- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Newbie looking for some guidance
- LIVEcommunity
- Discussions
- General Topics
- Re: Newbie looking for some guidance
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Newbie looking for some guidance
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-01-2023 06:21 AM
Hello everyone. I am new to Palo Alto firewalls. We have bought many new PA-440's and I am having trouble with my very first installation.
I have a site that is currently using a TP-Link AX1500 router.
Very simple setup.... ISPmodem----WANportOfAX1500/LANportOfAX1500----Clients.
I have tried, without success, to mimic the setup of the AX1500 and replace it with the PA-440. I have the PA-440 acting as a DHCP server. My clients get IP addresses, and then can ping the PA-440. They cannot ping anything on the Internet. From the PA-440 command line, I also cannot ping anything on the Internet (ping host 8.8.8.8 for example).
I know this post leaves many questions, but is there a guide on a very basic setup like this? I am sure I am missing something small but have been unable to put my finger on it.
Thank you -- Walter
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-01-2023 06:32 AM - edited 02-01-2023 06:32 AM
"ping host 8.8.8.8" sends ping requests out from Palo mgmt interface.
For this to work mgmt interface needs to be connected, NAT and security policy need to be in place.
Do you see those sessions under "Monitor > Traffic"?
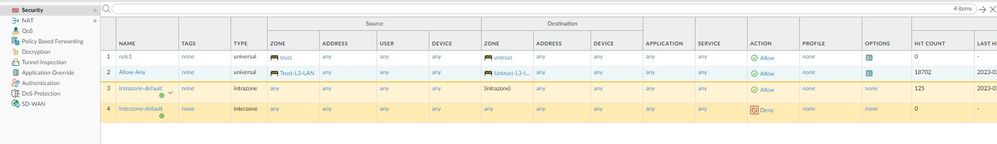
By default "interzone-default" and "intrazone-default" rules don't log so it is suggested to override them and check "Log at session end" on Actions tab.
You can also try "ping source 1.2.3.4 host 8.8.8.8" (replace 1.2.3.4 with your WAN IP).
In this case ping goes out from WAN interface. NAT is not needed and by default "intrazone-default" rule will permit this traffic.
If you share output of your results we can help you get them connected.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2023 01:32 PM
Thank you very much for responding.
I am now working on the bench in my office. I have two Windows laptops, one Windows PC, and the Palo.
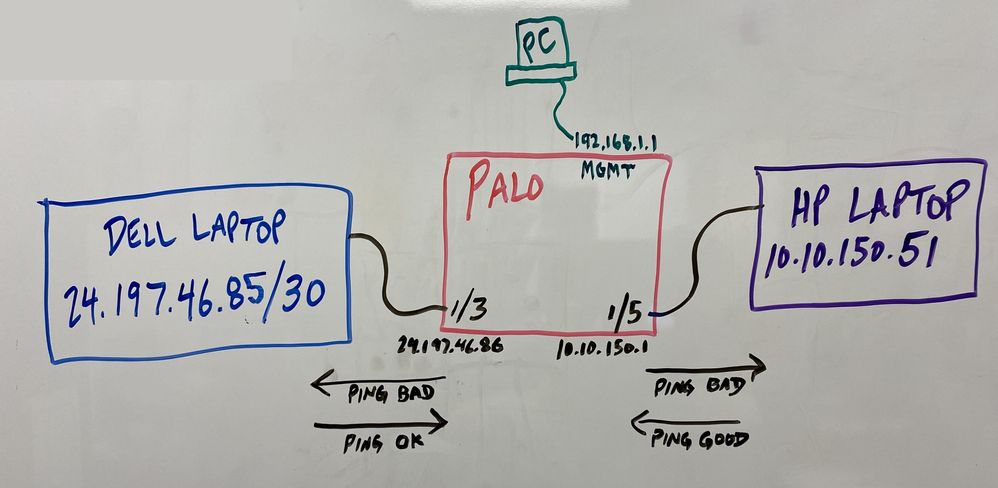
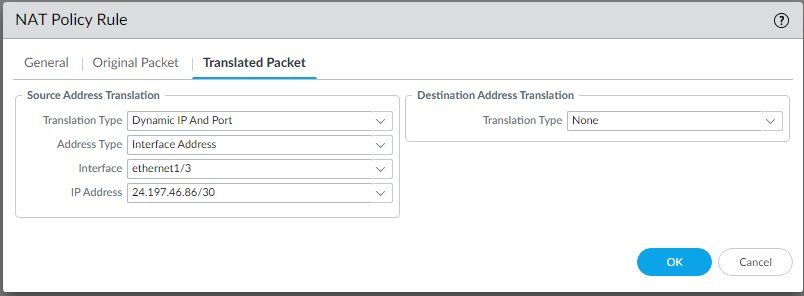
I have attached a picture of the connections.
