- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Palo Alto Proxy IDs Bidirectional?
- LIVEcommunity
- Discussions
- General Topics
- Re: Palo Alto Proxy IDs Bidirectional?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2023 11:03 AM
Hi everyone,
I am a bit confused about proxy IDs when it comes to tunnel negotiation. Lets say I have a tunnel I am building with a vendor. My encryption domain will be 192.168.1.0/24 and my vendor will have 192.168.2.0/24. So lets also say the vendor has an ASA so I will add this proxy id to my phase 2 config: Source 192.168.1.0/24 Destination 192.168.2.0/24. Here is my question: Lets say I need the vendor to also be able to send traffic to me as well as receive my traffic. Is my proxy id bi-directional for the purpose of the vendor being able to initiate/negotiate the tunnel? OR do I need another proxy id as such: Source 192.168.2.0/24 Destination 192.168.1.0/24
Thanks for the help.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2023 11:19 AM
ProxyID is not source/destination but local/remote instead.
It means they are bi-directional.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2023 12:05 PM
Palo don't care but other end is most likely policy based firewall that routes traffic based on those ProxyID's / encryption domains so most likely yes you need ProxyID for every pair of subnets.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-24-2023 11:19 AM
ProxyID is not source/destination but local/remote instead.
It means they are bi-directional.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2023 10:40 AM
Thank you. One additional question:
Lets say I have the following proxyIDs built:
ProxyID1 LOCAL 192.168.2.0/24 REMOTE 10.1.1.0/24
ProxyID2 LOCAL 192.168.10.0/24 REMOTE 10.50.1.0/24
Here is my question, for LOCAL 192.168.10.0 to be able to pass traffic back and forth with REMOTE 10.1.1.0, do I need a separate proxy ID such as this: LOCAL 192.168.10.0 REMOTE 10.1.1.0 ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-26-2023 12:05 PM
Palo don't care but other end is most likely policy based firewall that routes traffic based on those ProxyID's / encryption domains so most likely yes you need ProxyID for every pair of subnets.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2023 08:06 AM
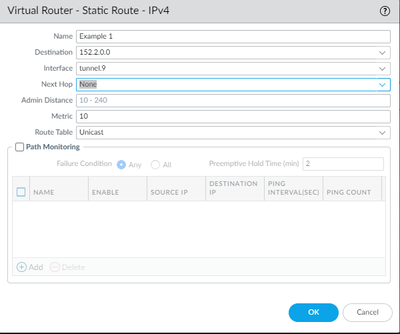
Hi again Raido, thanks for all of your help. I ran across something else I am questioning in my PA440 config. When there is a NAT rule created for an ipsec tunnel for example: Source address 192.168.1.0/24 Destination address 152.2.0.0/16 Source translation 10.77.120.212 and bidirectional is yes. I only need a static route for the PRE-NAT ip address correct?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2023 08:43 AM
Palo virtual router will route based on POST-NAT destination IP.
In your example you don't seem to change destination IP but source IP so destination PRE-NAT and POST-NAT IPs are the same (unless I misunderstand your requirement to also NAT destination IP).
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2023 08:58 AM
I am creating a source nat rule and setting it to bi-directional so the destination nat rule is auto created by the firewall. This means when I view nat rules from command line i see this:
"Example1; index: 86" {
nat-type ipv4;
from inside;
source 192.168.1.0;
to l2lvpn;
to-interface ;
destination 152.2.0.0/16;
service 0:any/any/any;
translate-to "src: 10.77.120.212 (static-ip) (pool idx: 24)";
terminal no;
}
"Example1; index: 87" {
nat-type ipv4;
from any;
source any;
to l2lvpn;
to-interface ;
destination 10.77.120.212;
service 0:any/any/any;
translate-to "dst: 192.168.1.0";
terminal no;
}
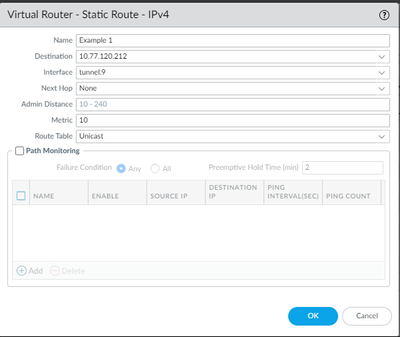
My question is, when I create my static routes for the tunnel, do I need a static route for 152.2.0.0 or for my source nat address 10.77.120.212
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2023 09:28 AM
I usually prefer not to use bi-directional NAT rules and create 2 rules myself for better control due how bi-directional option messes up zones.
Your example shows that one way source zone is "inside" and destination zone is "l2lvpn"
Other way source zone is "any" and destination zone is "l2lvpn"
But if you don't have 10.77.120.212 in your routing table then destination zone should be "outside" instead for nat policy to match for traffic initiated from peer side.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2023 09:54 AM
Which one of these would be correct given my nat rule example? Sorry, I do not do enough networking to be well versed with it =(
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2023 09:56 AM
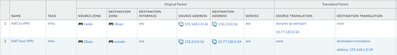
Can you share screenshot of your NAT policy as well but I would say that destination needs to be
152.2.0.0/16
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2023 11:20 AM
Do you need to use 10.77.120.212 only or can you use /24 subnet like example below?
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-30-2023 11:22 AM
I can use subnet like your example.
- 2 accepted solutions
- 5185 Views
- 12 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- PA-415-5G not working with fresh T-Mobile SIM in General Topics
- GloablProtect + Explicit Proxy blocks WSL traffic. in GlobalProtect Discussions
- Palo Alto Unable to Download Software Updates in Next-Generation Firewall Discussions