Filtering enabled. For example, the managed device can be a remote user connected with GlobalProtect, a datacenter server protected by a PA-Series NGFW, or cloud resources protected by VM-Series NGFW.
- Palo Alto Networks URL Filtering: A URL Filtering profile is created and attached to the security policy. The profile inserts the organization restriction as a custom header for any requests originating from the managed device. This configuration prevents users and devices from accessing any Google Cloud resources that reside in unsanctioned Google Cloud organizations.
- Google Cloud: The organization restrictions feature in Google Cloud inspects all requests for organization restrictions header, and allows or denies the requests based on the organization being accessed.
Example Scenario
The network security administrator of Organization A, wants to allow employee access to resources hosted in their Google Cloud organization. All employee access to cloud resources hosted in all other Google Cloud organizations should be denied.
Configuration
A cloud and network security administrator for Organization A perform the following steps to implement organization restrictions.
- Retrieve the Google Cloud organization ID for
Organization A.
(output)gcloud organizations listDISPLAY_NAME: Organization A ID: 0123456 DIRECTORY_CUSTOMER_ID: a1b2c3d4
- Create a JSON representation for the value that will be assigned to the organization restriction header,
X-Goog-Allowed-Resources, and save it to a file namedauthorized_orgs.json. Please see configure organization restrictions for complete information on constructing the value for the header.{ "resources": ["organizations/0123456"], "options": "strict" }
- Encode the header value in base64 format. Below is an example using basenc. The URL Filtering profile will insert the base64 string as the value for the X-Goog-Allowed-Resources header.
(output)cat authorized_orgs.json | basenc --base64url -w0fdsasdfInJlc291cmNlasjdfaJnYW5pemF0ay8xMjM0NTY3ODkiXSwKICJvcHRpb25zIjogInN0cmljdCIKfQo
- If there are no upstream devices decrypting HTTPS traffic, configure SSL Forward Proxy.
- On the Palo Alto Networks device, edit or create a URL Filtering profile. In the profile, click HTTP Header Insertion → Add to create a new entry. Configure the entry as follows:
- Header:
X-Goog-Allowed-Resources - Value: Add the base64 encoded value from the previous step.
- Header:
- Apply the URL Filtering profile to your security policy that inspects the managed device’s internet traffic.
- Commit the changes.
Verify Configuration
The organization restrictions are applied for access to the Google Cloud APIs and Google Cloud console. On a managed device that has access to both Organization A and Organization B, perform the following to test the organization restrictions feature.
- On the managed device, log into the Google Cloud Console with an account that has access to
Organization AandOrganization B.
- In the Console, click the Organization drop down menu.
Even though the user account on the managed device has access toOrganization AandOrganization B, onlyOrganization Aappears in the Google Cloud Console. This is because the URL Filtering profile inserts the organization restriction header to enable Google Cloud to block the user from accessing other organizations.
- From the same managed device, attempt to reach the logging API of a Google Project (i.e.
org-a-project) that belongs toOrganization A.The request should show a successful return of the log entries within the Google Cloud project belonging to
Organization A.
(output)TOKEN=$(gcloud auth print-access-token) curl -X POST -d '{"projectIds": ["org-a-project"]}' -H 'Content-Type: application/json' -H "Authorization: Bearer ${TOKEN}" "https://logging.googleapis.com/v2/entries:list"{ [ <..redacted..> ] nextPageToken": "EAB<..redacted..>RsAB" }
- Attempt to reach the logging API of a Google Cloud project (i.e. org-b-project) that does not belong to
Organization A.The request should show a failed return to the Google Cloud project that does not belong to
Organization A. This is because the URL filtering profile inserted the organization restriction header into the request of the managed device.
(output)curl -X POST -d '{"projectIds": ["org-b-project"]}' -H 'Content-Type: application/json' -H "Authorization: Bearer ${TOKEN}" "https://logging.googleapis.com/v2/entries:list"{ "error": { "code": 403, "message": "Access denied by organization restriction. Please contact your administrator for additional information.", "status": "PERMISSION_DENIED", "details": [{ "@type": "type.googleapis.com/google.rpc.ErrorInfo", "reason": "ORG_RESTRICTION_VIOLATION", "domain": "googleapis.com", "metadata": { "consumer": "projects/01234567890", "service": "logging.googleapis.com" } }] } }
