- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
multiple VLANs on one security zone - possible?
- LIVEcommunity
- Discussions
- General Topics
- multiple VLANs on one security zone - possible?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
multiple VLANs on one security zone - possible?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-16-2013 01:12 AM
Hi
I need your help with one (probably simple for You problem).
I have PA200 but I have only one "free" security zone and one phisical interfece free.
I need to create 4 local networks (as a subinterfaces/VLAN) that every one has their own adresses, dhcp server, NAT policy to their own IP.
Intervlan traffic shouldn't be allowed.
Is it possible? Until now I do always one security zone per one network ...
With regards
Slawek
- Labels:
-
Configuration
-
Networking
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2013 03:25 AM
admin@PA-200> show routing route
VIRTUAL ROUTER: rtr_ign (id 3)
==========
destination nexthop metric flags age interface next-AS
0.0.0.0/0 XXX.XXX.XXX.XXX 10 A S ethernet1/1
[..........]
192.168.3.0/24 192.168.3.1 0 A C ethernet1/3.250
192.168.3.1/32 0.0.0.0 0 A H
192.168.210.0/24 192.168.210.1 0 A C ethernet1/3.1
192.168.210.1/32 0.0.0.0 0 A H
192.168.230.0/24 192.168.230.1 0 A C ethernet1/3.2
192.168.230.1/32 0.0.0.0 0 A H
192.168.240.0/24 192.168.240.1 0 A C ethernet1/3.3
192.168.240.1/32 0.0.0.0 0 A H
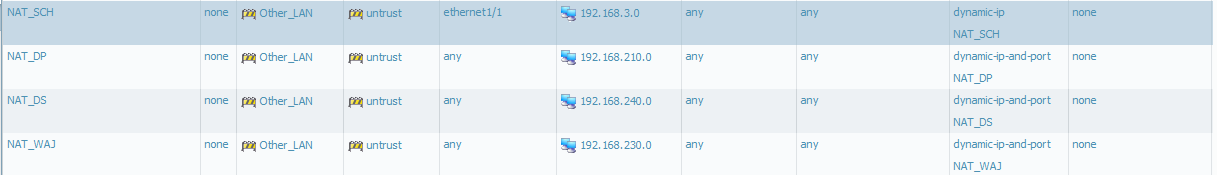
>Can try to include the Interface in the Source NAT rule instead of the translated address.
I dont understnd correctly - I think
I change to:
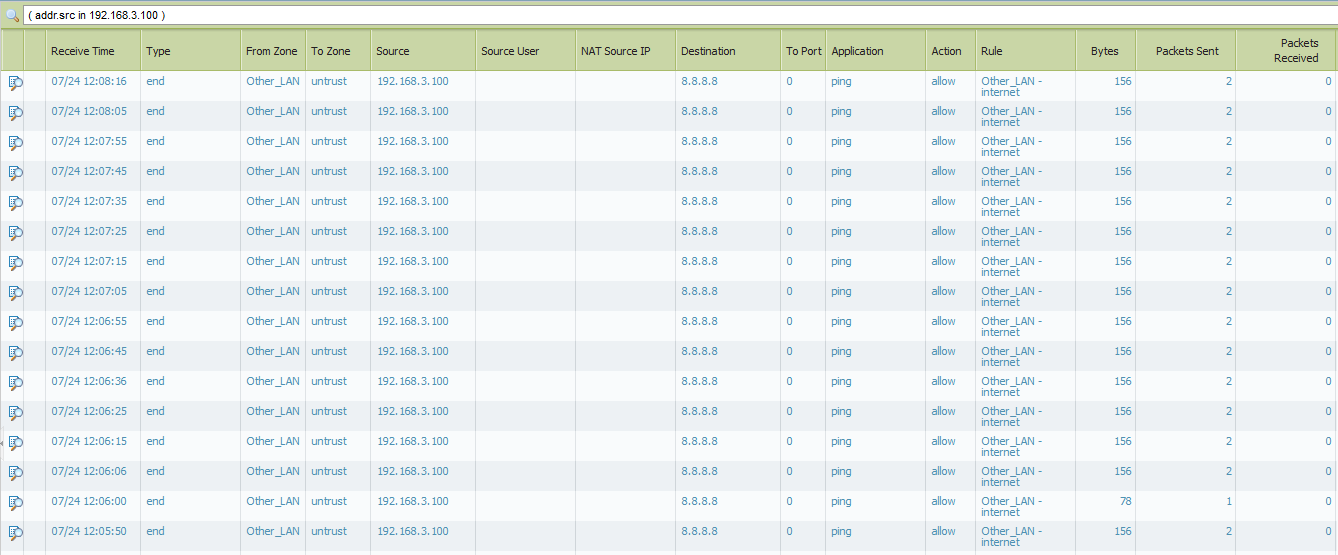
But i still can't ping from 192.168.3.x to 8.8.8.8
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2013 04:01 AM
Finally I found my mistake ...
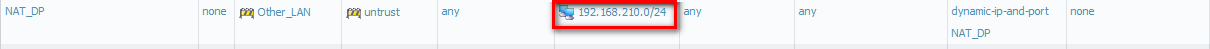
After I add "/0" I can reach internet from every LAN (even CP is working too).
So I have to isolate traffic of every network - please give me advice hot to do that.
I wouldn't create a lot of policies like:
192.168.3.0/24 to 192.168.210.0/24 deny
192.168.3.0/24 to 192.168.230.0/24 deny
192.168.3.0/24 to 192.168.240.0/24 deny
and again
192.168.210.0/24 to 192.168.30.0/24 deny
.
.
.
.
.
Is it possible to do it in other way?
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2013 06:15 AM
If you are really trying to isolate the traffic from each subnet, you should really be creating separate zones for each one. You would just add the new zones to the outbound NAT rule and NAT policy.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-24-2013 11:29 PM
I know ... but I have PA200 and I have only one security zone free ... so I have to make configuration as good as possible in this situation.
This 4 networks will have couple computers, but must be separataed.
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-25-2013 06:11 AM
Sorry - I forgot the limitation on a 200 is 10 Zones. Unless you want to move the vlans to a layer 3 switch and use ACLs or don't enable forwarding, I think the only viable alternative would be to create the deny policies on the PAN.
- 9891 Views
- 19 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Problem with downloading PAN OS in General Topics
- New articles about how to create signatures without or with AI (ChatGPT/OpenAI) in Custom Signatures
- Excel downloads being blocked in General Topics
- Security Policy with Destination Criteria in Strata Cloud Manager
- WTH is process 'touch' and hwy is it showing zombie? in General Topics



