- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Jumpcloud RADIUS Auth failure
- LIVEcommunity
- Discussions
- General Topics
- Jumpcloud RADIUS Auth failure
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-26-2019 05:00 AM
Hi,
I have configured a RADIUS profile to use a "Directory as a service" provider (JumpCloud) for authentication, I have tested this with LDAP and everything seems to work as intended but when I configure the Radius profiles and test authentication via the cli I get the following response
Failed EAPOL auth (-1). Response for user: "bob" from RADIUS server: "self signed certificate in certificate chain; unknown CA"
I have been through and installed the certificate chains for JumpCloud as well as the certificate they provide so I am not sure I understand exaclty what this certificate error is refering to.
Any help will be appreciated.
/M
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2019 11:21 AM
Looks like I have managed to solve this issue, appears I had the wrond certificate chains loaded.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2019 11:21 AM
Looks like I have managed to solve this issue, appears I had the wrond certificate chains loaded.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-15-2019 04:38 PM
Hi @Marc_T,
Please can you share more light on how you resolved this issue?
I'm having the same issue as well. However, this time, it is Palo Alto RADIUS authentication via Aruba ClearPass, using EAP-MSCHAPv2 as Authentication protocol. My experience in SSL certificates is not so fantastic.
Actually, an SSL certificate was installed on the RADIUS server (ClearPass) which I exported and imported into the Palo Alto firewall.
Patiently waiting for your feedback.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-23-2020 07:58 AM - edited 02-23-2020 07:59 AM
Hi @Marc_T ,
I'm having this exact same issue with JumpCloud RADIUS auth; any chance you could let us know what resolved the issue for you? I'v tried every possible version of certificates/certificate chains that I can think of, but still no luck. Would really like to know how you resolved this.
Thanks!
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-23-2020 11:44 AM
Hi @nolansuess ,
Its been a while since I used this so I hope all the information I have still configured in my firewall is still valid.
There are the certificates I had to install and then create a certificate profile from:
You should be able to download any updated certs from here: https://support.jumpcloud.com/support/s/article/jumpcloud-radius-certificate-for-eap-ttls-client-dep...
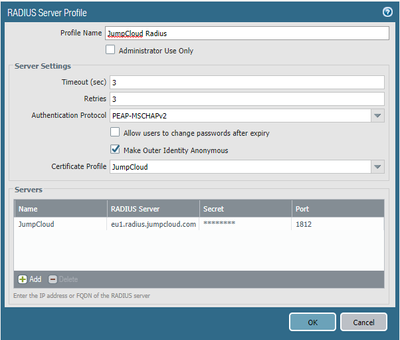
Once I had all that configured I created the Radius profile as per usual
Let me know if this helps
/M
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-03-2020 06:03 AM
Did you also add both the GD CA and GD Inter to the certificate profile (which is assigned to the radius server profile)
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-03-2020 01:58 PM
So... I was also getting the "self signed certificate in certificate chain; unknown CA" issues after following;
I just installed all the other ROOT and INTER CAs off the below repo, I then added them all to my certificate profile and I was able to auth with peap-mschapv2.. So I think the doc is out of date. I have raised a ticket with JC and once I have the definitive list I will post.
Heres the repo;
https://certs.godaddy.com/repository
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-10-2020 03:29 AM
Hi @Marc_T,
Is this setup still working for you for Jumpcloud?
If I enable "Make Outer Identity Anonymous" radius authentication does not work.
Works fine if I disable this option. Setup is the same other than this.
/Jo Christian
- 1 accepted solution
- 11268 Views
- 7 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Several client authentication in a Gateway in GlobalProtect Discussions
- SAML Jumpcloud HA Implementation in General Topics
- Radius Authentication Failure: Timeout in General Topics
- Radius authentication with Clearpass for Firewall Webgui in General Topics
- Authentication Sequence not working in General Topics