- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Direct web traffic to internal proxy
- LIVEcommunity
- Discussions
- General Topics
- Direct web traffic to internal proxy
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Direct web traffic to internal proxy
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-03-2019 02:23 AM - edited 09-03-2019 02:36 AM
For some reason oun of our MS GPO's is failign to apply ( or rather is wiping ) proxy server settings for our users.
The users shoudl be hitting the proxy before going through the PA, but it's broken.
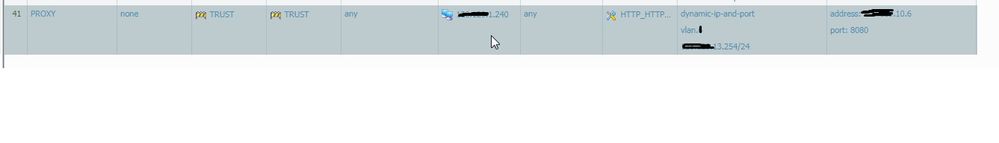
USER-Website:80:443 --> PROXY:8080 --80:443--> --PALO --> WORLD
I am trying to fatom how to get teh PA to transparently pass traffic to the proxy but it's not working..
USER-Website:80:443 --> PALO --> PROXY:8080 --> WORLD
I have tied a nat rule ( one source at present )
X.X.13.254 is the firewall trusted interface.
X.X.10.6 is the proxy server.
But I get a "Mismatch of destination address translation range between original address and translated address"
It's not, as far as I can tell the issue with named objects.
Ideas?
Rob
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-03-2019 12:00 PM
Hello
If it was me... I would NOT be using any sort of NAT rules at all (are they really needed?)
I would configure a VWire Object (My-VW-Object) and associate 2 interfaces (need 2) with it.
Vwire acts as essentially a 2 port repeater, with no layer2 or layer3 address (no mac or IP)
So I would associate (say) interface 4 and 5 with My-VW-Object)
Now the traffic looks like this.
USER-Website:80:443 --> (INT 4 in VWmode) PALO (INT 5 in VWmode --> PROXY:8080 --> WORLD
or even easier
USER-Website:80:443 --> PROXY:8080 --> WORLD
(because VWire mode = repeater... the User's next hop would be the Proxy server)
Considerations...
Interface 4 as vwire needs to belong to a zone... So VW-Internal Zone
Interface 5 as vwire needs to belong to a one... So VW-External Zone.
Need a security policy that allows VW-Internal Zone to talk with VW-External Zone
No NAT rule is needed (again, Vwire does not have L3 address associated with it)
No complimentary rule is needed (VW-External talking with VW Internal)... because... well, your proxy should not be allowing inbound connections to your trusted network. 😛
Any other questions?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-09-2019 07:34 AM
without NAT the vwire will pass "443 -> 443" and "80 -> 80" it will never get translated to the proxy port 8080.
Also there would be no way to get the traffic to the vwire. the default route out of the network points at the main firewall l3 interface so ALL traffic includig 80:443 arrives there.
And the Proxy is on an internal IP as part of one of our subnets.
It's a documented setup using IPTABLES on Linux, just thought it may be replicatable.
Fortunatly we tracked down our issue to the I.E. Exception list having breached to 2056 character limit.. We thought we had ruled that out early in the investiagtion but we can't have.
- 3519 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- High Bandwidth on Broker VM: Cluster Mismatch (v29 vs v28) & P2P in Cortex XDR Discussions
- Discord voice chat no longer connecting after PA-440 install in General Topics
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in General Topics
- Multiple High/Critical Alert Detected via Port 18264 | Possible FP in VirusTotal
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud