- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
dmz data flow
- LIVEcommunity
- Discussions
- General Topics
- dmz data flow
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
dmz data flow
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-18-2021 10:48 AM
Hi,
Please advise
Hi,
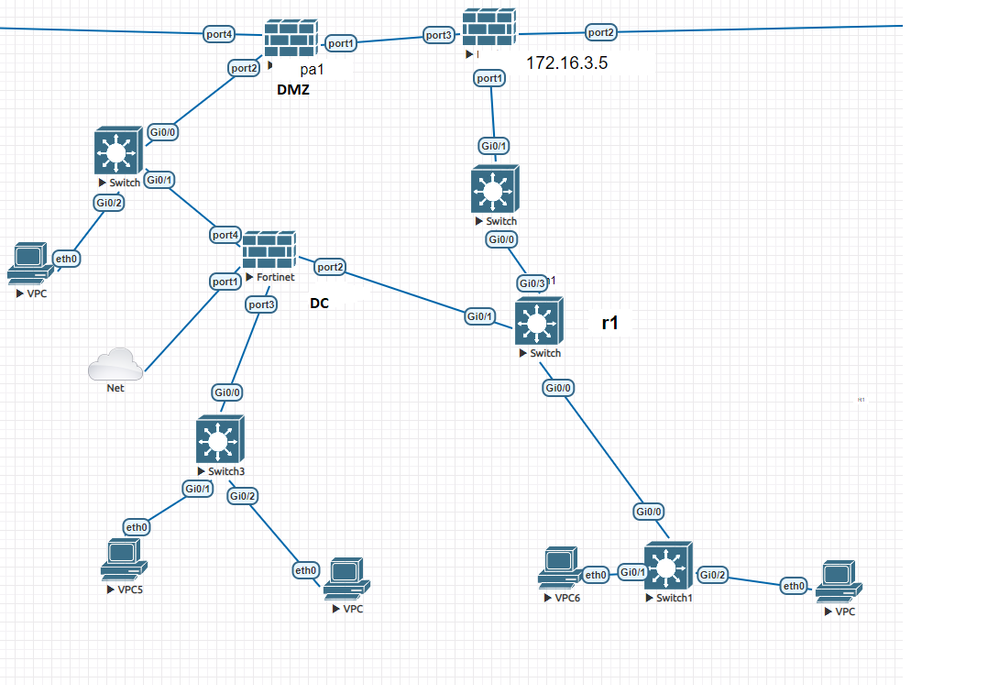
I have a design flaw . I am trying to test dual dmz . dmz server the gateway is on the dmz firewall .
If the server in dmz wants to send data to dc server it has to go back through the same switch
How to avoid this ?
And also, please point out pros and cons for the below design
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-18-2021 10:50 PM
Your diagram isn't incredibly well labelled, at least to my eyes. I don't see where you have a dual DMZ configured, nor do I honestly fully understand your question.
@simsim wrote:If the server in dmz wants to send data to dc server it has to go back through the same switch
How to avoid this ?
Why do you think this is a problem that needs to be avoided. Ideally your DMZ wouldn't be allowed to access resources in your DC, but in the event this is needed I would have the traffic separated through different physical switches, or have the DMZ isolated to it's own VRF on any shared switches.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-18-2021 11:23 PM - edited 12-20-2021 09:05 AM
Hi @BPry
I have updated the diagram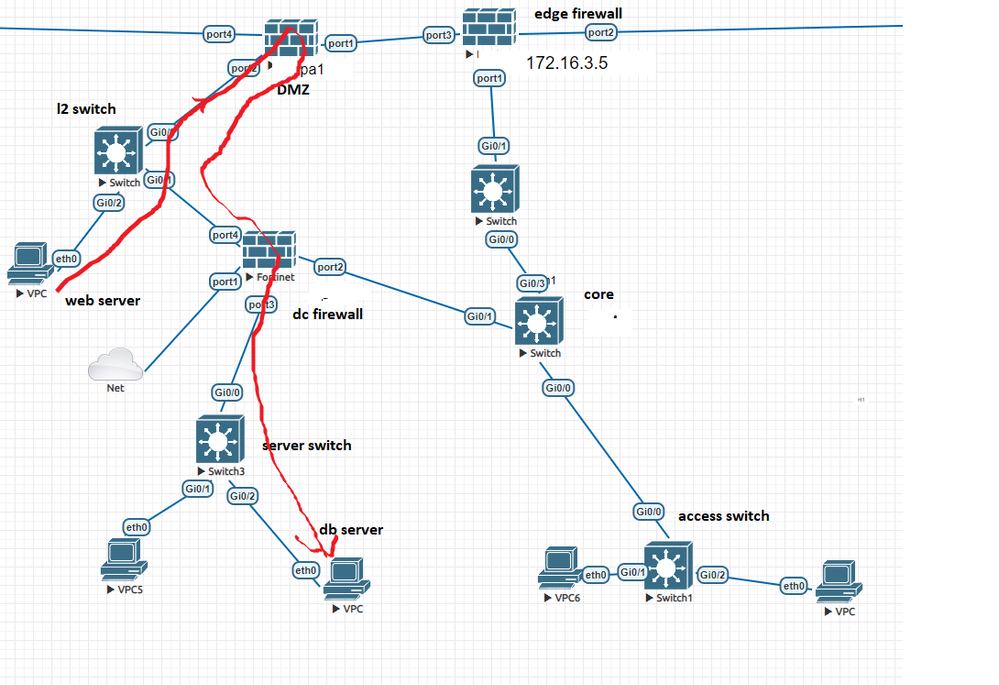
I don't see where you have a dual DMZ configured, nor do I honestly fully understand your question.
