- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Commit Error After Upgrading to 10.0.9
- LIVEcommunity
- Discussions
- General Topics
- Re: Commit Error After Upgrading to 10.0.9
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Commit Error After Upgrading to 10.0.9
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-07-2022 07:27 AM
Hi Team,
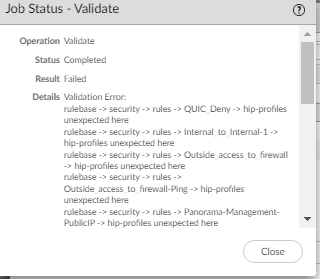
Getting below commit validation error after upgrading to PAN-OS 10.0.9.
- Validation Error:
- rulebase -> security -> rules -> QUIC_Deny -> hip-profiles unexpected here.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2022 08:40 AM - edited 04-04-2022 08:41 AM
I too had the error 'hip-profiles unexpected here' when going from 10.0.8-h8 to 10.0.9 on Panorama. Attempting to run the command 'delete device-group DG_AllFirewalls pre-rulebase security rules "TEST App" hip-profiles', I received 'Invalid syntax.' Even though the steps I list below are for Panorama, you should be able to change them to match your firewall.
Steps I did:
1) Downgrade Panorama from 10.0.9 to 10.0.8-h8
2) Backup your config in case you mess anything up.
3) find all rules that contain hip-profiles with the following commands:
set cli config-output-format set
configure
show device-group DG_AllFirewalls pre-rulebase security | match hip-profiles
4) copy and paste all results in notepad++. then change these commands to be delete commands
5) find and replace "set " with "delete "
6) find and replace "hip-profiles any" with "hip-profiles"
7) copy and paste the updated commands back into putty in sets of 30 (originally I tried sets of 40 but it exceeded the buffer size)
8 ) look for any rules that might have failed or had been missed:
show device-group DG_AllFirewalls pre-rulebase security | match hip-profiles
9) I had one hip-profiles rule that did not delete. The reason neither the delete command, nor the show command matched a rule was because it had 2 consecutive spaces in the name. I'm not sure if it is a bug or a subtle hint to clean up the rule name. I took the hint, cleaned up the rule name from the GUI, and then was able to come back to CLI to delete the hip-profiles entry.
10) commit the changes
commit
11) Optional, exit and set the cli display back to default
exit
set cli config-output-format default
12) take another backup
13) upgrade Panorama from 10.0.8-h8 to 10.0.9
14) test modifying the security rules you were not able to before.
For me, I did the above because I didn't need to plan for any user downtime since the downgrade/upgrade were on Panorama rather than the actual firewalls, and it was only one command to run to remove it. I'm assuming your firewall is in production and it might be annoying to schedule two reboots so I had another idea that I didn't test/use. You should be able to backup/export your config on 10.0.9, remove the hip-profiles lines in the xml file, and then import/load the modified xml file.
I hope that helps.
-Bill
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-05-2022 10:55 AM
I am facing a similar issue, however for the Authentication rule. I tried it via CLI. I do see a hip-profile match, however, there is no matching option for the delete command.
delete rules <rule-name>
authentication-enforcement Authentication enforcement object to use for authentication.
category category
description description
destination destination
destination-hip destination-hip
disabled Disable the rule
from from
group-tag group-tag
log-authentication-timeout log-authentication-timeout
log-setting Log setting for forwarding authentication logs
negate-destination negate-destination
negate-source negate-source
service service
source source
source-hip source-hip
source-user source-user
tag tag
target Target devices
timeout expiration timer (minutes)
to to
<Enter> Finish inputHere is config for the policy.
set device-group <GROUP-NAME> post-rulebase authentication rules <RULE NAME> hip-profiles any
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-05-2022 10:59 AM - edited 04-05-2022 11:00 AM
I tried the CLI option. I could see the hip-profile config for the rule, however, delete command does not have hip-profile option for removal. I replace set with delete and use the same config, then it complains about invalid syntax. Looks like a bug.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2022 03:19 AM - edited 04-06-2022 03:39 AM
I had this issue in authentication policy where there are luckily not many rules.
List the problematic authentication rule in CLI in set format and you will see a line which sets hip-profile to any.
Unfortunately you can't just use delete command for hip setting as Pan-OS doesn't expect hip-profile here.
So copy the whole existing rule to your favorite text editor, change the rule name to something else, and paste it back without the hip profile line.
After checking the new identical rule is in place, delete the original rule and commit
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2022 06:51 AM
One of my colleagues worked on editing the xml config and re-importing the config in Panorama. It resolved the issue. It was a hassle. Palo Alto needs to resolve this issue in the PAN-OS.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-08-2022 01:22 AM
We are facing the issue now to, after upgrading from 10.1.3 to 10.1.5h1.
Downgrade to 10.1.4h4 as suggested would not fix the OpenSSL vulnerability:
https://security.paloaltonetworks.com/CVE-2022-0778
From the looks of it, this bug was fixed in 10.5.0:
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-release-notes/pan-os-10-1-5-known-and-addressed...
PAN-171869 | Fixed an issue where HIP profile objects in Security policies and authentication policies were replaced with source HIP and destination HIP objects. |
After hitting already lovely bugs with 10.1.3 and 10.1.4 with device tag assigned security rules and dynamic object groups. 10.1.x looks like a bullet proof release of PAN-OS.
Regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2022 02:05 AM
We also experienced the same issue on 10.1.5-h1, so have reverted to 10.1.4-h4... but as mentioned that leaves us with the OpenSSL vulnerability. Any news on a fix?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2022 02:29 AM
Guys, I encountered another problem during committing from Panorama. When I try to push configuration to devices validation fails and all what I can see about is like below. After click on the status a window without content is displayed. None, indeed 😉
So, because both Panorama and my device have exactly same version (10.0.9) I pushed configuration locally (on the device) and it finished successfully. Most likely it is another Panorama bug 😞
I will create support ticket today and provide feedback here if a solution will be found.
All the best 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2022 06:39 AM
I had the same issue. The policy wrong was under Policy - Authentication. I've deleted and recreated my policy and then the commit was fine. Hope it helps
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2022 06:47 AM - edited 04-13-2022 06:47 AM
@rpanini I had exactly same issue with authentication policies 😉
Ok, so I will try to do the trick again however it will be a bit harder - I have a lot of configuration in these configs.....
Anyway i created a support ticket an I hope somebody picks it up.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2022 09:14 AM
Hi guys,
The solution that worked for me was:
1)in CLI identify the affected rules with the command: show rulebase security | match hip-profile
2)for each affected rule: show rulebase security rules "Rule affected by problem"
copy rule commands to text editor
remove line ---set rulebase security rules "Rule affected by problem" hip-profiles any
delete the rule in GUI (first note it's rule number, because when you create a new one it is going to be at the end all policies)
paste commands to create the new rule without the problematic line
repeat this with all the rules wih the problem
I hope it helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-16-2022 01:05 PM
Thanks! This fixed it for me.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-17-2022 01:05 AM
release. I have problem with validation template stack during push to
devices. (error message: none).
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-18-2022 01:27 PM
FWIW, the rules causing the issue for me were generated using the BPA+ tool.
- 33658 Views
- 44 replies
- 2 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- XSIAM V3.4 upgrade - anyone having issues? in Cortex XSIAM Discussions
- PAN-OS HA UGRADE PATH in Next-Generation Firewall Discussions
- Playbook stuck after upgrade in Cortex XSOAR Discussions
- From Template Stack Override in Advanced SD-WAN for NGFW Discussions
- HA ACTIVE firewall is failing when commit in General Topics