- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
L2 Networking - some help needed
- LIVEcommunity
- Discussions
- General Topics
- Re: L2 Networking - some help needed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
L2 Networking - some help needed
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-29-2012 03:24 PM
Hi
I just started with PA and try to get my head around the "slightly" different concept of how my PA50 does things.
I have currently the following "playground":
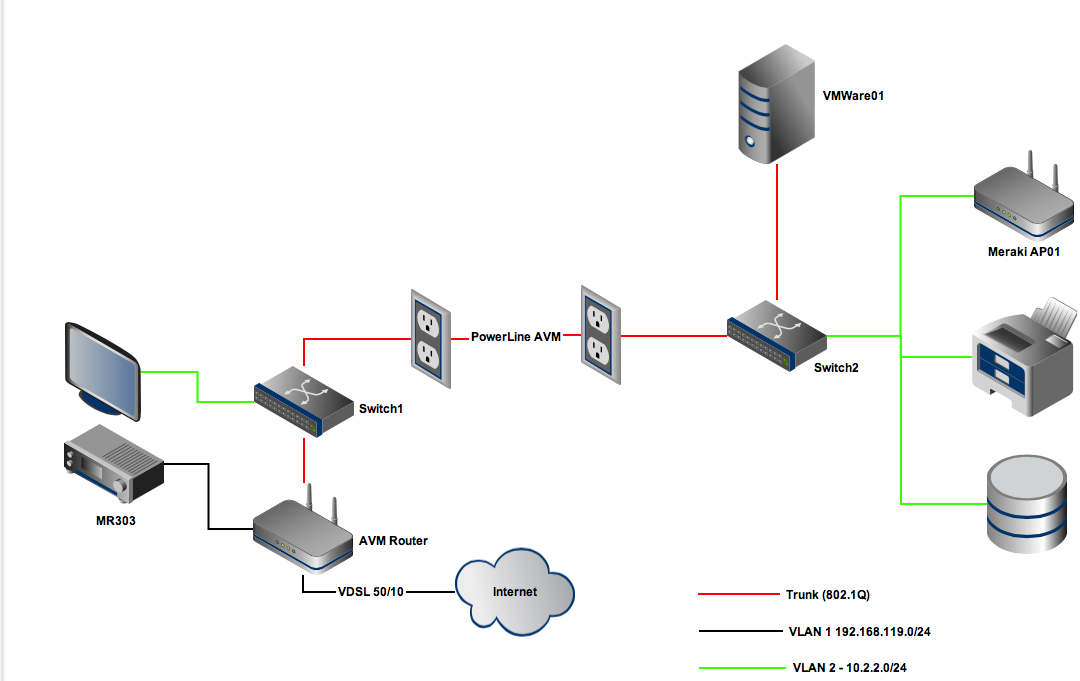
my PA500 sits between the two switches.
There is a Router running on the VMWare Machine which has one interface in VLAN1 (untagged) and one in VLAN2 (tagged). This router is the default gateway for the VLAN2 / 10.2.2.0/32 network (Vyatta router with routing on a stick)
First I started with a vWire setup and everything was fine but the TV couldn't talk to the NAS, which was obvious, as it comes in via E1/1 which was in the Untrust Zone.
So i thought I opt for a L2 config. I setup E1/3 and E1/4 as L2 Interfaces and created 1/3.2 and 1/4.2 as sub interfaces. I created two zones: Untrust (E1/3 and E1/4) and Trust (E1/3.2 and E1/4.2) and setup my policies accordingly (basically a allow any any in both directions).
Problem is that I can't get anything through the firewall at all. Before I dig deeper I just wanted to ask whether such a setup (having both "trust" and "untrust" on both sides of the firewall ) is a valid setup at all.
As said, running above setup without the PA works fine (so I believe my general tagging setup is ok) and using the PA with a vWire runs also fine (apart from the TV problem mentioned above).
Thanks a lot in advance
PS: this is not a live network and I'd probably never build such a network but I want to test anything possible.
- Labels:
-
Networking
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-29-2012 05:50 PM
Depends on what the purpose is with your PA - is it to protect some internal resource like your vmware box or is it to protect the whole lan from Internet, or a combination (or for that matter to try different setups to better learn how the PA device functions)?
I assume your AVM router have a built in VDSL modem and I also assume that MR303 is an IPTV device.
I would then set this up as:
1) Set your AVM router into bridgemode (if possible - this is to get as much performance as possible), but let it still be a QoS device between IPTV stuff vs Internet stuff from your ISP.
2) MR303 is connected to your AVM router on the IPTV interface (so it can speak to your ISP's IPTV boxes). This is by assuming that your MR303 doesnt need to speak to your NAS or such.
3) Your PA box is then connected to your AVM router - use L3 interfaces (in your drawing the PA would sit between AVM router and Switch1).
4) Now if you want to isolate your vmware box from the rest of your lan you can still use 802.1Q for the vmware box otherwise you can just use untagged interfaces in your LAN.
