- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Blocking youtube
- LIVEcommunity
- Discussions
- General Topics
- Blocking youtube
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Blocking youtube
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-18-2013 08:13 PM
How can I properly block youtube, because it's bypassing a PA-3050 on port 443 (https://)?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-20-2013 11:37 AM
You can either implement SSL decryption, or use URL filtering. (If you use URL filtering, and don't implement SSL decryption, your user will be greeted with a blank page since the firewall can't inject the comfort page.)
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-11-2014 04:34 PM
I believe you could do in two different ways:
1. Build a security policy with app youtube-base and action block;
2. Use an URL filtering profile to block streaming-media category (would block more but you could use allow list to make exceptions... or add youtube with wildcards on the block list of a url filtering that allow streaming media categories;
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-06-2015 06:52 AM
Unfortunately neither of those solutions works (without SSL decryption). I have youtube application blocked, all streaming media blocked with URL filtering, youtube.com in URL block list and youtube still works. It is recognised as SSL application and goes to an URL which is categorised as 'search-engines'. I'll try to catch this URL and add it to block list.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-06-2015 09:42 AM - edited 10-14-2015 12:17 PM
You can block youtube with or without SSL Decryption.
With SSL Decryption, and if you don't want to implement it for *everything* you can do a targeted decryption to *.google.com and then block youtube.com and *.youtube.com with a Custom URL Category, or simply add those lines to the URL Filtering Profile Block List. I explain how to do a targeted decryption on document: How to Block a Specific HTTPS Site with URL Filtering
Without SSL decryption we can't see the HTTP GET, so URL Filtering wouldn't ever trigger. However, without SSL decryption we can still see the SNI (sent from the Browser) and the CN (inside Subject Name field, in the certificate presented by the server). The CN for youtube is *.google.com, however blocking this will also block all HTTPS sites with certificates that present *.google.com
Note that in order to present a block page without SSL decryption, you may want to refer to How to Serve a URL Response Page Over an HTTPS Session Without SSL Decryption
The SNI is sent from the browser on the SSL 'Client Hello' message, and it is, in this example: www.youtube.com
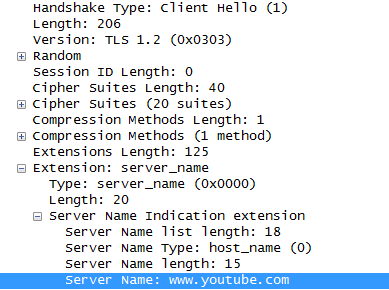
This means that adding an URL Filtering Block rule for *.youtube.com, will block access to YouTube by leveraging the SNI.
This (reading SNI) is a feature which was included on PAN-OS 6.0
Please note that not all browsers do support SNI (not all of them send the SNI value).
Note that the SNI is an extension of TLS (a.k.a SSLv3.1 and above), so SSLv3.0 won't send the SNI, even if you are using the correct browser. Please disable SSLv3.0 in your browser to make sure it's not contributing to the problem. Digicert has an excellent tutorial on how to achieve this. See: Disabling Browser Support - SSL v3 Protocol | DigiCert.com
To know when SNI was implemented into a Browser/Operative System combination, there's a good article on it on Wikipedia. See: Server Name Indication - Wikipedia, the free encyclopedia
Implementation[edit]
In 2004, a patch for adding TLS/SNI into OpenSSL was created by the EdelKey project.[5] In 2006, this patch was then ported to the development branch of OpenSSL, and in 2007 it was back-ported to OpenSSL 0.9.8.
For an application program to implement SNI, the TLS library it uses must implement it and the application must pass the hostname to the TLS library. Further complicating matters, the TLS library may either be included in the application program or be a component of the underlying operating system. Because of this, some browsers implement SNI when running on any operating system, while others implement it only when running on certain operating systems.
Web browsers[6][edit]
- Internet Explorer 7 or later, on Windows Vista or higher. Not in any Internet Explorer version on Windows XP or Windows Server 2003 because SNI depends upon the SChannel system component shipped with Windows Vista.[7]
- Mozilla Firefox 2.0 or later
- Opera 8.0 (2005) or later (the TLS 1.1 protocol must be enabled)[8]
- Opera Mobile at least version 10.1 beta on Android[citation needed]
- Google Chrome (Vista or higher. XP on Chrome 6 or newer.[9] OS X 10.5.7 or higher on Chrome 5.0.342.1 or newer)
- Safari 3.0 or later (Mac OS X 10.5.6 or higher and Windows Vista or higher)
- Konqueror/KDE 4.7 or later [10]
- MobileSafari in Apple iOS 4.0 or later[11]
- Android default browser on Honeycomb (v3.x) or newer[12]
- BlackBerry 10 and BlackBerry Tablet OS default browser
- Windows Phone 7 or later[13]
- MicroB on Maemo
- Odyssey on MorphOS
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-06-2015 10:02 AM
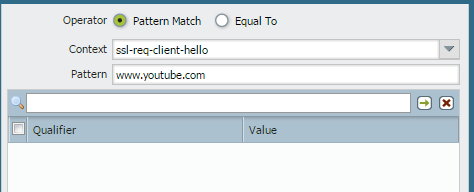
just write a custom app-id and use client hello for ssl and pattern as youtube.com
write a deny rule for that application
youtube will not work with https
you don't need to use ssl decryption.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-07-2015 03:17 PM
Without SSL decryption, the firewall thinks that Youtube is also Google.