- The Palo can successfully ping either of it's own interfaces (10.10.150.1 or 24.197.46.86).
- Palo cannot ping either laptop from the command line.
- Dell laptop can ping 24.197.46.86, but not 10.10.150.1.
- HP laptop can ping 10.10.150.1, but not 24.197.46.86.
I am sure I am missing something fundamental.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-02-2023 06:07 PM - edited 02-02-2023 06:09 PM
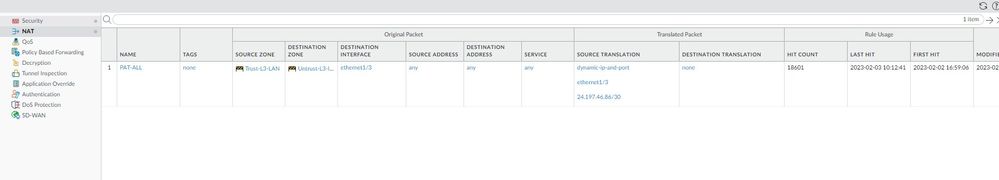
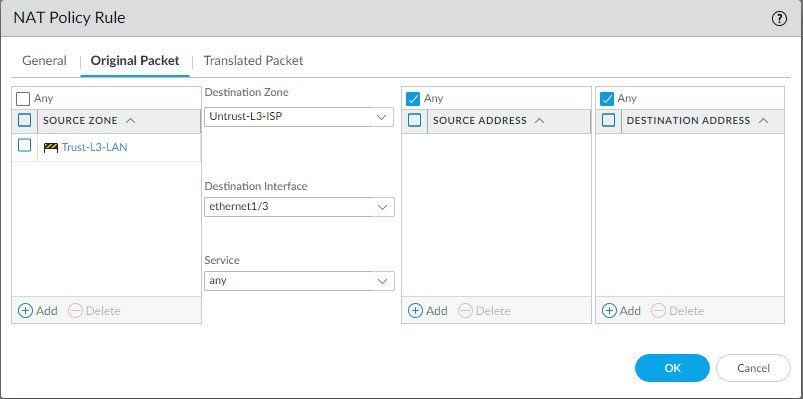
Can you share screenshot of security and nat policy?
Have you permitted incoming ping in laptops (or disabled firewall)?
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-03-2023 06:28 AM
I have the Windows firewall disabled on both laptops. Just to make sure of pingability, I changed one laptop to match the subnet of the other laptop, cross-connected them via Ethernet, and they were able to ping each other.
I am attaching 7 screenshots. Thanks again for your help.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-03-2023 06:40 AM
Those 2 commands don't work?
ping source 24.197.46.86 host 24.197.46.85
ping source 10.10.150.1 host 10.10.150.51
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-03-2023 07:06 AM - edited 02-03-2023 07:07 AM
Yes, both of those commands do work. I apologize... I thought "ping host 10.10.150.1" would work.
I get replies using both of these commands:
ping source 24.197.46.86 host 24.197.46.85
ping source 10.10.150.1 host 10.10.150.51
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-03-2023 07:30 AM - edited 02-03-2023 07:30 AM
If you don't specify source IP (like ping host 10.10.150.51) then ping requests go out from mgmt interface.
There is no interconnection inside firewall between mgmt port and dataplane port.
For mgmt port to have connectivity you need to connect fw internal interface and mgmt port into switch so they can see each other.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-03-2023 09:54 AM
You don't appear to be logging your interzone-default policy, for troubleshooting I'd enable that so you can ensure that the traffic is actually being processed properly and isn't getting dropped. Couple things I would look at:
- Traffic Logs - Do you see this traffic in your current traffic logs at all? If you have it recorded in the logs as being allowed, make sure that you've actually verified via the detailed log view that things are routing properly and going out the proper interface. If you don't have records prior to enabling the interzone-default logging, this traffic wasn't matching your rules and getting dropped.
- Routing - Kinda covered this above, but make sure that your traffic is actually routing properly via your traffic logs.
- 7114 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GloablProtect + Explicit Proxy blocks WSL traffic. in GlobalProtect Discussions
- Conditional Advertisement / BGP Failover with Dual ISP — How to Remove ISP1 Routes on Internet Loss? in Next-Generation Firewall Discussions
- Problem with downloading PAN OS in General Topics
- web file blocking in Next-Generation Firewall Discussions
- Inquiry Regarding Publishing Custom Third-Party IOC Feed via EDL Hosting Service in Next-Generation Firewall Discussions