- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Mac OS userID using Syslog and Web Server Authentication
- LIVEcommunity
- Discussions
- General Topics
- Mac OS userID using Syslog and Web Server Authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Mac OS userID using Syslog and Web Server Authentication
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-30-2021 07:10 PM - edited 12-31-2021 04:51 PM
I ran through the process of creating a solution to get userID consistently for MacOS machines via the syslog feature in the User Agent. The goal was to authenticate to a domain webserver using cert-based auth, and to have the web server provide the IP and user information via syslog to the user agent.
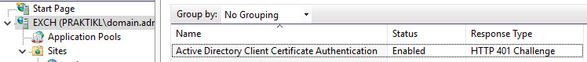
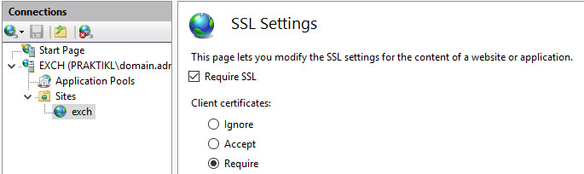
I set up a general webserver site “exch” (AD-joined server, requiring SSL, enabled “Active Directory Client Certificate Authentication and disabled other authentication methods)
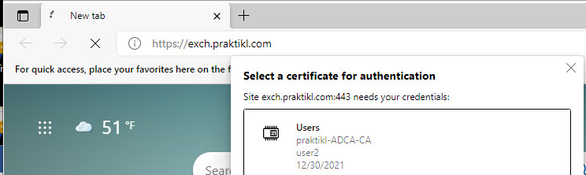
Tested cert auth from client machine using “PRAKTIKL\user2”
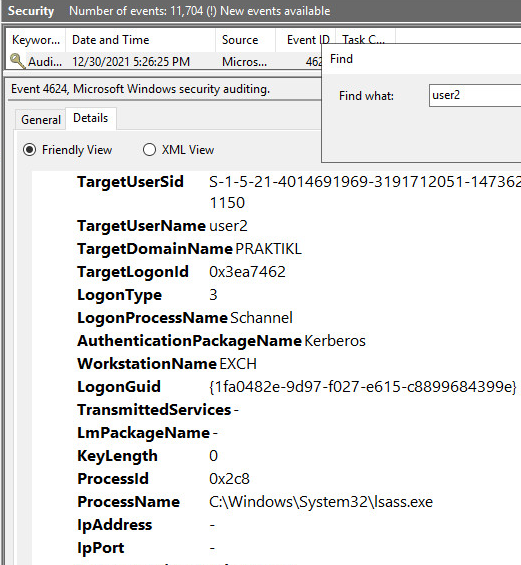
Checking the event security logs, you see the user logon event (4624), but the IP is not recorded. I found that when the provider is “schannel” (this seems to always be the case with cert-based auth to webservers in an AD domain), the IP is never logged.
Best info I could find on this is: “This is because the service handles authentication on behalf of the client”. If I use username/password, I get the IP, although via a different service. Unfortunately, this affects OWA too, where logging in via the app uses logon process “kerberos” and provides the IP, but logging in via OWA with cert-based authentication uses “schannel” and does not provide the IP. This is also reflected in the user agent where app login logs userID, and OWA login does not.
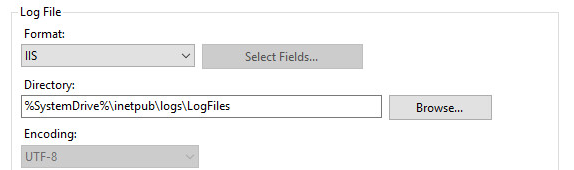
IP and user information is stored in the IIS logs. You just need to verify logging is enabled for the site. I chose the IIS format: csv.
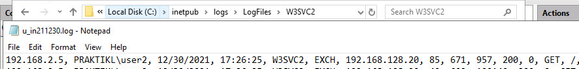
If you browse to the log file location you can verify the logs contain the right information by opening the latest log and searching for a user, in my case “user2”. Looking at the example, the source IP is logged first, followed by the user in down-level logon format.
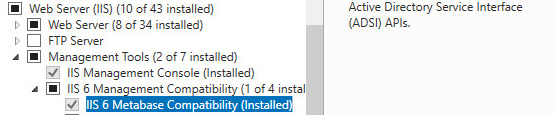
To parse these log files and get any sort of useful format, I found that LogParser 2.2 from Microsoft https://www.microsoft.com/en-us/download/details.aspx?id=24659 was the best SIMPLE/FREE option. Also, if you make sure that “IIS 6 Metabase Compatibility” is installed, this will simplify using LogParser where you can reference the IIS logs for a site using only <SITENAME>.