If you use two or more VLANs (either all are 802.1Q or you leave one as untagged and tag the others) on the inside your PA box will act as a firewall between the zones. Where your TV who is on the same VLAN as your NAS wont need to pass your PA (the flow would be like in your drawing: TV <-> (untagged vlan2)Switch1(tagged vlan2) <-> Powerline AVM <-> (tagged vlan2)Switch2(untagged vlan2) <-> NAS).
The term "zone" can bee seen as "interface" with the difference (if I remember correctly - standard disclaimer :P) that a zone can contain one or many physical interfaces along with one or many vlan interfaces at the same time. With the limit that an interface, subinterface or vlan can only be part of a single zone at a time. So in your case Untagged E1/3 can be zoneX while Tagged E1/3.2 can be zoneY (but Untagged E1/3 cannot be zoneX and ZoneY at the same time).
Personally I prefer to not use "trust" or "untrust" as names of zones but rather which network is actually available. Such as "WAN", "LAN", "Internet", "Server", "VMware" and so on.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-30-2012 01:06 AM
Hi
thanks for your quick response.
right now it's purpose is only to better learn how exactly it functions.
You're right with your assumptions, but I can't get the AVM to be the modem only, as it handles also some VoIP Stuff which is turned off when I bring it to bridge mode.
My Idea was to consider everything in VLAN1 (untagged) as the "Internet" or untrust and everything in VLAN2 (tagged) as internal LAN (trust).
So I started with this L2 setup and defined the tagged sub interfaces as LAN and the untagged as Internet. If I understand it correctly, I don't need to setup VLAN Interfaces (Network -> Interfaces -> VLAN), as those are for L3 only.
<entry name="ethernet1/3">
<link-speed>auto</link-speed>
<link-duplex>auto</link-duplex>
<link-state>auto</link-state>
<layer2>
<units>
<entry name="ethernet1/3.2">
<tag>2</tag>
</entry>
</units>
</layer2>
</entry>
<entry name="ethernet1/4">
<link-speed>auto</link-speed>
<link-duplex>auto</link-duplex>
<link-state>auto</link-state>
<layer2>
<units>
<entry name="ethernet1/4.2">
<tag>2</tag>
</entry>
</units>
</layer2>
</entry>
</ethernet>
<vlan>
<entry name="VLAN Bridge">
<virtual-interface>
<l3-forwarding>no</l3-forwarding>
</virtual-interface>
<interface>
<member>ethernet1/3.2</member>
<member>ethernet1/4.2</member>
</interface>
</entry>
</vlan>
<zone>
<entry name="vWireTrust">
<network>
<virtual-wire>
<member>ethernet1/2</member>
</virtual-wire>
</network>
</entry>
<entry name="vWireUntrust">
<network>
<virtual-wire>
<member>ethernet1/1</member>
</virtual-wire>
</network>
</entry>
<entry name="L2Untrust">
<network>
<layer2>
<member>ethernet1/3</member>
<member>ethernet1/4</member>
</layer2>
</network>
</entry>
<entry name="VLAN2">
<network>
<layer2>
<member>ethernet1/3.2</member>
<member>ethernet1/4.2</member>
</layer2>
</network>
</entry>
</zone>
If I now go ahead and define a allow any any rule from zone "VLAN2" to Zone "L2Untrust", I should be able to get it working, correct?
Andre
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-30-2012 03:12 AM
I have never done any setup like that so unfortunately I dont know.
Usually when one use vwire you do this without any additional configuration of the interfaces (like L3, VLAN etc) - the idea is that you can take a TP (or fiber) cable and split it in half and put your PA device as MITM no matter which traffic it contains.
I mean in your case it would be vwire on E1/3 and E1/4 (or whichever 2 interfaces you wish to use) and thats it and the VLAN-handling would be taken care of the AVM router (like (untagged)VLAN1:192.168.0.254/24, (tagged)VLAN2:192.168.1.254/24). But at the same time I agree with you - it would be healthy if one can assign the various vlans flowing through to different zones.
Hopefully one of these documents might help you to get an idea on how the PA device can be used:
Edit: As a sidenote here is another great document regarding PA functionality and how to configure stuff (not the question of this thread but I assume its the next thing once the VLAN handling is sorted out 😉
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-30-2012 07:51 AM
Hi
thanks a lot for the docs, will have a look into it.
Agreed, vWire would do it but in this case (as described in my first post), it doesn't help, as vWire can only make it's decision based on interface (trust / untrust) and the TV (which should be trust) is therefore untrust ....
Andre
- 3409 Views
- 4 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Insights - Filter out Guest Wifi or other such networks in Strata Cloud Manager
- Need help on this XSOAR Weird behavior on preprocessing scripts in Cortex XSOAR Discussions
- Need help uninstalling Cortex XDR in General Topics
- New Certifications: Next Gen Firewall Engineer and Network Security Professional in General Topics
- Vulnerability assessment report in Cortex XDR Discussions



