- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IKE and IPsec Encryption and Authentication Parameters for Site-to-site IPsec VPN
- LIVEcommunity
- Discussions
- General Topics
- IKE and IPsec Encryption and Authentication Parameters for Site-to-site IPsec VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-20-2021 05:44 PM - edited 02-20-2021 05:53 PM
I was configuring a Site-to-site IPsec VPN and I was having a hard time matching my Encryption and Authentication parameters. The remote end device is Huawei Eudemon 1000E and my local device is PA-800. I have finished the configuration both sides by picking the closed parameters(I suppose) which I presume would work to get the tunnel up and running. Unfortunately, Its not up and running yet and my prime suspicion would be the IPsec parameters not matching on each of the peers.
I have details here below:
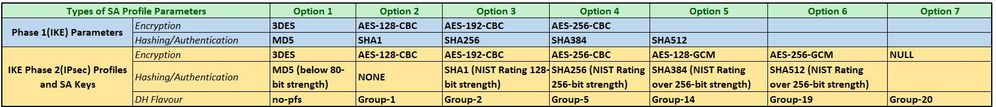
Supported parameters on my local PA800 are:
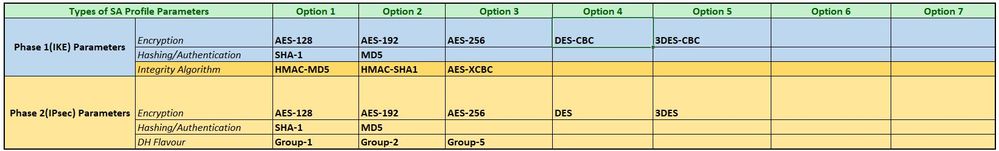
And on the remote Huawei Firewall Device, the supported parameters are:
- For Phase-1, the closest and the strongest possible IKE Encryption algorithm that is present on both sides would be the AES-256 which is AES-256-CBC on my side and a mere AES-256 on the remote side. Will these two work fine together where each configured on their respective end or I will be having a problem here?
- In a similar case for Phase-2 Encryption, the closest and the strongest possible Encryption algorithms that is present on both sides would be the AES-256 which is AES-256-CBC/AES-256-GCM on my side and again a bloody plain AES-256 on the remote side. So will these two work fine together where each configured on their respective end or I will be having another problem here too?
- Based on your view on #1 and #2, what option is the best and viable way to proceed?
- On the Remote end of Huawei Eudemon, there is a Choice Integrity algorithm option which I am not clear about on how to proceed with? What recommendation do you have for me here?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2021 02:15 PM
Huawei doesn't really appear to have clear information which algorithms they support
1. And 2. should work if huawei implemented cbc as default. 3. You'll need to pick something other than xcbc as that's not supported on the Palo
To troubleshoot this, try initiating the connection from the huawei while running these commands on the Palo:
reaper@PA-VM2> debug ike gateway GW1 on debug
Debugging for IKE gateway GW1 is enabled (debug).
IKE gateway debug level:
GW1 2 debug
reaper@PA-VM2> debug ike tunnel Tunnel1 on debug
Debugging for IPSec tunnel Tunnel1 is enabled (debug).
IKE gateway debug level:
GW1 2 debug
IPSec tunnel debug level:
Tunnel1 2 debug
reaper@PA-VM2> tail follow yes mp-log ikemgr.logPANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-22-2021 02:15 PM
Huawei doesn't really appear to have clear information which algorithms they support
1. And 2. should work if huawei implemented cbc as default. 3. You'll need to pick something other than xcbc as that's not supported on the Palo
To troubleshoot this, try initiating the connection from the huawei while running these commands on the Palo:
reaper@PA-VM2> debug ike gateway GW1 on debug
Debugging for IKE gateway GW1 is enabled (debug).
IKE gateway debug level:
GW1 2 debug
reaper@PA-VM2> debug ike tunnel Tunnel1 on debug
Debugging for IPSec tunnel Tunnel1 is enabled (debug).
IKE gateway debug level:
GW1 2 debug
IPSec tunnel debug level:
Tunnel1 2 debug
reaper@PA-VM2> tail follow yes mp-log ikemgr.logPANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-28-2021 01:49 AM
@reaper You have accurately put it there and I just got it working successfully yesterday with not specific type stated will automatically meaning as CBC. Thank you for sharing your knowledge and wishing all the best!
Next challenge will be DHCP from the Remote Site via the Tunnel to the AD and DHCP server that is situated in the HQ. Drop me any link of a related topic if you got one. Thank you again!
- 1 accepted solution
- 6923 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- Azure Active Directory users - Incorrect padding in Cortex XSOAR Discussions
- Global Device/Setup Authentication Settings vs Device/Setup/Authentication Profile in General Topics
- Problems with SentinelOne V2 Integration - 401 in Cortex XSOAR Discussions
- Cortex XDR PoC Lab ft. CVE-2021-3560 in Cortex XDR Discussions