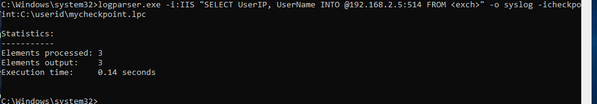
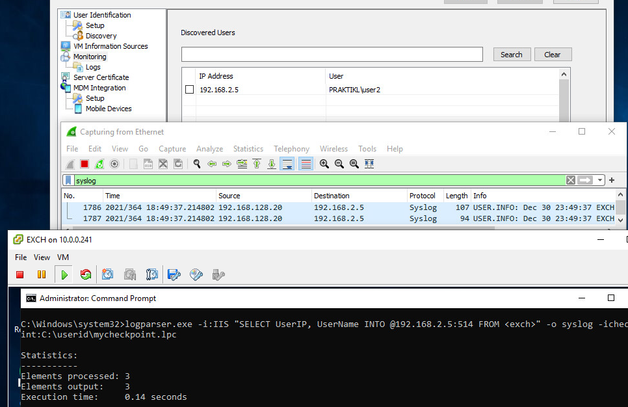
LogParser opens in command prompt, and you can query the IIS logs to test extracting the IP and username, in my case “user2”. Selecting on “UserIP” and “UserName” provides only the output needed (IP and username).
NOTE: If you run command (logparser “SELECT * FROM <SITENAME>”), it will show the heading and all fields you can use to select on.
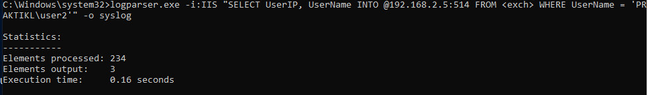
You can test sending this output to the user agent using the output switch for syslog and “INTO” redirection to @IP:port. “-o syslog” and “INTO @192.168.2.5:514”
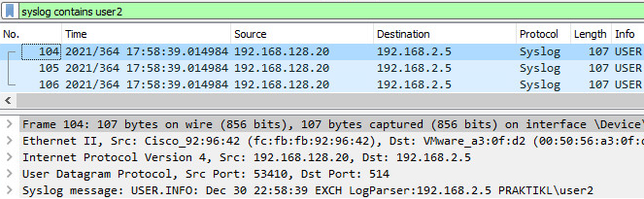
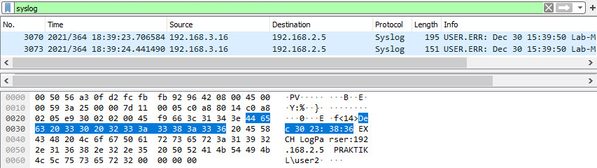
Log messages received on user agent machine
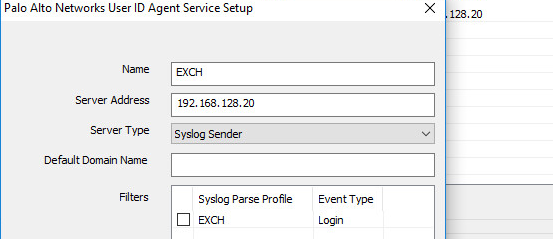
Then you can configure the user agent to accept logs from web server and configure regex to match on log information to extract the IP and user.
The string to match on is “EXCH LogParser:192.168.2.5 PRAKTIKL\user2” per the pcap above.
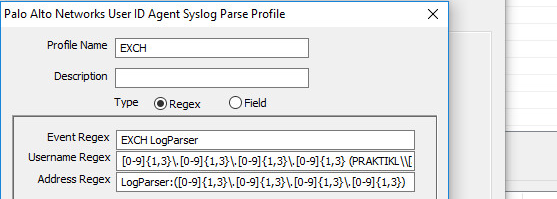
For the user agent syslog regex configuration, you can have a specific match, or you can lead with some data and surround the relevant portions in “()”. For example, there are three fields:
Event Regex: “EXCH LogParser” – nothing special here
Username Regex:
Beginning Delimiter User Matching Data
[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3} (PRAKTIKL\\[a-zA-Z0-9]*\.?[a-zA-Z0-9]*)
- needed to match on a delimiter to trigger the start of the username. In this case, I matched on the preceding IP and space before matching on the username. “+” is not available for use in the Palo user agent, somewhat limited w/other options too.
Address Regex:
Delimiter IP Matching Data
LogParser: ([0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3})
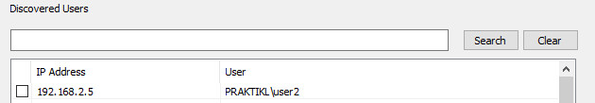
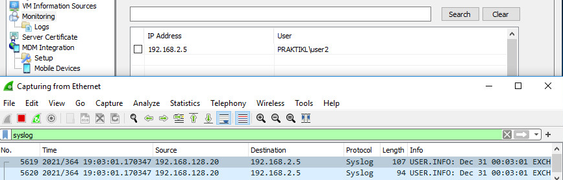
If you log into the webserver again from the client: in my case “user2”, and run the LogParser command again, you’ll have the user ID info logged in the user agent.