I meand dual firewall dmz ,I want to ask the above design is ok ?
Ideally your DMZ wouldn't be allowed to access resources in your DC,
what if a web server wants to talk to a DB server inside
but in the event this is needed I would have the traffic separated through different physical switches, or have the DMZ isolated to it's own VRF on any shared switches.
Please provide a rough diagram
Thanks for your support
Hi @BPry
It would be great if you can reply
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-20-2021 01:50 PM
Hello,
A DMZ is just a vlan that is anchored at the firewall. Using two different vendors, no longer makes sense to me in the modern world, especially with PaloAlto. I would simplify the diagram and get rid of the Fortinet firewall. Also make sure all traffic to/from the DMZ serer goes through the palo alto and gets inspected.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-20-2021 05:58 PM - edited 12-20-2021 05:59 PM
Hi @OtakarKlier and @BPry
Can I make a DMZ zone in the dc firewall?
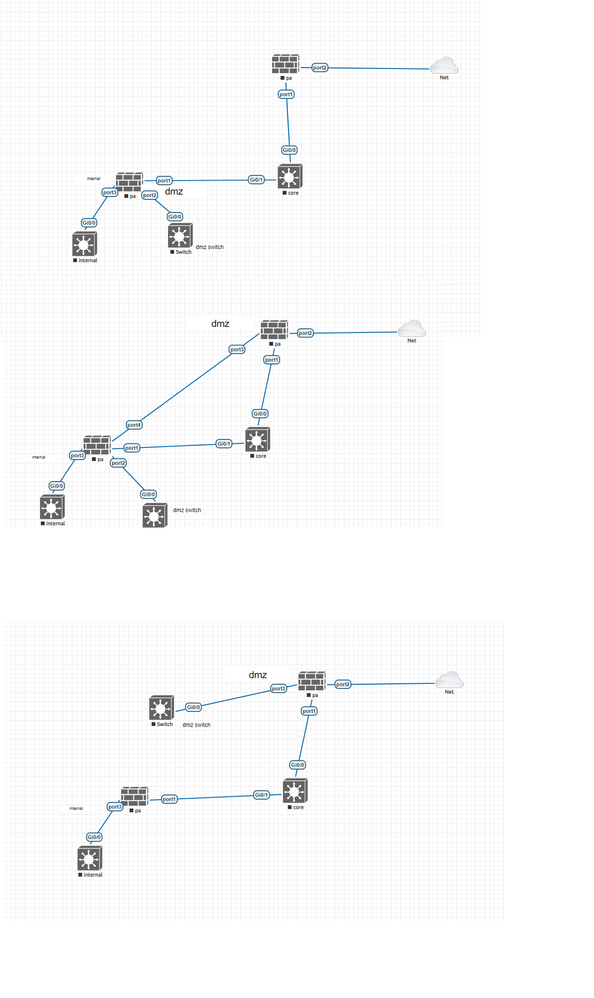
In the above diagram which one is good .My purpose is i will keep all web server in dmz and the server has t ocommunicate internal vlan and ldap .Please suggest
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-21-2021 01:37 PM
Hello,
I've always been a fan of keeping things simple. There are a few things to keep in mind when architecting networks, some of these are where are the systems that require a NAT from outside to inside (if at all) and what function do all the devices perform. You have a device called 'core' yet in the second diagram, you have a way to bypass it? Depending on its overall function, I would either go with the first or third diagram. I would also let the PAN's handel the routing and anchor the vlans so that the traffic can be inspected and monitored.
Hope that makes sense.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-21-2021 06:54 PM
Hi @OtakarKlier
"you have a device called 'core' yet in the second diagram, you have a way to bypass it? Depending on its overall function"
That is my core device for routing and edge switches are connected. Inter VLAN routing is happening on core
What does it mean by anchor the vlan ?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-22-2021 08:43 AM
Hello,
Meaning the vlan IP for routing etc is on the firewall and the switch is just layer 2 for that particular vlan.
Regards,
- 4955 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Need help on this XSOAR Weird behavior on preprocessing scripts in General Topics
- XSIAM API pagination in Cortex XSIAM Discussions
- Fortigate Correlation rules thread in Cortex XSIAM Discussions
- Address Group and Tag limitations in General Topics
- Best practices for Palo Alto security policy when destination IP/FQDN is dynamic or unknown in Next-Generation Firewall Discussions