Browse to https://www.youtube.com and look at the certificate information. The CN is *.google.com.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2015 07:02 AM
by creating a custom app-id it takes precedence over builtin apps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 03:06 PM
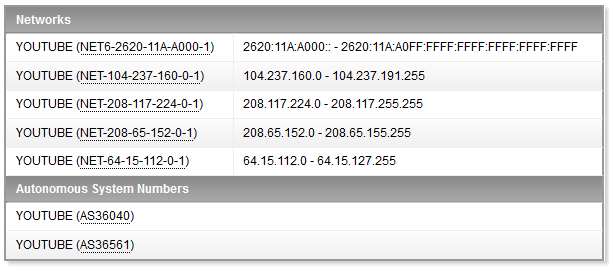
Unlikely to remain static, they have one of the largest CDN's in the world. Guaranteed those will not remain the same.
Also if you obtain the list of all Google IP's, you won't have a way to tell which are serving YouTube.
Please see:
Google IP address ranges - Google Apps Help
For a list of all google IP's, you could alternatively leverage information to create an EBL from radb.net and shadowserver.org. The idea is to create a cron script that hosts a clear text file from a web server like apache, (may need to tweak the output to adjust to EBL accepted format). Then will be periodically updated and fetched as follows:
mivaldi$ ping www.youtube.com
PING www.google.com (64.15.118.10😞 56 data bytes
64 bytes from 64.15.118.10: icmp_seq=0 ttl=54 time=2.506 ms
^C
--- www.youtube.com ping statistics ---
1 packets transmitted, 1 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 2.506/2.506/2.506/0.000 ms
mivaldi$ whois -h asn.shadowserver.org "origin 64.15.118.10"
43515 | 64.15.112.0/20 | YOUTUBE | IE | google.com | YouTube LLC
Or search AS by name here:
http://bgp.potaroo.net/as1221/asnames.txt
...or here:
https://www.ultratools.com/tools/asnInfoResult?domainName=youtube
mivaldi$ whois -h whois.radb.net -- '-i origin AS43515' | grep ^route
route: 208.65.154.0/24
route: 208.65.155.0/24
route: 208.117.226.0/24
route: 208.117.234.0/24
route: 208.117.235.0/24
.
.
.
All known YouTube AS43515 IP's
... Also note that some AS like Google's may contain very long lists...
mivaldi$ whois -h whois.radb.net -- '-i origin AS15169' | grep ^route | wc -l
6876
If it's a long list and may exceed your EBL limits (dependent on platform).
Note: Commands were run from Mac terminal. Will also work on Linux, or cygwin terminal on Windows.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 03:12 PM
Well put! I just tried to see what it would look like so here is a snipped of what the PAN see's for that https traffic:
HTTPS
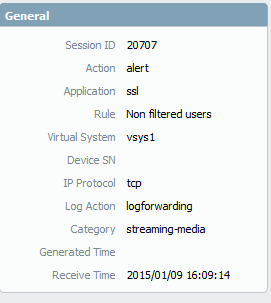
It is seeing at SSL but also the URL filter categorizes it properly so you maybe able to use the URL filter to block streaming-media.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 03:16 PM
This will not work with explorer 11
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 03:41 PM
I still think that blocking that category will resolve this issue. I just tried it with IE11:
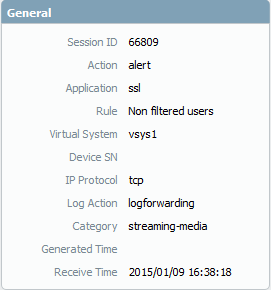
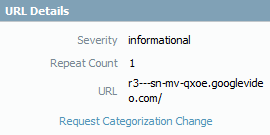
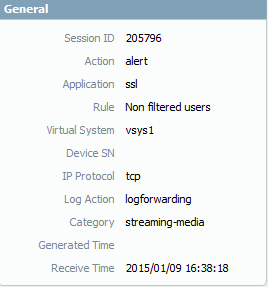

Or maybe we just need to wait for PAN to update their definitions for this?
- 17976 Views
- 16 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Geo blocking after GP login in GlobalProtect Discussions
- Unable to block download and upload for chatgpt and messengers in Next-Generation Firewall Discussions
- Stealth Rule Question in Next-Generation Firewall Discussions
- Detect and Block Openclaw with XDR!? in Cortex XDR Discussions
- Notepad++ block specific hash version in Cortex XDR Discussions