Additional Materials
- 12709 Views
- 0 comments
- 0 Likes
-
"Address Objects"
1 -
10.0
1 -
10.1
1 -
10.2
2 -
ACC
1 -
Active-Passive
1 -
AD
1 -
address objects
1 -
admin roles
1 -
Administration
6 -
Administrator Profile
1 -
ADNS
1 -
Advanced DNS Security
1 -
Advanced URL Filtering
2 -
Advanced WildFire
1 -
AI
2 -
AI Security
1 -
AI Threat
1 -
AIOPS
1 -
Ansible
1 -
antivirus
1 -
API
1 -
App-ID
1 -
applications
2 -
APS
1 -
Artificial Intelligence
1 -
Asset Management
1 -
Authentication
6 -
Authentication Profile
1 -
Authentication Sequence
1 -
automatically acquire commit lock
1 -
Automation
3 -
aws
3 -
Basic Configuration
4 -
Beacon
1 -
Best Practices
6 -
Block List
1 -
categories
1 -
certificates
1 -
Certification
1 -
Certifications
1 -
Certifications & Exams
1 -
CLI
5 -
CLI command
3 -
Cloud Automation
1 -
Cloud Identity Engine
1 -
cloud ngfw
1 -
cloud security
1 -
Collector Group
1 -
Commit and Push
1 -
Commit Process
1 -
Configuration
8 -
Configuration and Management
3 -
Configure Next Generation Firewall
1 -
console
1 -
Cortex
1 -
Cortex Data Lake
2 -
Cortex XDR
3 -
CPSP
1 -
Custom Signatures
3 -
cyber elite
1 -
cyberelite
11 -
Cybersecurity
1 -
dag
1 -
DDoS
1 -
Debug
1 -
debugging
2 -
Default Policy
1 -
discussions
1 -
DLP
1 -
EDL
2 -
education
1 -
Education and Training
1 -
Education Services
1 -
Educational Services
1 -
Effective Routing
1 -
End to End Encryption
1 -
Endpoint
1 -
export
1 -
failover
1 -
FAQ
1 -
file upload
1 -
Filtering
2 -
Firewall
2 -
Firewall VM-Series
2 -
Focused Services
3 -
Focused Services Proactive Insights
2 -
gateway
1 -
Gateway Load Balancer
2 -
GCP
2 -
GCP Firewall
1 -
geolocation
1 -
Getting Started
1 -
GitHub
1 -
Global Protect
1 -
Global Protect Cookies
1 -
GlobalProtect
7 -
GlobalProtect App
1 -
globalprotect gateway
1 -
GlobalProtect Portal
2 -
google
2 -
Google Cloud
3 -
google cloud platform
2 -
Hardware
2 -
Header Insertion
1 -
High Availability
1 -
How to
1 -
HTTP
1 -
https
1 -
Hybrid Cloud
1 -
ike
3 -
import
1 -
Installation & Upgrade
1 -
IoT
1 -
IPSec
4 -
IPSec VPN Administration
1 -
kerberos
1 -
Layer 2
1 -
Layer 3
1 -
Learning
1 -
licenses
1 -
local user
3 -
Log Cluster Design
1 -
Log Collection
3 -
Log Collector Design
2 -
Logging
1 -
login
1 -
Logs
3 -
Management
8 -
Management & Administration
5 -
MFA
1 -
Microsoft
1 -
Microsoft 365
1 -
Migration
1 -
minemeld
4 -
multi factor authentication
1 -
multi-factor authentication
1 -
multi-vsys
1 -
NAT
1 -
NetSec
1 -
NetSec Newsletter
1 -
network security
34 -
Network Security Management
1 -
Network-Security
1 -
Networking
1 -
newsletter
2 -
Next Generation Firewall
4 -
Next-Generation Firewall
42 -
next-generation firewall. network security
1 -
Next-Generation Firewall. NGFW
6 -
NGFW
30 -
NGFW Configuration
11 -
NGFW Newsletter
1 -
Nominated Discussion
1 -
Objects
2 -
OTP
1 -
PA-3200 Series
1 -
PA-400
1 -
pa-440
2 -
PA-5400 series
1 -
PA-800 Series
1 -
pa-820 firewall
1 -
Packet Buffer
1 -
packet debug
1 -
packet diag
1 -
PAN-OS
16 -
PAN-OS 10.2
1 -
PAN-OS 11.0
1 -
PAN-OS Prisma Access
1 -
Panorama
11 -
Panorama Configuration
2 -
PBF
1 -
PCNSA
1 -
PCNSE
1 -
performance
2 -
policies
2 -
policy
3 -
Policy Based Forwarding
1 -
Prisma Access
7 -
Prisma AIRS
1 -
Prisma SASE
2 -
Prisma SD-WAN
1 -
proactive insights
2 -
Prompt Poaching
1 -
Radius
1 -
Ransomware
1 -
RBI
2 -
region
1 -
Registration
1 -
Remote Browser Isolation
3 -
reporting and logging
1 -
RestAPI
1 -
Risk Management
1 -
Routing
1 -
SAML
1 -
SASE
1 -
script
2 -
SD WAN
1 -
SDWAN
1 -
Search
1 -
Security Advisory
1 -
Security automation
1 -
security policy
4 -
security profile
1 -
Security Profiles
2 -
Selective Push
1 -
Session Packet
1 -
Setup & Administration
8 -
Site-to-Site VPN
1 -
Split Tunneling
2 -
SSL
1 -
SSL Decryption
2 -
SSL Forward Proxy
1 -
SSO
1 -
Strata Cloud Manager
1 -
Strata Logging Service
2 -
Support Guidance
1 -
syslog
1 -
system modes
1 -
Tag
2 -
tags
2 -
Terraform
2 -
Threat
1 -
threat log
1 -
Threat Prevention
1 -
Threat Prevention License
1 -
Tips & Tricks
1 -
TLS
1 -
traffic_log
1 -
Traps
1 -
Troubleshoot
2 -
Troubleshoot. logs
1 -
Troubleshooting
6 -
tunnel
2 -
Tutorial
2 -
Unified Monitoring
1 -
upgrade
1 -
upgrade-downgrade
2 -
url categories
1 -
URL Filtering
2 -
URL-Filtering
1 -
User ID Probing
1 -
User-ID
1 -
User-ID & Authentication
1 -
User-ID mapping
1 -
userid
1 -
VM Series
1 -
VM-Series
7 -
VM-Series on AWS
3 -
VM-Series on GCP
2 -
VPC Flow logs
1 -
VPN
3 -
VPNs
4 -
Vulnerability
2 -
Vulnerability Protection
1 -
WhatsApp
1 -
WildFire
2 -
Wildfire License
1 -
wmi
1 -
XDR
1 -
xml
2 -
XML API
2
- Previous
- Next