LogParser ran again after site logon
Syslog received on user agent
User ID logged in agent
The full LogParser string is:
Logparser.exe -i:IIS “SELECT UserIP, UserName INTO @192.168.2.5:514 FROM <exch>” -o syslog -icheckpoint:C:\userid\mycheckpoint.lpc
- Logparser.exe (moved to system32 folder, no need for path)
- -i:IIS (just tells LogParser that format of logs is IIS)
- SELECT UserIP, UserName INTO @192.168.2.5:514 FROM <exch> (SQL query)
- -o syslog (output to syslog format/syslog server)
- -icheckpoint:C\userid\mycheckpoing.lpc (used by LogParser to follow logs, only trigger on and send new logs
Adding the -icheckpoint switch allows LogParser to track the parsing location in the log file using a special file ".lpc" (in my case, C\userid\mycheckpoing.lpc), so it will not resend entries that were previously received and sent.
For example, if I clear the user agent cache and wireshark, and I run the command again, nothing will be sent.
If I authenticate to the site again and run the LogParser command, there will be a new entry.
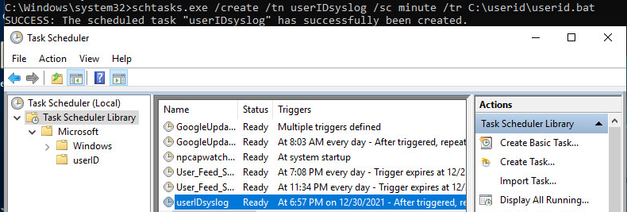
Once the command and user agent are ironed out, you can automate using “schtasks.exe” (Task Scheduler) and a batch file. See below: I just added the same command to a txt file and saved as a .bat
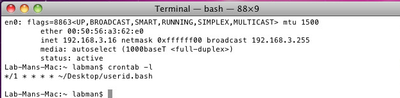
Then, I ran “schtasks.exe /create /tn userIDsyslog /sc minute /tr C:\userid\userid.bat” to get the task going.
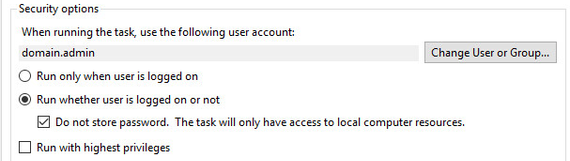
I also found that it will be set to “Run only when user is logged on” under “Security options”, and it will fail initially. I changed it to “Run whether user is logged on or not” and “Do not store password. The task will only have access to local computer resources.”. Once I did that, it started working.
New logs received by user agent
At this point, you can just set up this logging option on frequently used web servers and/or set up a special-purpose web server, use Desktop shortcuts on Mac clients, and tell users if they’re not able to get to stuff, to open the link, authenticate, and they’ll be good to go in 1-3 mins.
If you want to automate it so that machines are always authenticating without user interaction, that is possible too.
If you take a user cert, break it up into cert and key, and call it in a curl action, you can add this to a cron job and have it checking in continuously.
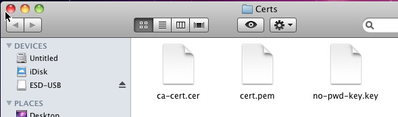
Below, I took the user cert for “PRAKTIKL\domain.admin” and broke it up using openssl
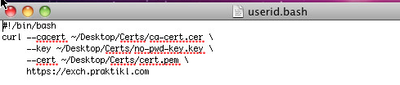
Next, I made a .bash file identifying the location of the CA cert, the private key, and the cert, with a curl to https://exch.praktikl.com
Then, I used Crontab to run this file every minute. (NOTE: IP 192.168.3.16)
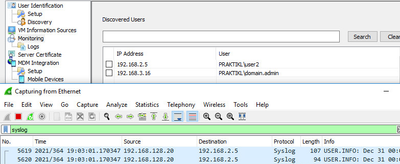
Checking back on the user agent, I verified that “PRAKTIKL\domain.admin” was logged to IP 192.168.3.16.
That’s it, hope it helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-03-2022 03:59 PM
Hey @jbworley ,
This is awesome! Thank you for sharing it
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2022 02:24 PM
I had the same problem, therefore I came here for a way to collect userID consistently for MacOS machines via syslog, you presented it properly with illustrations, and I got it without becoming tired, Thank you for sharing this useful knowledge. This page is also shared on my Twitter account.
https://shareitpro.com/ https://tweakbox-online.net/ https://acmarket-apk.info/
- 3897 Views
- 2 replies
- 2 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Assistance with LDAP Authentication in General Topics
- Push Cortex XDR datasets/logs to dedicated syslog server in Cortex XDR Discussions
- Sectigo Root CA Trusted Store Request in General Topics
- Why do the same Windows Server data collected using XDRC and WEC agents show different statuses in the following fields? in Cortex XSIAM Discussions
- Global Protect Connectivity Issue in GlobalProtect Discussions